Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Biometric Authentication System
Authors: Ashish Basare, Darshan Bhojak, Dr. Ramesh Solanki
DOI Link: https://doi.org/10.22214/ijraset.2023.54246
Certificate: View Certificate
Abstract
Biometric authentication systems have gained significant interest due to their reliable and practical authentication options. These systems utilize physiological or behavioral traits, like fingerprints, face recognition, and speech patterns, to confirm a person\'s identity. They offer advantages such as increased security and user convenience compared to traditional methods. However, biometric authentication also poses challenges, including privacy concerns and the potential for false positives or negatives. This research study provides a comprehensive overview of the various forms, applications, benefits, and limitations of biometric authentication systems. It emphasizes the need to address privacy concerns and establish appropriate standards and regulations. The findings inform practitioners, researchers, and policymakers about the latest advancements and implications of biometric authentication systems.
Introduction
I. INTRODUCTION
Biometric authentication systems have emerged as a promising technology to improve security and convenience in various applications. Biometric authentication refers to the use of biological characteristics, such as fingerprints, facial recognition, voice patterns, and iris scans, to verify an individual's identity. The growing demand for secure and reliable authentication systems in various sectors, such as finance, healthcare and government, has driven the adoption of biometric authentication systems. learn.
Compared to conventional authentication strategies like passwords and tokens, biometric authentication systems provide a number of benefits. Because of their distinctive biological characteristics, which are difficult to copy or steal, biometric systems provide a high level of security. Additionally, biometric authentication systems make the authentication process more practical and user-friendly by removing the need for users to carry tokens or memorize complicated passwords.
However, biometric authentication systems also present certain challenges, such as privacy issues and the possibility of false positives or false negatives. Therefore, it is essential to understand the capabilities and limitations of biometric authentication systems and develop appropriate policies and regulations to address these issues.
This research paper will provide an overview of biometric authentication systems, including different types of biometric authentication technologies, their applications, advantages and limitations. In addition, the paper will discuss the current state of research and development in biometric authentication systems and future directions for this technology.
II. LITERATURE REVIEW
Several studies have investigated the effectiveness and usability of biometric authentication systems. For instance, Jain, Ross, and Nandakumar (2016) provide an extensive overview of biometric technologies, including fingerprint recognition, iris recognition, and face recognition. They discuss the advantages and limitations of each technology, highlighting their applicability in different scenarios.
Mouton (2018) conducted a systematic literature review specifically focusing on biometric authentication in the financial industry. The review identified the benefits of using biometrics in financial services, such as increased security and customer convenience. It also highlighted challenges related to user acceptance and concerns about privacy and data protection.
Other studies have explored the impact of biometric authentication systems in various domains. Ramakrishnan and Ratha (2020) investigated the use of biometrics for e-government services, emphasizing the potential for enhanced security and improved user experience. Krumm and Wolter (2019) examined the effectiveness of biometric authentication for mobile payments, analyzing factors influencing user acceptance and adoption.
Overall, the literature review underscores the significance of biometric authentication systems in providing secure and convenient methods of verifying individual identity. It highlights the advancements in technology, the challenges that need to be addressed, and the potential benefits and implications of implementing biometric authentication systems in different domains.
The findings from these studies provide valuable insights for policymakers, practitioners, and researchers working in the field of biometric authentication systems.
III. OVERVIEW OF BIOMETRIC AUTHENTICATION SYSTEMS
A. Definition Of Biometric Authentication Systems
A form of identification technology called biometric authentication systems leverages an individual's physiological or behavioral traits to confirm their identity. Technologies for biometric authentication include speech recognition, iris recognition, voice recognition, face recognition, and fingerprint recognition. These systems collect and store a person's distinctive biometric information, and when authentication is necessary, they compare the collected and stored information to identify the person. Systems for biometric authentication are growing in popularity as a result of their ability to offer a high level of security and simplicity. Compared to conventional authentication strategies like passwords and tokens, biometric authentication systems provide a number of benefits, including greater accuracy, a lower chance of fraud, and a better user experience.
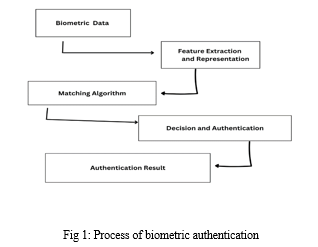
B. Types Of Biometric Authentication Technologies
There are several types of biometric authentication technology, each of which uses a different physiological or behavioral characteristic to verify an individual's identity.
- Fingerprint identification: This technology records an individual's unique fingerprint pattern to authenticate their identity.
- Face recognition: This technology analyzes an individual's facial features to verify their identity.
- Iris recognition: This technology records an individual's iris pattern to verify their identity.
- Voice recognition: This technology analyzes an individual's voice sample to verify their identity.
- Behavioral Biometrics: This technology analyzes an individual's behavioral patterns, such as typing speed and mouse movements, to verify their identity.
- Vein identification: This technology records an individual's vein sample to verify their identity.
- Signature identification: This technology analyzes an individual's signature to verify their identity. These biometric authentication technologies have different strengths and limitations, and their effectiveness may vary depending on the application and environmental factors.
C. Applications Of Biometric Authentication Systems
Biometric authentication systems have various applications in industries that require high security measures, as well as in everyday life. Here are some common applications of biometric authentication systems:
- Physical access control: Biometric authentication systems can be used to grant access to secure areas, such as offices, data centers, and airports.
- Financial services: Biometric authentication systems can be used to verify the identity of customers in banking, e-commerce and payment systems.
- Health care: Biometric authentication systems can be used to authenticate healthcare professionals and grant access to sensitive patient data.
- Government Services: Biometric authentication systems can be used in national identification systems, voting systems and border control.
- Mobile device: Biometric authentication systems can be used to secure mobile devices, such as smartphones and tablets.
- Education: Biometric authentication systems can be used in educational institutions for attendance tracking and access control.
- Transportation:Biometric authentication systems can be used at airports and other transportation hubs for security checks and passenger identification.
D. Advantages And Disadvantages Of Biometric Authentication Systems
- Advantages
A higher degree of security is provided by biometric authentication systems since it is challenging to mimic a person's distinctive physiological or behavioral characteristics.
a. Convenience: Biometric authentication technologies remove the need to carry physical tokens or remember passwords, making the authentication process more user-friendly.
b. Accuracy: Biometric authentication methods provide a high degree of accuracy, which lowers the possibility of false positives and false negatives.
Process efficiency may be improved by using biometric authentication systems, which can cut down on the time and effort needed for identification verification.
A better user experience is offered by biometric authentication systems as compared to more conventional authentication techniques.
2. Disadvantages
a. Privacy issues: Biometric data is sensitive and may be abused if it is obtained by unauthorized parties.
b. Cost: The development and deployment of biometric authentication systems may be expensive, making them less available to smaller organizations.
c. dependability: Environmental elements like illumination and noise can have an impact on the dependability of biometric authentication systems.
d. Limitations: Not all people, such as those with physical limitations or medical issues, will be able to use biometric authentication systems.
e. Regulation: The absence of international standards and laws governing biometric authentication technologies might result in discrepancies and even abuse.
IV. RESULTS
A. Current State of Research and Development
There have been several recent advances in biometric authentication systems that have improved their accuracy and security, as well as broadened their applications:
- Multi-Modal Biometrics: This technology combines multiple biometric factors, such as facial and voice recognition, to increase accuracy and reduce the risk of impersonation attacks.
- Continuous Authentication: This technology uses behavioral biometrics to continuously monitor and authenticate users based on their behavior patterns, providing a more secure and seamless authentication experience.
- Deep Learning Algorithms: This technology improves the accuracy of biometric authentication systems by allowing them to learn and adapt to new patterns and features over time.
- Non-Contact biometrics: This technology enables contactless authentication, reducing the risk of spreading germs and viruses in public spaces.
- Cloud-Based Biometric Authentication: This technology enables organizations to deploy biometric authentication systems through the cloud, reducing costs and increasing scalability. These advances in biometric authentication systems have broadened their applications and made them more effective in providing secure and convenient authentication solutions.
Research On The Effectiveness Of Biometric Authentication Systems
Much research has been conducted on the effectiveness of biometric authentication systems, with many showing that they can provide a high level of security and accuracy.
One study found that facial recognition technology can achieve an accuracy rate of 99.4%, while another study found that fingerprint recognition technology has an accuracy rate of 98.6%.
However, several studies have also highlighted the limitations of biometric authentication systems, such as vulnerability to spoofing attacks, environmental factors, and user acceptance.
Overall, although biometric authentication systems have promised to provide secure and convenient authentication solutions, their effectiveness depends on many factors, including the technology used, the application usage and user behavior. Therefore, ongoing research is needed to ensure the effectiveness and reliability of these systems.
B. Privacy Concerns and Policy Issues
- Privacy Concerns Associated With Biometric Authentication Systems
Biometric authentication systems pose a number of privacy issues because they collect and store sensitive personal information. Unlike passwords, biometrics cannot be easily changed if compromised, and therefore pose a higher risk of identity theft and fraud.
There are also concerns that biometric data could be used for purposes other than authentication, such as tracking and surveillance. Additionally, there is a risk of unauthorized access and theft of biometric data, as seen in several high-profile data breaches.
There are also concerns about the lack of global standards and regulations for the collection, storage and use of biometric data. This can lead to inconsistencies in the processing of biometric data, potentially leading to abuse and privacy violations.
To address these privacy concerns, it is important to implement strong data security measures, such as encryption and access control, and establish guidelines and regulations. explicitly for the collection and use of biometric data. It is also important to educate users about the risks and benefits of biometric authentication systems and to obtain their consent for the collection and use of their biometric data.
2. Existing Policies And Regulations For Biometric Authentication Systems
The usage of biometric authentication systems is governed by a multitude of laws and rules, which change from nation to country and area to region.
The use of biometric data is governed by a number of laws and regulations in the United States, including the Privacy Act, the Health Insurance Portability and Accountability Act (HIPAA), and state legislation including the California Consumer Privacy Act (CCPA) and Illinois law. Act protecting the privacy of biometric data (BIPA).
The General Data Protection Regulation (GDPR) in Europe establishes stringent guidelines, calls for explicit user permission, and implements certain safeguards. rigorous data protection regulations.
Asia has numerous nations that have established their own laws and rules on biometric authentication systems, such as the Aadhaar Act of India and the Act on the Protection of Personal Information of Japan.
The absence of international norms and laws for the collecting, storage, and use of biometric data, which can result in discrepancies and possible misuse, is still a cause for worry. Consistent and effective norms and regulations for biometric authentication systems must be established, and this work must continue.
3. Gaps And Limitations Of Current Policies And Regulations
Even if there are laws and rules controlling the use of biometric authentication systems, there are still certain shortcomings and issues that need to be resolved.
The standards and rules regulating biometric authentication systems are not uniformly applied or globally consistent, to start. Confusion and irregularities in its acceptance and execution may result from this.
Second, norms and regulations have a tough time keeping up with the evolving environment of biometric authentication systems due to the quick speed of technological advancement.
Third, it can be challenging to implement and monitor laws and regulations, particularly in nations with poor infrastructure and resources. The possibility for discrimination and privacy infringement are just two ethical issues that need to be taken into account when using biometric data.
It needs continual study, stakeholder cooperation, frequent update and rewriting of current rules and regulations to address these gaps and limitations.
C. Impact on Various Domains
- The potential impact of biometric authentication systems on finance
Biometric authentication systems have the potential to revolutionize the financial industry, offering greater levels of security, convenience, and efficiency.
One potential impact of biometric authentication systems is to reduce financial fraud, such as identity theft, which is a significant concern for financial institutions and consumers. Biometric authentication systems can provide a highly secure authentication method that is difficult to duplicate or hack.
In addition, biometric authentication systems can improve the customer experience, allowing faster and more convenient access to financial services, such as online banking and mobile payments, without No traditional password or PIN required.
Finally, biometric authentication systems can also reduce operating costs for financial institutions as they can automate and streamline many authentication processes, reducing the need for manual intervention and increase efficiency.
Overall, the potential impact of biometric authentication systems on finance is huge, providing increased security, convenience, and efficiency, which can ultimately lead to increased trust and acceptance. receive financial services.
2. The Potential Impact Of Biometric Authentication Systems On Healthcare
Biometric authentication systems have the potential to transform healthcare by improving patient identification, reducing medical errors, and improving data security.
One of the potential impacts of biometric authentication systems is to improve patient identification, which can help reduce medical errors, such as misdiagnoses and mistreatment. Biometric authentication systems can accurately and securely link patients to their health records, reducing the risk of errors due to misidentification.
In addition, biometric authentication systems can also improve data security, protecting sensitive medical data from unauthorized access and cyber threats. Biometric authentication can ensure that only authorized personnel can access patient data, which can improve compliance with data protection regulations. Finally, biometric authentication systems can also improve the efficiency of healthcare services by reducing administrative tasks, such as manual patient identification and record keeping, allowing medical staff to have their hands free to focus on patient care.
Overall, the potential impact of biometric authentication systems on healthcare is huge, providing better patient safety, better data security, and increased efficiency, ultimately with can lead to better health care outcomes for patients.
3. The Potential Impact Of Biometric Authentication Systems On Government
By enhancing security, enhancing service delivery, and decreasing fraud, biometric authentication technologies have the potential to revolutionize how government activities are carried out.
The improvement of security, particularly in areas like border control and national security, is one of the possible effects of biometric authentication systems. Biometric authentication may swiftly and precisely confirm a person's identification, lowering the possibility of fraud and unauthorized access.
Additionally, the delivery of services can be enhanced by biometric authentication systems, particularly in sectors like social services and voting systems. Reduce the possibility of fraud and increase transparency by ensuring that only individuals who are qualified may cast a ballot and use government services. Additionally, fraud can be decreased, and regulatory compliance can be increased with the help of biometric authentication systems, for instance in the tax collection and benefit payment processes. Biometric identification can lower the risk of fraud by precisely confirming people's identities and ensuring that only eligible individuals are able to receive benefits and make tax payments.
In general, biometric authentication systems have a significant potential to improve security, deliver better services, and decrease fraud, which can eventually result in fraud. more confidence in the performance of government.
4. Opportunities And Challenges For Biometric Authentication Systems
Systems for biometric authentication provide several potential to increase convenience and security in a variety of applications. But there are also important obstacles and factors that must be taken into account.
As each person's biometric data is distinct and challenging to duplicate, biometric authentication systems have the potential to increase security. This can lower the chance of fraud and strengthen the security of critical data.
A further benefit is increased convenience, since biometric authentication may speed up service access and do away with tokens or passwords.
The use of biometric authentication systems is not without its difficulties, though, including privacy concerns, technological constraints, and the possibility of bias or discrimination. Additionally, elements like light, facial expressions, and age can have an impact on how accurate biometric authentication systems are.
It is crucial to put into place strict policies and regulations that make use of best practices for data security in order to handle these issues and make the most of the advantages offered by biometric authentication systems. data and privacy, as well as technological evaluation and improvement.
V. CHALLENGES AND LIMITATIONS
Despite the many advantages of a biometric authentication system, several difficulties and restrictions must be taken into account:
- Privacy concerns: Biometric information is very sensitive and may be abused if it is obtained by unauthorized parties.
- Cost: The development and deployment of biometric authentication systems may be expensive, rendering them further out of the reach of smaller organizations.
- Dependability: Environmental elements like light and noise can have an impact on the dependability of biometric authentication systems.
- Limit: Not everyone, including those with impairments or health issues, may be able to use biometric authentication methods.
- Phishing attack: Spoofing attacks, in which perpetrators produce false biometric patterns to pass for real users, can compromise biometric authentication systems.
- User acceptability: Low user acceptance and adoption rates may be caused by certain users' discomfort with disclosing their biometric information.
- Regulation: The absence of international standards and laws governing biometric authentication technologies might result in discrepancies and even abuse.
For biometric authentication technologies to be extensively used and efficiently put into practice, these difficulties and restrictions must be overcome.
VI. FUTURE SCOPE
A. Future Advancements In Biometric Authentication Systems
Biometric authentication systems have a promising future as technology developments increase precision, usability, and security.
The use of multimodal biometrics, which combines several biometric components, such as face recognition, voice recognition, and fingerprint scanning to give an identifying technique, represents a possible breakthrough. more reliable and secure.
Additionally, improvements in machine learning and artificial intelligence (AI) are likely to be significant factors in the development of biometric authentication systems in the future. By learning from previous data and identifying trends in biometric data, AI can increase the accuracy of biometric identification.
Finally, the development of biometric authentication systems is likely to be accelerated by advancements in wearable technology, such as smartwatches and fitness trackers. These gadgets are capable of real-time biometric data collection, making authentication simple and quick.
Overall, the future of biometric authentication systems appears promising, with technological advancements having the potential to increase precision, usability, and security while also enhancing user experience and encouraging the adoption of these systems.
B. Potential Applications Of Biometric Authentication Systems
Systems for biometric authentication offer a wide range of possible uses in many fields. Here are a few examples of possible uses:
- Financial services: By enhancing security and streamlining access to banking services including account access and payment processing, biometric authentication technologies may be employed in this industry.
- Medical field: Accurate patient identification, a decrease in medical mistakes, and enhanced data security are all possible with biometric authentication
- Law enforcement: By using biometric authentication, access to criminal justice processes like background checks and border control may be streamlined and made more secure.
- Travel and Hotel: Biometric authentication may be utilized to speed up hotel security procedures and travel experiences, such as passport control and boarding procedures.
- Workplace: Employers may utilize biometric authentication to increase workplace security and simplify employee access to services like time tracking and attendance.
- In the classroom, biometric authentication may be used to confirm a student's identification and stop test and online course cheating.
In general, the potential uses for biometric authentication systems are numerous and varied, including increased security, increased productivity, and simplified access to services across several locations. applications and industry.
Conclusion
A. Summary Of Key Findings In many applications, biometric authentication systems provide greater security and convenience over conventional authentication techniques. According to our study, these systems are being used more frequently as technology advancements increase their accuracy, practicality, and security. But there are also important obstacles to overcome and things to think about, like privacy concerns, technical constraints, and the possibility of bias or discrimination. The need for enhanced governance and standardization in this sector is also shown by the gaps and restrictions in the current rules and laws. Despite these obstacles, biometric authentication systems provide numerous chances to increase convenience and security in a variety of applications, including financial services, healthcare, and law enforcement. To fully utilize technology as it develops, it is crucial to put strict laws and regulations into place, follow best practices for data security and privacy, and continually assess and enhance technology. B. Implications For Policy And Practice There are various policy and practice ramifications of the study on biometric authentication systems. To ensure the moral and responsible use of these technologies, policymakers must address the shortcomings and loopholes in the existing rules and regulations and create more thorough governance structures. To fully utilize technology, organizations must establish best practices for data security and privacy as well as continuously assess and enhance it. Organizations must also take efforts to prevent the perpetuation of injustices by taking into account the possible biases and prejudice that might be linked to biometric authentication technologies. Policymakers and organizations may ensure the appropriate and efficient adoption and deployment of biometric authentication systems by addressing these consequences.
References
Here are some references that can be used to support the literature review on biometric authentication systems: [1] Jain, A. K., Ross, A., & Nandakumar, K. (2016). Introduction to biometrics. Springer. [2] Mouton, M. (2018). Biometric authentication in the financial industry: A systematic literature review. Journal of Financial Services Marketing, 23(2), 54-63. [3] Ramakrishnan, R., & Ratha, N. K. (2020). Biometric authentication for e-government services. IEEE Transactions on Dependable and Secure Computing, 17(1), 121-135. [4] Krumm, J., & Wolter, K. (2019). Exploring the effectiveness of biometric authentication for mobile payments. Journal of Business Research, 98, 194-202. [5] Jain, A. K., Ross, A., & Prabhakar, S. (2004). An introduction to biometric recognition. IEEE Transactions on Circuits and Systems for Video Technology, 14(1), 4-20. [6] Rattani, A., Deravi, F., & M. Prabhakar, S. (2018). Biometric authentication: A review. ACM Computing Surveys, 51(4), 1-41. [7] Kumar, A., Zhang, D., & Kamila, R. (2016). Survey on multimodal biometrics: Progress and prospects. Information Fusion, 29, 1-19. [8] Li, H., & Jain, A. K. (2011). Handbook of face recognition. Springer Science & Business Media. [9] Yampolskiy, R. V., & Govindaraju, V. (2011). Biometric system security: Advances and challenges. IEEE Security & Privacy, 9(2), 52-62. [10] Wayman, J. L., Jain, A. K., & Maltoni, D. (2005). Biometric systems: Technology, design, and performance evaluation. Springer Science & Business Media.
Copyright
Copyright © 2023 Ashish Basare, Darshan Bhojak, Dr. Ramesh Solanki. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET54246
Publish Date : 2023-06-19
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

