Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- Copyright
A Blockchain-based Approach for Drug Traceability in Healthcare Supply Chain
Authors: Kiran Bhagwat , Pratibha Sudrik, Shraddha Pawar, Vishwanath Waghchaure, Prof. A. P. Suryavanshi
DOI Link: https://doi.org/10.22214/ijraset.2023.53120
Certificate: View Certificate
Abstract
The blockchain typically described as a decentralized system in which transactional or ancient statistics are recorded, stored, and maintained throughout a peer-to-peer community of personal computers referred to as nodes. Counterfeit drugs are one consequence of such limitations within existing supply chains, which not only has serious adverse impact on human health but also causes severe economic loss to the healthcare industry. Blockchain technology has gained tremendous attention, with an escalating hobby in a plethora of several applications like safe and relaxed healthcare records management. Similarly, blockchain is reforming the traditional healthcare practices to an extra reliable means, in phrases of powerful prognosis and treatment through safe and cosy facts sharing using SHA Hash Generation Algorithm. Within the future, blockchain will be an era that can probably assist in personalized, authentic, and at ease healthcare by means of merging the entire actual-time scientific information of a patient’s fitness and offering it in an up to date cosy healthcare setup. In this paper, we evaluation each the present and modern day trends inside the subject of healthcare with the aid of imposing blockchain as a model. We also talk the packages of blockchain, at the side of the demanding situations confronted and destiny views. The proposed system executed blockchain implementation in distributed computing surroundings and it gives the automated restoration of invalid chain by using Consensus and Mining Algorithm. In this system, we present a Custom blockchain-based approach leveraging smart contracts and decentralized off-chain storage for efficient product traceability in the healthcare supply chain. The smart contract guarantees data provenance, eliminates the need for intermediaries and provides a secure, immutable history of transactions to all stakeholders. We present the system architecture and detailed algorithms that govern the working principles of our proposed solution. We perform testing and validation, and present cost and security analysis of the system to evaluate its effectiveness to enhance traceability within pharmaceutical supply chains.
Introduction
I. INTRODUCTION
A blockchain system can be considered as a virtually incorruptible cryptographic database where critical medical information could be recorded. The system is maintained by a network of computers, that is accessible to anyone running the software. Blockchain operates as a pseudo-anonymous system that has still privacy issue since all transactions are exposed to the public, even though it is tamper-proof in the sense of data-integrity. The access control of heterogeneous patients’ healthcare records across multiple health institutions and devices needed to be carefully designed. Blockchain itself is not designed as the large-scale storage system. In the context healthcare, a decentralized storage solution would greatly complement the weakness of blockchain in the perspective. The blockchain network as a decentralized system is more resilient in that there is no singlepoint attack or failure compare to centralized systems. However, since all the bitcoin transactions are public and everybody has access, there already exist analytics tools that identify the participants in the network based on the transaction history. With popularity analytics, similarity or closeness among topics within large volume of data can be detected. Groups of items or topics can be system generated using closeness relationship formulation. As information flows among different nodes in bitcoin network, Bitcoin transaction is slow due to the fact that information needs to be propagated across the network to synchronize the ledger replicas. The slow dissemination of information exposes a potential security hole for the malicious attacks. Some measures have been implemented to mitigate the number of the blockchain forks in the network by 50%. However, a long-term solution is still needed. Like any other networks, Bitcoin network is no exception when it comes to malicious attacks. One of the notable form of attack against Bitcoin network topology is eclipsing attack by using information propagation knowledge. Bitcoin peer-to-peer network topology can be inferred and utilized by malicious attackers to perform precise attacks such as eclipsing attack. By observing the flooding process of the information flow, a flooding network’s topology can be inferred. A network topology inference method has been proposed along with a proof of concept in real network. The critical players of bitcoin transactions can be identified use various network centrality metrics. Blockchain might replace conventional methods of keeping track of valuable information such as contracts, intellectual-property rights, and corporate accountings.
Personal healthcare records need to be protected with the highest standard. With the increasing number of data breach incidents in the past several years, the awareness of the general public about the personal data privacy will continue to increasing. The necessity for data privacy will grow stronger with an increasing number of services and device collecting our personal data associated with our personal identity. There are techniques that obfuscate the linking of pseudonymous address and the real person such as Coin Join.
II. SYSTEM ARCHITECTURE
The security demanding situations are nevertheless a few of the fundamental boundaries when thinking about cloud adoption services. The primary reason is that the database hosted and processed inside the cloud server, which is beyond the control of the data owners. For the numerical question, those schemes do no longer offer sufficient personal safety towards sensible demanding situations. In this system, we suggest different statistics example architectures for a at ease database that protects several questions associated with the numeric variety. We put in force a three-layer/instance garage framework primarily based on facts computing. The generation of block-chain attracts high attention first because of the opportunity of decentralizing incredibly unstable operations, which traditionally carried out in predetermined records centers. The maximum famous example of use is the substitute of the feature of engaging in transactions within the system of financial institution transfers to a decentralized community of cryptographic handlers. The essence of this approach of processing financial transactions is the encryption of transaction sets combined into blocks with the inclusion within the code of the specific identifier code of the preceding block.
- Large data storage at the required of decentralized data storage as well as information system.
- The different attack issues in centralized database architectures.
- There is no automatic attack recovery in central data architectures
- The decentralized architecture provides the automatic data recovery from different attacks.
After the analysis of this system we move to develop the decentralized system architecture, and distributed computing provide parallel processing in distributed environment.
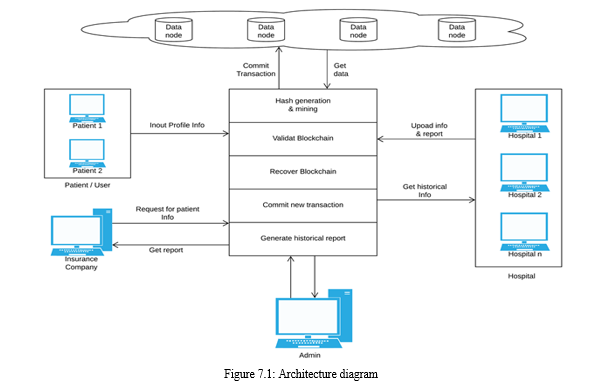
We take a holistic view of the pharmaceutical supply chain, presenting an end-to-end solution for drug traceability whereas only focused on a subset of these challenges. Firstly, our approach recognize and engages major stakeholders in the drug supply chain i.e. the CDSCO, supplier, manufacturer, distributor, pharmacy, and patient, whereas is limited to the supplier, manufacturer, and wholesaler as the stakeholders. Hence, the pharmacists are constituted as an external entity, which is not the case in a actual drug supply chain. Secondly, we make clear-cut efforts to spot and clarify relationships among stakeholders, on-chain resources, smart contracts, and decentralized storage systems, which are lacking in solution. Furthermore, because of the significance of interactions among stakeholders, we have included precise definitions to remove any ambiguity, whereas such interactions have not been defined as part of the system. Thirdly, we use smart contracts technology to attain real-time, seamless traceability with push notifications to minimize human intercession and therefore undesired delays. Particularly, each drug Lot is allocated a unique smart contract that create an event whensoever a change in ownership take place and a list of events is delivered to the DApp user. However, the smart contracts are programmed for specific roles such as supplier, manufacturer, and wholesaler, which require each participant to manually confirm which drugs are received. Such an approach can introduce delays and inaccuracies in the immutable data stored on the ledger. Eventually, we have conducted a cost and security analysis to assess the performance of the proposed solution including discussion on how the proposed solution can be generic to other supply chains.
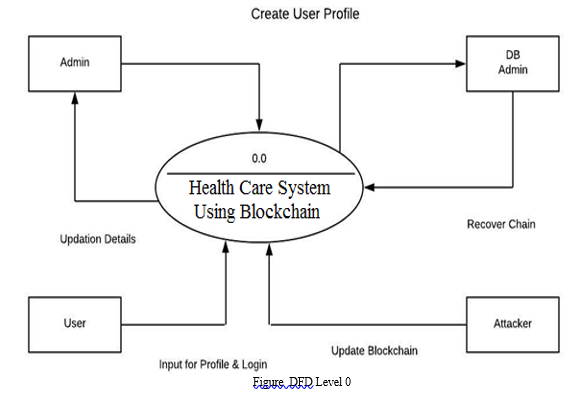
III. DATA FLOW DIAGRAM
- The DFD is also called as bubble chart. It is a simple graphical formalism that can be used to represent a system in terms of input data to the system, various processing carried out on this data, and the output data is generated by this system.
- The data flow diagram (DFD) is one of the most important modeling tools. It is used to model the system components. These components are the system process, the data used by the process, an external entity that interacts with the system and the information flows in the system.
- DFD shows how the information moves through the system and how it is modified by a series of transformations. It is a graphical technique that depicts information flow and the transformations that are applied as data moves from input to output.
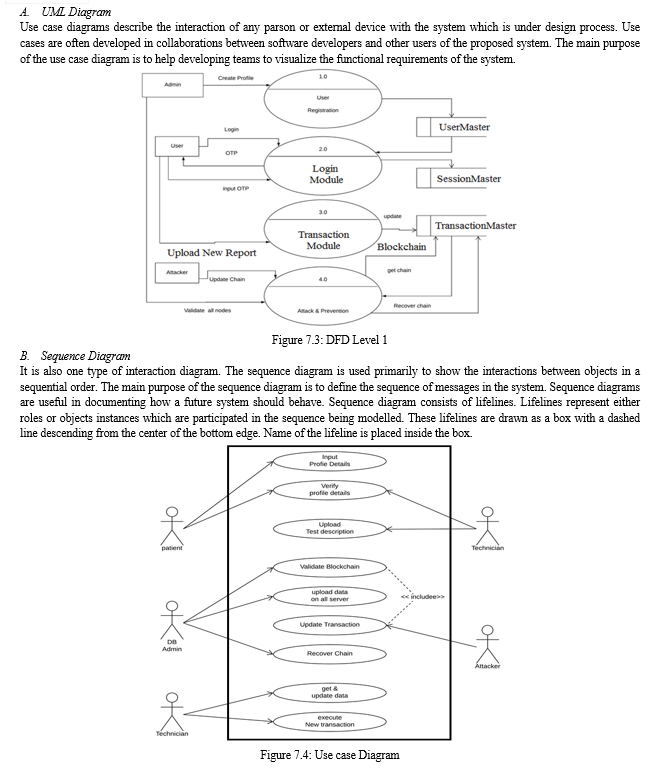
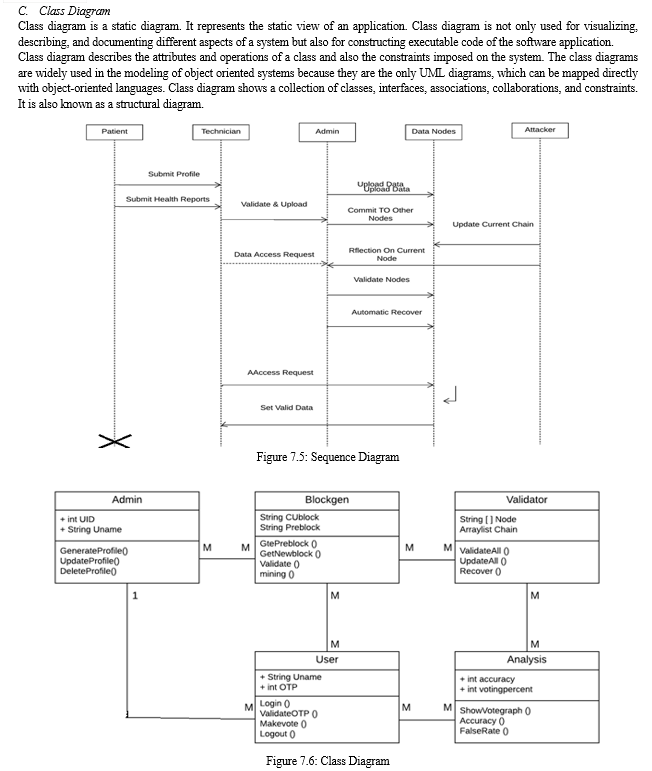
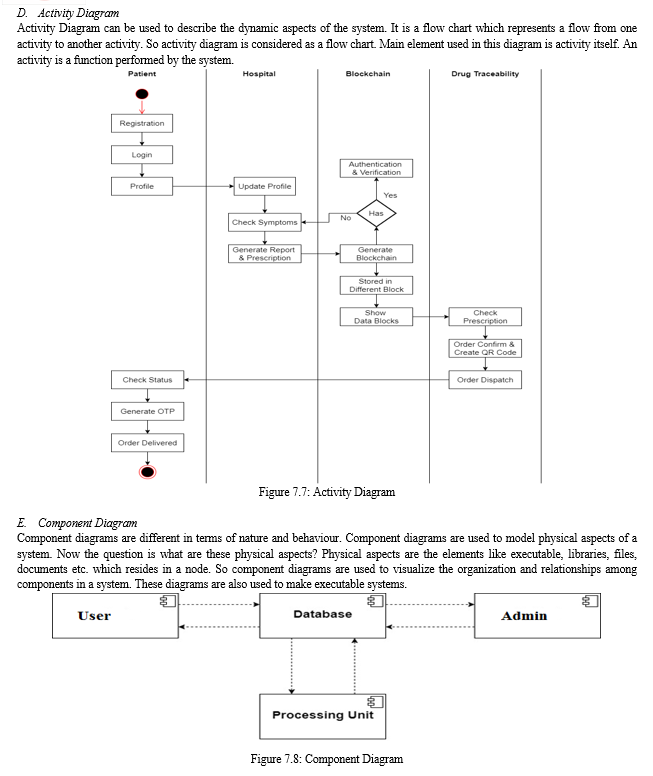
IV. METHODOLOGIES OF PROBLEM SOLVING
- Requirement Gathering and Analysis: In this step of waterfall we identify what are various requirements are need for our project such are software and hardware required, database, and interfaces.
- System Design: In this system design phase we design the system which is easily understood for end user i.e. user friendly. We design some UML diagrams and data flow diagram to understand the system flow and system module and sequence of execution.
- Implementation: In implementation phase of our project we have implemented various module required of successfully getting expected outcome at the different module levels. With inputs from system design, the system is first developed in small programs called units, which are integrated in the next phase. Each unit is developed and tested for its functionality which is referred to as Unit Testing.
- Testing: The different test cases are performed to test whether the project module are giving expected outcome in assumed time. All the units developed in the implementation phase are integrated into a system after testing of each unit. Post integration the entire system is tested for any faults and failures.
- Deployment of System: Once the functional and non-functional testing is done, the product is deployed in the customer environment or released into the market.
- Maintenance: There are some issues which come up in the client environment. To fix those issues patches are released. Also to enhance the product some better versions are released. Maintenance is done to deliver these changes in the customer environment. All these phases are cascaded to each other in which progress is seen as flowing steadily downwards like a waterfall through the phases. The next phase is started only after the defined set of goals are achieved for previous phase and it is signed off, so the name ”Waterfall Model”. In this model phases do not overlap.
V. SOFTWARE CONTEXT
- Java (J2EE)
- HTML/CSS
- Eclipse Oxygen
A. Major Constraints
- Environmental Constraints
- Power Failure: The system cannot function if there is a power failure.
2. Functional Constraints
- Network Failure: System will not function if there is a network failure while connecting with the database, while sending alerts, or generating reports.
- Connectivity Failure: Data may get lost if there are connectivity issues.MAJOR CONSTRAINTS
3. Environmental Constraints
- Power Failure: The system cannot function if there is a power failure.
4. Functional Constraints
- Network Failure: System will not function if there is a network failure while connecting with the database, while sending alerts, or generating reports.
- Connectivity Failure: Data may get lost if there are connectivity issues.
VI. METHODOLOGIES OF PROBLEM SOLVING AND EFFICIENCY ISSUES
Problem with physical to capture input data is there will be educational past history parameters to that area while trying them. There are multiple solution is available for this:
- Requirement Gathering and Analysis: In this step of waterfall we identify what are various requirements are need for our project such are software and hardware required, database, and interfaces.
- System Design: In this system design phase we design the system which is easily understood for end user i.e. user friendly. We design some UML diagrams and data flow diagram to understand the system flow and system module and sequence of execution.
- Implementation: In implementation phase of our project we have implemented various module required of successfully getting expected outcome at the different module levels. With inputs from system design, the system is first developed in small programs called units, which are integrated in the next phase. Each unit is developed and tested for its functionality which is referred to as Unit Testing.
- Testing: The different test cases are performed to test whether the project module are giving expected outcome in assumed time. All the units developed in the implementation phase are integrated into a system after testing of each unit. Post integration the entire system is tested for any faults and failures.
- Deployment of System: Once the functional and non-functional testing is done, the product is deployed in the customer environment or released into the market.
- Maintenance: There are some issues which come up in the client environment. To fix those issues patches are released. Also to enhance the product some better versions are released. Maintenance is done to deliver these changes in the customer environment. All these phases are cascaded to each other in which progress is seen as flowing steadily downwards like a waterfall through the phases. The next phase is started only after the defined set of goals are achieved for previous phase and it is signed off, so the name ”Waterfall Model”. In this model phases do not overlap. So, we are using above solution that is our system, we are performing the processing on current input data. This solution is best.
VII. SCENARIO IN WHICH MULTI-CORE, EMBEDDED AND DISTRIBUTED COMPUTING USED
Our system is Multi-User system.
A. Outcome
The potential outcomes of a project on ”A Blockchain-based approach for Drug Traceability in Healthcare Supply Chain” can include:
- Improved transparency and visibility of the drug supply chain: Blockchain technology can enable real-time tracking of drugs, from the manufacturer to the end-user, ensuring that all transactions are recorded and accessible to authorized stakeholders.
- Reduced counterfeiting: Blockchain can provide a tamper-proof and immutable record of the drug’s movement, making it difficult for counterfeiters to introduce fake drugs into the supply chain.
- Enhanced patient safety: With improved drug traceability, patients can be assured that the medicines they are taking are genuine and safe, reducing the risk of adverse drug reactions.
- Improved regulatory compliance: Blockchain-based solutions can help pharmaceutical companies comply with regulatory requirements related to drug traceability, serialization, and recall management.
- Improved efficiency and cost savings: Blockchain-based solutions can reduce manual effort and paperwork, streamline supply
VIII. APPLICATIONS
There are several real-time applications for the project report of ”A Blockchain-based approach for Drug Traceability in the Healthcare Supply Chain.” Some of them include:
- Drug Authentication: With a blockchain-based approach for drug traceability, it becomes possible to authenticate drugs in real-time. By using a unique identifier for each drug, stakeholders in the supply chain can track the movement of the drug from the manufacturer to the patient, ensuring that the drug is genuine and not counterfeit.
- Supply Chain Management: Another real-time application of a blockchain-based approach is supply chain management. By using blockchain technology, stakeholders can track the movement of drugs in real-time, ensuring that the drugs are delivered to the right place at the supplychain.
Conclusion
In this paper, we have examined the challenge of medicine traceability inside pharmaceutical supply chains highlighting its significance especially to protect against counterfeit medicine and medicine trafficking. We have developed and determined a blockchain-based solution for the pharmaceutical supply chain to track and trace medicine in a decentralized manner. Specifically, our proposed solution holds cryptographic fundamentals of block-chain technology to achieve protected logs of events within the supply chain and uses smart contracts within Custom blockchain to achieve automated recording of events that are accessible to all participating collaborators. We will continue our efforts to increase the efficiency of pharmaceutical supply chains and imagine focusing on extending the proposed system to achieve end-to-end transparency and provability of medicine use as future work.
Copyright
Copyright © 2023 Kiran Bhagwat , Pratibha Sudrik, Shraddha Pawar, Vishwanath Waghchaure, Prof. A. P. Suryavanshi . This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET53120
Publish Date : 2023-05-27
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

