Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Criminal Navigation System / Extractor
Authors: Aniket Kale, Akshata Shinde, Sushant Patil, Prof. Rajesh Kadu
DOI Link: https://doi.org/10.22214/ijraset.2022.42054
Certificate: View Certificate
Abstract
We proposed a criminal navigation system/extractor that retains a criminal\'s records and also forecasts primary suspects in this paper. The method is intended to assist agencies such as the CBI, CID, and other similar bureaus in expediting the investigation process. Case summary, people involved, conflicts, past criminal histories of those engaged, items recovered on scene, and other facts such as facial recognition and fingerprints are all included in the system. The system recognises the type of case and allows the administrator to update the investigation\'s status and submit more crime photographs. It investigates past criminal histories of all those involved and makes recommendations for suspects based on this information. There is no proper centralised database or tracking criteria for criminal investigation in the area of criminal navigation. This system is based on criminal records management and a criminal navigation system. The system has the most up-to-date information on previous crimes. Those recordings will be useful in future investigations and training for new police. Officers will save time and the investigative process will be sped up as a result of the technology. The suggested method is intended to encourage criminal investigation teams to collaborate on cases and to expedite the investigative process by proposing suspects.
Introduction
I. INTRODUCTION
Criminal Navigation System is also a criminal database in which law enforcement agents maintain track of criminals who have previously been apprehended, are most sought, have yet to be apprehended, or have escaped custody. The forecast is made after all of the suspects have been interrogated by law enforcement personnel in the interrogating area and the data has been entered into to the data base.However, the Criminal Records management nowadays is majorly done using manual methods, which
is, simply the use of pen and paper. Therefore, these records can be misused by both who have authorized to access these records as well as a person who does not have authorized access. These manual methods have created problems in some areas like security, authenticity, storage, retrieval, and exchange of information The proposed system is designed to encourage investigation teams to work collectively on criminal cases and speed up the investigation process by suggesting suspects based on data provided to the system Using this system, the admin can check out the past events from the System & get all details about past crimes. Using this system Admin can use previous crime reports to investigate future cases. Admin will have to manually input all the details about the criminal case into the system.
II. LITERATURE REVIEW
This chapter examines the relevant literatures to show how this project ties to previous research. This review serves as a bridge between the project and previous studies. It also emphasis the that has previously been established and concluded This chapter will also continue with the previous system's talks and ideas, as well as research. The crime management system is the subject of a journal and an article. Since the introduction of the new system, it has become extremely difficult to locate the previous system. The system is private and cannot be viewed by the general public. In addition, the technique and algorithm are contrasted.to determine which method is the most systematic and efficient. The analytic hierarchy process algorithm was chosen for this project. The research on the analytic hierarchy process algorithm has been combined with prior research, and some research on the analytic hierarchy process algorithm has been completed. Furthermore, research into another suitable algorithm is being employed in a variety of research and studies to investigate new methods and make comparisons. The Deep Neural Network technology and method will be used to develop the Criminal Navigation System / Extractor. Input is passed through numerous "layers" of neural network algorithms in deep learning algorithms, each one passes a reduced version of the data to the next layer. When you really need to substitute human labour with autonomous work without sacrificing efficiency, a deep neural network can help. In real life, deep neural networks can be used in a variety of ways. Fingerprint scanners capture the grooves on a finger's pattern. The gadget measures the charge while a finger rests on the capacitance surface; ridges generate a variation in capacitance, whereas valleys produce almost no change at all. All of this information is used by the sensor to correctly map out prints.
A. Comparison between Previous Journals and Articles
[1].The Directorate of Students and Services Development (DSSD) is in charge of investigating and identifying criminals who commit crimes at Redeemer's University. When it comes to identifying the true offenders of certain crimes, the DSSD has significant obstacles. The main goal of this project is to develop their strategy so that they may achieve the great results and rates of high success.[2]. This is evidenced in the usage of automated crime record management systems (CRMS) by law
enforcement organization around the world to keep track of crimes and criminals involved. Crime is a threat to society since it is an act against law. As a result, for efficient and effective monitoring is required to ensure the population's well-being. Because of this, CRMS was created specifically for this purpose.[3]. This study discusses a data mining-based approach for extracting relevant items from police narrative reports. Crime data will be entered automatically into a database at law enforcement agency utilizing this method.[4]. National security has long been a source of anxiety for Nigerians. There is a religious crisis in some Northern Nigerian states, and kidnappings in some of South-East states, South-West regions, and bombings in Abuja and other parts of the country. To strengthen Nigeria's security and justice, as well as to safeguard the safety of its residents, a tangible and user-friendly system must be established at all levels, allowing for the effective interchange of information on criminals' previous convictions.[5]. By including fingerprint bio-metrics into the model, a web-based prototype was created. The minutiae were retrieved and a template was constructed using the Delaunay technique after the captured fingerprint pictures were prepossessed using the wavelet scalar quantization (WSQ) algorithm. Through automation, the built system improved the business process.[6]. This suggested system is based on a criminal investigation tracker and the management of criminal records. All of the facts concerning previous offenses will be stored in the system. These recordings will aid in the investigation of future instances and the training of new law enforcement agents. The method will save law enforcement officials' time and expedite their entire investigation process.
III. DESIGN
The system architecture is critical in determining entities, properties, and relationships in this area. The Crime Investigation System with Suspect Prediction has the following entities: admin, officer, suspect, cases, suspect criteria, and crime types.
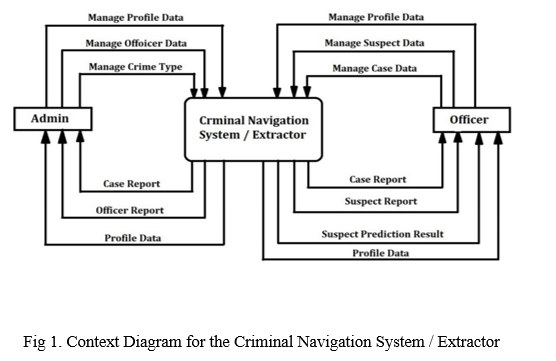
A. Description of Context Diagram
Figure shows the Context Diagram for the Criminal Navigation System / Extractor. The Criminal Navigation System / Extractor is located in the diagram's middle. There are two types of entities. ADMIN and OFFICER are the central processes that are encircled. In the relationship between both the processes and the entities, 13 data flows are involved. There are three data outgoing entities in the Admin entity. MANAGE PROFILE DATA, MANAGE OFFICER, MANAGE TYPE OF CRIME are the three flows. PROFILE DATA, OFFICER REPORT, and CASE REPORT are the three incoming data flows. REPORT ON CRIME. Following that, the OFFICER unit has three outward data-flows, the first of which is MANAGE PROFILE DATA .MANAGE SUSPECT DATA, MANAGE CASE DATA, and PROFILE DATA There are four of them. OFFICER data flows include PROFILE DATA, CASE REPORT, and SUSPECT REPORT and SUAPECT PREDICTION RESULT.
IV. WORKING
A. Functional
- Officers will be able to enter new criminal data (image/fingerprint) to the system.
- Officers will be able to upgrade criminal data (image/fingerprint) via the system.
- Officers should be simply delete criminal data (images/fingerprints) from the system.
- The system must be able to display a list of criminal data (images/fingerprints).
- Officers will be able to add new cases to the system.
- The system should allow officers to make changes to their cases.
- Officers should be able to delete cases from the system.
- Officers will be able to add suspects to the system.
- Officers will be able to update suspect information using the system.
- Officers will be able to eliminate suspects from the system.
- Officers will be able to view suspect predictions.
B. Non-Functional
- Security: For all operations, the Admin and Officer will be required to login. The pass code will be encrypted before being saved to the database.
- Reliability: The system must have a 99 percent availability, which means that out of every 100 requests, 99 must be fulfilled. The initial data must be carefully and precisely obtained. The database must be backed up on a regular basis and be recoverable in the event of a disaster.
- Availability: Users should be able to access the system at any time. The availability is 24 hours a day, seven days a week. After the user submits the questions, the response to the queries should load into the screen in no more than 15 seconds. Within 15 seconds, the login details must be validated. The system will be able to handle 200 users at the same time.
- Portability: The website can be accessed with any browser that has access to the internet.
- Maintainability: The system must be capable of data backup. All errors must be recorded by the system.
- Flexibility: Users can update and delete their profiles using the system's flexibility. Owners can add, delete, and update their admins using the system.
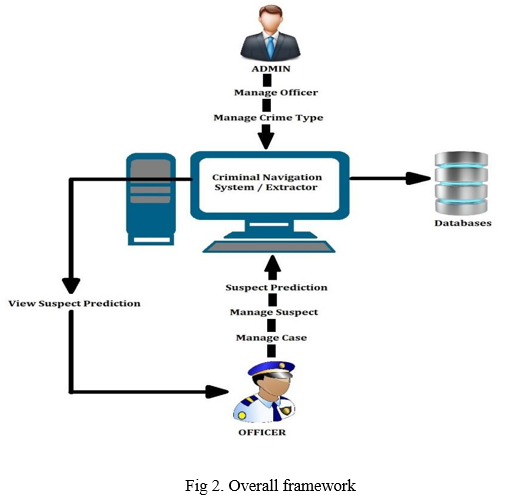
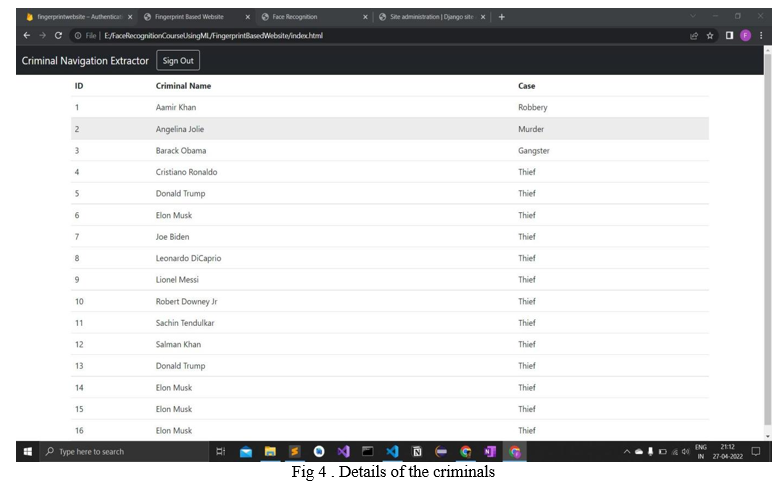
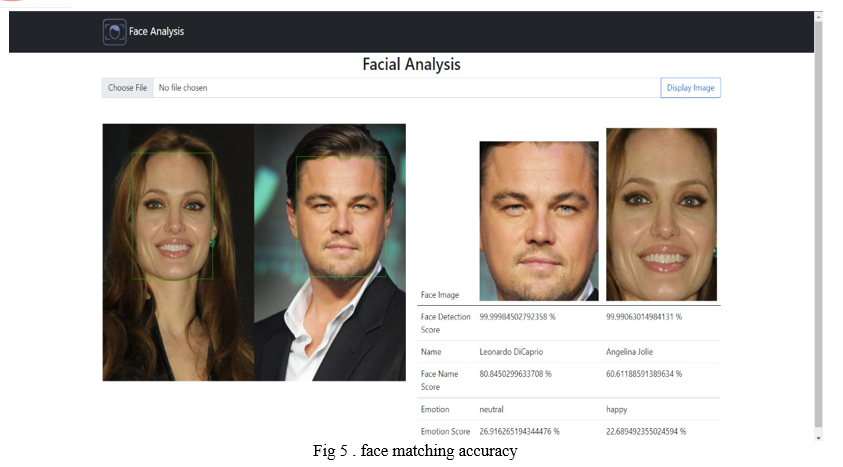
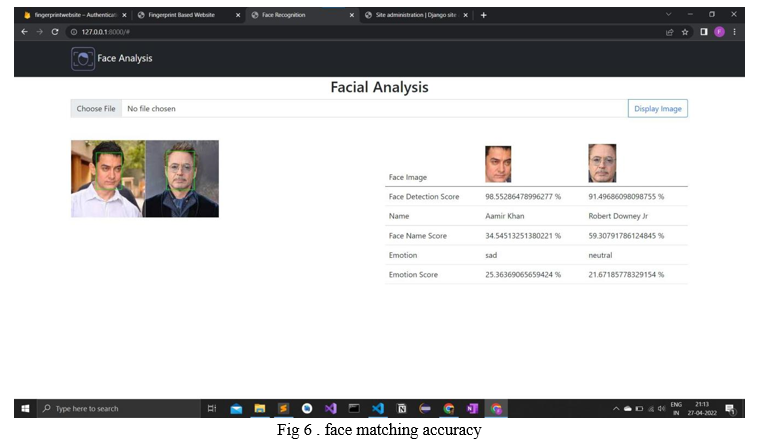
VI. FUTURE SCOPE
A. User
Admin
- Admin can add new officers
- Admin can access case reports from the database
Officer
- Officers can add data about case if it involves several suspects.
- After the questioning session with the suspect, the officer can add the suspect's data criteria to the system, which will forecast the criminal with the highest probability among multiple suspects.
Place
- Police Department
- Forensic Department
System
- Because this system will be extensively used in the forensic department, it will be web-based as well as data will be kept in a distributed database.
VII. ACKNOWLEDGMENT
We would like to express our gratitude to Prof. Rajesh Kadu, our project guide, for their constant encouragement and inspiration in ensuring the success of our study. Our project manager insisted that we work with them.excellent direction, thoughtful recommendations, and timely motivation that aided us in making decisions about our project.
We also like to express our gratitude to our H.O.D. Dr. Ashok Kanthe, who has been a great help to us.allowing us to use the computer facilities at our laboratory for our project and making it a reality success. Our research would've been stifled to a halt if it hadn't been for their gracious and eager cooperation.
Finally, we'd like to express our gratitude to our college's vice principal, Dr.V.G. Sayagavi, for providing lab space and allowing us to continue with our project. We'd also want to express our gratitude to our colleagues who assisted us explicitly or implicitly during the project.
Conclusion
In our system, we\'ve created a fully integrated and portable system that the police may use. The police dept, security agencies, and even the forensic department will all employ this project in the future. The project\'s biggest strength is that it incorporates new features while maintaining the original qualities of old systems (for example, the Criminal Database). An attempt has been made to suggest a system that is capable of recognizing a criminal based on his or her face and fingerprints, thereby assisting law enforcement efforts.
References
[1] Adewale Opeoluwa Ogunde, Gabriel Opeyemi Ogunleye, Oluwaleke Oreoluwa,A DECISION TREE ALGORITHM BASED SYSTEM FOR PREDICTING CRIME IN THE UNIVERSITY. Department of Computer Science, Redeemer’s University, Ede, Nigeria and Department of Computer Science, Federal University, Oye-Ekiti, Nigeria Received: January 27, 2017; Accepted: February 13, 2017; Published: March 2, 2017. [2] Oludele Awodele, Onuiri Ernest E., Olaore Olufunmike A., Sowunmi Oluwawunmi O.Ugo-Ezeaba Anita A. A REAL-TIME CRIME RECORDS MANAGEMENT SYSTEM FOR NATIONAL SECURITY AGENCIES. European Journal of Computer Science and Information Technology. Vol.3, No.2, pp.1-12, May 2015. [3] MohammadReza Keyvanpoura, Mostafa Javidehb, Mohammad Reza Ebrahimia. DETECTING AND INVESTIGATING CRIME BY MEANS OF DATA MINING: A GENERAL CRIME MATCHING FRAMEWORK. Department of Computer Engineering, Alzahra University, Tehran, Iran Shamsipoor Technical College, Tehran, Iran Islamic Azad University, Qazvin Branch, Qazvin, Iran 45. [4] Daniel E.S. Kawai, Dogo H. Samson. DEVELOPMENT OF CRIMINALS RECORD INFORMATION SYSTEM. Department of Mathematical Science, Faculty of Science, Kaduna State University, Kaduna, Nigeria. [5] G. Lyoko, J. Phiri, and A. Phiri. Integrating Biometric into Police Information Management System: A Case of Zambia Police. Life Science Journal. Vol. 5, No. 1, February 2016. [6] MUHAMMAD SHAHRUL HANIFF BIN OSMAN, CRIME MANAGEMENT SYSTEM WITH SUSPECT PREDICTION USING AHP METHOD, Thesis Submitted in Fulfilments of the Requirement for the Bachelor of Computer Science (Software Development) In the Faculty of Informatics and Computing University Sultan Zainal Abidin MAY 2018.
Copyright
Copyright © 2022 Aniket Kale, Akshata Shinde, Sushant Patil, Prof. Rajesh Kadu. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET42054
Publish Date : 2022-04-30
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

