Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Cyber Harassment Detection on Social Network Using Deep Convolutional Neural Network
Authors: Aruna Rajeswari K K, Lavanya M K, Saranya P
DOI Link: https://doi.org/10.22214/ijraset.2022.44624
Certificate: View Certificate
Abstract
Rate of innovation is increasing apace. This growth in innovation provides another dimension of communication. However, in spite of the very fact that innovation conjures up U.S. in numerous elements of life, it goes with completely different effects that influence folks during a hardly or the opposite means. Cyber Harassment is one in every of them. Social media provides a platform to speak with plenty, however it additionally becomes an area for negative comments and cyber harassment. Cyber Harassment is bullying dead through digital equipment’s like laptop computer and mobile devices. Cyber Harassment happens on social media, chat rooms and play platform wherever folks will read and share their own content. Cyber Harassment embrace causing hurtful messages posting sensitive photos or video on social media, and increasing mean rumors on-line. Cyber Harassment is large drawback. Thus, on forestall such drawback Cyber Harassment detection technique supported deep neural network is developed referred to as Convolution Neural Network (CNN). CNN is employed for the higher outcomes once contrasted with the present systems.
Introduction
I. INTRODUCTION
With the emergence of internet, a pair of 2.0 there has been a considerable impact on social communication, and relationships and friendships are redefined everywhere once more. Adolescents pay a substantial quantity of your time on-line and on completely different social platforms, besides all the advantages that it'd bring them, their on-line presence additionally create them susceptible to threats and social misbehaviours like Cyberharassment.
Studies show that concerning eighteen of the youngsters in Europe are concerned in cyberharassment. Within the 2014 EU youngsters on-line Report it's explicit that 2 hundredth of youngsters from eleven to sixteen years previous are exposed to on-line bullying. The quantitative analysis of shows that cyber-victimization rates among teenagers between 2 hundredth and four-hundredth.
These statistics proceed and on a pair of,3 of these demonstrate the importance of finding a strong and comprehensive resolution to the present widespread drawback. Cyberbullying must be understood and addressed from completely different views. Automatic detection and interference of those incidents will well facilitate to tackle this drawback. There are area unit already tools developed which might flag a bullying incident and programs that attempt to offer support to the victims. Moreover, most of the web platforms that area unit usually employed by teenagers have safely centres, for instance, YouTube Safety Centre4 and Twitter Safety and Security, which give support to users and monitor the communications. There are additionally several analyses conducted on automatic detection and interference of cyberbullying, that we'll address in additional details within the next section, however this drawback continues to be removed from resolved and there's the requirement for additional enhancements towards having a concrete resolution.
Most of the present studies have used standard Machine Learning (ML) models to sight cyberbullying incidents. Recently Deep Neural Network primarily based (DNN) models have additionally been applied for detection of cyberbullying. In, authors have used DNN models for detection of cyberbullying and have distended their models across multiple social media platforms. Supported their rumoured results, their models beat ancient cubic centimetre models, and most significantly authors have explicit that they need applied transfer learning which implies their developed models for detection of cyberbullying are often custom-made and used on alternative datasets.
A. Main Text
With the unbelievable growth of the web, social media has become a significant concern in today ‘s life. This is often predicted as a platform to harass and target people. Cyberbullying has emerged a growing bother. Cyberbullying results into severe humiliation and defamation. Church bench analysis Institute survey in 2014, commented that four-hundredth of the web users have in person intimate on-line ill-usage, and forty fifth of these have intimate severe harassment. Typically, severe cases of cyber-bullying even led the victims to kill. Bullying contains of images been changed to degrade people, videos or pictures connected with physical bullying, revealing personal data to harass folks, perpetually poke people with unacceptable or unwanted messages.
B. Background Work
Varieties of mechanisms area unit developed for detection of cyberbullying. These mechanisms largely treat drawback as Classification drawback, within which messages area unit classified as intimidated or non-bullied messages. numerous datasets of social sites area unit accustomed confirm the performance of algorithms, accuracy, and potency and in what time the results area unit generated. Whole method relies on options extracted from text.
Depending on features they are classified into 4 categories:
C. Content Based Features
Content primarily based attributes area unit like prevalence of writing system pronouns, document length, utterance etc. the entire ton of social sites area unit flooded with matter posts, comments, wishes, messages, chats. of these acts as contents that is then pre-processed to content -based options. The options play a very important half in distinctive bullies. Following information pre-processing takes place for distinctive content-based.
- Stop word Removal: A, abort, me, ours, yourself, himself, if etc. are removed as these words makes no sense while processing data.
- Tokenization: Characters are broken into chunks of pieces and throwing certain character like punctuation.
- Stemming: These reduces the word to its original root word, for e.g., Processing -> process
- URLs removal
- Hash-tag removal
- Lower Casing the Letter
- White space removal.
- Least and Frequent Words Removal
Types of Sentiment Analysis:
- Fine-grained Sentiment Analysis
- Very Positive
- Positive
- Neutral
- Negative
- Very Negative
2. Emotion Deduction
This type of sentiment analysis aims at police investigation emotions, like pleasure, exasperation, anger, sadness, and so on. several feeling recognition systems use lexicons (i.e., lists of words and therefore the emotions they convey) or complicated machine learning algorithms.
3. Aspect Based Sentiment Analysis
Usually, once deciding sentiments of texts, let ‘s say product reviews, you ‘ll need to grasp that specific aspects or attributes individual square measure mentioning in a very positive, neutral, or negative manner. that is wherever aspect-based sentiment analysis will facilitate, for instance during this text: "The battery lifetime of this camera is just too short", associate degree aspect- based mostly classifier would be able to verify that the sentence convey a negative opinion regarding the attribute battery life.
4. Multilingual Sentiment Analysis
Multilingual sentiment analysis is tough. It involves loads of pretreatment and resources. Most of those resources square measure offered on-line (e.g., sentiment lexicons), whereas others got to be created (e.g., translated corpora or noise detection algorithms).
- Sentiment Based Features: It incorporates use of labeled datasets and sentiments wordlist. The get square measure options if used with function word will increase potency of detection system. SVM classifier is employed to find sentiments in tweets.
- User based Features: User-Based options incorporates users ‘gender, age, race, sexual orientation. These options have considerably improved the detection method as well as interference access to net or causation associate degree responsive to the oldsters. Age is accustomed limit the young users to varied parts of social media. Lexical syntactical framework computes harmful score for the users supported these options.
- Network Based Features: Network based mostly options embody social media network knowledge like no. of friends, uploads, likes and then on. variety of friends will facilitate in deciding what friend one has and it is easier to find among what class the chums fall. The frequency of uploads will verify the state of mind of person. variety of likes and dislikes will show the interest of individuals in victim. Dislikes will have bigger impact on finding the bully illustration of matter. instead of coping with text as strings of random numbers, the machine truly understands what that text suggests that. For e.g., think about the text ?smart in conjunction with their semantically similar text like intelligent, clever, good, better, of these words can have same similarity score by exploitation word embedding layer.
- CNN: The design of CNN contains of associate degree input, output layer and a couple of of hidden layers. This square measure the most core layers of the entire convolution neural network.
- Word Embedding: This class of technique generates numerical Convolutional Layer- This class of deep neural network is known as the heart of the neural network. It is the second layer after the embedding layer, it compresses the original input vector by preserving the important features. For this, a set of matrices is created called filters of random numbers called weights. As the filters convolved through the original input vector, it creates many feature maps by using element wise multiplication with the part of the input
- Max Pooling Layer: After convolution layer, grievous bodily harm pooling layer is employed that reduces the scale of the feature maps. At each location within the output, the pooling operation replaces the output at that location with a outline data point of near location. The depth of the feature map remains a similar. Thus, solely valuable, clear and purposeful options square measure preserved.
- Dense Layer: The previous layers were involved with compression of the input file in a very purposeful manner. Dense layers square measure the set of totally connected layers. the task of the dense layer is to classify the dates. every vegetative cell is connected to any or all alternative neurons, there will be variety of dense layers, however, the last vegetative cell should have a pair of neurons indicating.
II. LITERATURE SURVEY
Several efforts are created for a lot of privacy aware on-line Social Networks (OSNs) to shield personal knowledge against varied privacy threats. However, despite the connection of those proposals, we have a tendency to believe there's still the shortage of an abstract model on prime of that privacy tools need to be designed. Central to the current model ought to be the conception of risk. Therefore, during this paper, we have a tendency to propose a risk live for OSNs. The aim is to associate a risk level with social network users so as to supply alternative users with a live of what quantity it'd be risky, in terms of speech act of personal data, to own interactions with them. we have a tendency to reckon risk levels supported similarity and profit measures, by conjointly taking under consideration the user risk attitudes. particularly, we have a tendency to adopt an energetic learning approach for risk estimation, wherever user risk angle is learned from few needed user interactions. the chance estimation method mentioned during this paper has been developed into a Facebook application and tested on real knowledge. The experiments show the effectiveness of our proposal. Even though the benefits of on-line discussions over face-to-face discussion formats are extensively reportable and investigated, the mixing of on-line discussion tools in co-located schoolroom settings has been thought-about with way less intensity. during this paper, we have a tendency to report on middle school students’ experiences and preferences regarding 2 totally different discussion formats in co-located schoolroom settings, particularly face-to-face (F2F) and synchronous, computer-mediated communication (CMC). additionally, we have a tendency to conjointly differentiate between students that square measure renowned to move participants in F2F schoolroom discussions and people WHO sometimes stay silent. The findings highlight many blessings of CMC over F2F discussions in co-located settings and show that totally different students ('active' and 'silent') expertise F2F and computer-mediated communication otherwise.
Sybil attacks in social and data systems have serious security implications. Out of the many defence schemes, Graph-based Sybil Detection (GSD) had the best attention by each academe and business. although several GSD algorithms exist, there's no analytical framework to reason concerning their style, particularly as they create totally different assumptions concerning the used resister and graph models. during this paper, we have a tendency to bridge this information gap and gift a unified framework for systematic analysis of GSD algorithms. we have a tendency to use this framework to point out that GSD algorithms ought to be designed to search out local people structures around renowned non-Sybil identities, whereas incrementally chase changes within the graph because it evolves over time.
III. PROPOSED SYSTEM
OSN population is absolutely heterogeneous in determined behaviours. However, the same as globe, we have a tendency to expect that similar users (e.g., similar in activity level, gender, education, country, then on) tend to follow similar rules (e.g., moral, social) with the results of comparable behavioural models. a two-phase risk assessment, wherever users square measure initial classified along per some options purposeful for cluster identification. Then, for every known cluster, we have a tendency to build one or a lot of traditional behaviour models. to beat this issue, the Deep Neural Network algorithmic rule is projected during this system. This algorithmic rule mechanically blocks the unwanted text post message expeditiously. This methodology is enforced in java platform with the side NetBeans compiler and MySQL info as backend.
In the projected system, the dataset is collected then the feature extraction is completed with pre-processed numerical values needs to convert the vary of feature values between zero and one. Then the projected system enforced the deep learning algorithmic rule of neural network techniques that used for the dynamic interference method. This algorithmic rule mechanically blocks the unwanted text post message and within the classification strategies exploitation the supervised strategies. This algorithmic rule creates a lot of variety of class, below this class its hold on a lot of knowledge.
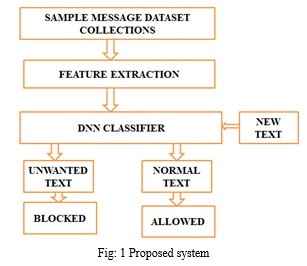
A. Proposed Algorithm
The neural network must learn all the time to resolve tasks during an additional qualified manner or perhaps to use numerous ways to produce an improved result. once it gets new info within the system, it learns the way to act consequently to a brand-new state of affairs.
Learning becomes deeper once tasks you solve get more durable. Deep neural network represents the kind of machine learning once the system uses several layers of nodes to derive high-level functions from input info. It suggests that remodelling the information into an additional inventive and abstract element.
In order to grasp the results of deep learning higher, let’s say an image of a median man. though you've got ne'er seen this image and his face and body before, you'll perpetually determine that it's somebody's and differentiate it from alternative creatures. this is often associate example of however the deep neural network works. inventive and analytical elements of data area unit analysed and classified to make sure that the item is known properly. These elements don't seem to be delivered to the system directly, so the metric capacity unit system needs to modify and derive them.
B. Deep Neural Network (DNN)
The area unit differing kinds of neural networks and therefore the variations between them lies in their work principles, the theme of actions, and therefore the application areas. Convolutional neural networks (CNN) area unit principally used for image recognition, and infrequently for audio recognition. it's principally applied to photographs as a result of there's no have to be compelled to check all the pixels one by one. CNN checks a picture by blocks, ranging from the left higher corner and moving more component by component up to a winning completion. Then the results of each verification are more matured a convolutional layer, wherever knowledge parts have connections whereas others don’t. supported this knowledge, the system will turn out the results of the verifications and might conclude what's within the image.
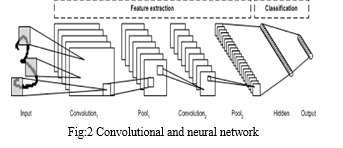
The use of deep layers of process, convolutions, pooling, and a totally connected classification layer opened the door to varied new applications of deep learning neural networks. additionally, to image process, the CNN has been with success applied to video recognition and numerous tasks among linguistic communication process. The DNN may be a typical spec however includes a unique coaching rule. The DNN may be a multilayer network (typically deep, as well as several hidden layers) during which every combine of connected layers may be a restricted physicist machine (RBM). during this manner, a DBN is depicted as a stack of RBMs.
In the DNN, the input layer represents the raw sensory inputs, and every hidden layer learns abstract representations of this input. The output layer, that is treated somewhat otherwise than the opposite layers, implements the network classification. coaching happens in 2 steps: unattended pretraining and supervised fine-tuning
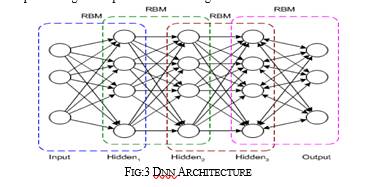
In unsupervised pretraining, every RBM is trained to reconstruct its input (for example, the primary RBM reconstructs the input layer to the primary hidden layer). following RBM is trained equally, however the primary hidden layer is treated because the input (or visible) layer, and therefore the RBM is trained by victimisation the outputs of the primary hidden layer because the inputs. This method continues till every layer is pretrained. once the pretraining is complete, fine-tuning begins. during this part, the output nodes area unit applied labels to provide them that means (what they represent within the context of the network). Full network coaching is then applied by victimisation either gradient descent learning or back-propagation to finish the coaching method.
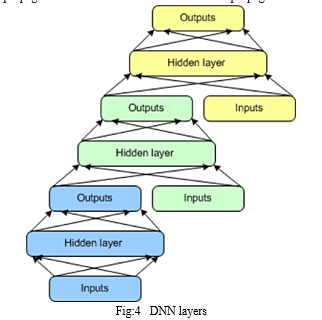
The DNN consists of a set of modules, each of which is a subnetwork in the overall hierarchy of the DNN. In one instance of this architecture, three modules are created for the DNN. Each module consists of an input layer, a single hidden layer, and an output layer. Modules are stacked one on top of another, where the inputs of a module consist of the prior layer outputs and the original input vector. This layering allows the overall network to learn more complex classification than would be possible given a single module.
The DNN permits training of individual modules in isolation, making it efficient given the ability to train in parallel. Supervised training is implemented as back-propagation for each module rather than back-propagation over the entire network.
Conclusion
Social media provides platform to attach individuals from Brobdingnagian distance. because of several easy options provided by these social media platforms they\'re turning into additional standard. Besides that, social media platform is turning into place for hateful and abusive comments leading to cyber bullying. to handle such several techniques are developed from that Convolutional Neural Network provides ninety-seven 0.8% accuracy. This is often additional intelligent approach as compared to the normal methodology. the most aim was to advance the present processes of cyberharassment detection by addressing crucial downside that haven\'t been resolved nonetheless. The planned algorithmic rule makes cyberharassment detection a totally machine-driven method that needs no human intervention. Comprehensive analysis established that deep learning surpasses the classical machine leaning approaches in cyberharassment. All the work done is on statically generated dataset wherever dataset is train and value at some purpose of your time. So, this method won\'t be a lot of economical on real time knowledge. Future work includes developing algorithmic rule to method dynamic or real time knowledge.
References
[1] Child Predator Detection System On Social Media,Arman Gangani,Aman Gangani,Shruti Kale, Dikshita Jain, Prof. A J Kadam, IJCRT,2022 [2] Cyber-Bullying Detection in Hinglish Languages Using Machine Learning, Karan Shah, Chaitanya Phadtare, Keval Rajpara, International Journal of Engineering Research & Technology (IJERT),2022 [3] Deep Learning For Detecting Cyberbullying Across Multiple Social Media Platforms, Habib Mohammed Yamani, Mohammed Faraz,Syed Mahmood Ali,T. Anita,2022 [4] Cyber-Bullying Detection in Social Media Platform using Machine Learning,Aditya Desai, Shashank Kalaskar,Omkar Kumbhar, and Rashmi Dhumal,2021 [5] Current limitations in cyberbullying detection: On evaluation criteria, reproducibility, and data scarcity, Chris Emmery,Ben Verhoeven,Guy De Pauw, Gilles Jacobs, Cynthia Van Hee,Els Lefever,Bart Desmet ,Ve´ronique Hoste,Walter Daelemans,2021. [6] DeepSBD: A Deep Neural Network Model WithAttention Mechanism for SocialBot DetectionMohd Fazil , Amit Kumar Sah, and Muhammad Abulaish , Senior Member, IEEE,2021. [7] A Decentralized Deep Learning Approach for Detecting Abusive Textual Content, Pranav Kompally, Sibi Chakkaravarthy Sethuraman, Steven Walczak, Samuel Johnson and Meenalosini Vimal Cruz,2021 [8] A Study of deep learning algorithms for multimodel and multilingual cyberbullying detection, Dr. Vijayakumar V, Dr Hari Prasad D,2021. [9] Multi-Input deep learning algorithm for CyberBullying Detection, Dr. Vijayakumar V, Dr. Hari Prasad D, Adolf P,2021. [10] Multi-Featured CyberBullying detection based on deep learning, Yue Luo, Xurui Zhang, Weixuan Shen,2021 [11] Cyberbullying Detection using deep convolutional neural network from social media comments in bangala language, Md Faisal Ahmed, Zalish Mahmud, Zarin Tasnim Biash, Ahmed Ann Noor Ryen, Arman Hossain, Faisal Bin Ashraf,2021 [12] Cyberbullying detection using Machine learning utilizing social media data, Md. Abdur-Rakib, Rashedur Rahman, Khadiza- Tul- Kobra,202 [13] Accurate Cyberbullying Detection and Prevention on social media, CENTERIS - International Conference on ENTERprise Information Systems / ProjMAN - International Conference on Project MANagement / HCist - International Conference on Health and Social Care Information Systems and Technologies 2020 [14] Cyberbullying severity detection: A machine learning approach, Declan O’Sullivan,2020. [15] Social Media Cyberbullying Detection using Machine Learning, (IJACSA) International Journal of Advanced Computer Science and Applications,John Hani, Mostafa Ahmed,Zeyad Emad,Eslam Amer, Mohamed Nashaat,2019.
Copyright
Copyright © 2022 Aruna Rajeswari K K, Lavanya M K, Saranya P. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET44624
Publish Date : 2022-06-20
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

