Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Enhancing Product Trust Using Blockchain
Authors: Sahil Bhosale, Aditya Bhosale, Sreerag Nair, Arjun Mohan, Prof. Anita Patil
DOI Link: https://doi.org/10.22214/ijraset.2023.52715
Certificate: View Certificate
Abstract
Counterfeit products have become a major issue in the global market, causing significant economic losses to businesses and health and safety risks to consumers. Blockchain technology has the potential to address this problem by creating a secure and immutable record of the origin and movement of products. This paper explores the use of blockchain technology for identifying counterfeit products. We examine the characteristics of blockchain technology, its benefits, and limitations. We also discuss the current approaches used for product identification and how blockchain technology can be used to enhance these methods. We present a case study on how blockchain technology can be implemented to identify counterfeit pharmaceuticals, one of the most critical areas of concern. The results show that blockchain technology can be a useful tool in identifying counterfeit products, as it provides an immutable record of product provenance, enhances traceability, and reduces the risk of fraud.
Introduction
I. INTRODUCTION
Counterfeit products pose significant risks to businesses, consumers, and economies globally. Counterfeit products not only cause financial losses to businesses but also pose significant health and safety risks to consumers. The traditional methods of product identification, [1]such as holograms, watermarks, and serial numbers, are becoming less effective as counterfeiters become more sophisticated. The need for more advanced and secure methods of product identification has become a top priority for businesses and governments worldwide.
A. Blockchain Technology
Blockchain Technology which provides a distributed and immutable record of transactions, is increasingly being considered as a solution to address the issue of counterfeit products. The blockchain can provide a secure and transparent record of the product's origin, movement, and ownership.[2] In this paper, we explore how blockchain technology can be used to identify counterfeit products, with a specific focus on pharmaceuticals.
- Characteristics of Blockchain Technology
Blockchain technology is a decentralized, distributed ledger that records and verifies transactions through a network of computers. The characteristics of blockchain technology that make it suitable for product identification include:
a. Decentralization: Blockchain technology is a decentralized system, which means that there is no central authority that controls the data. This means that the data is more secure and less prone to hacking.
b. Transparency: The blockchain is a transparent system, meaning that all transactions are visible to all participants. This transparency can be used to verify the authenticity of products and trace their origin.
c. Immutability: Once data is recorded on the blockchain, it cannot be altered or deleted. This feature ensures the integrity of the data, making it more reliable.
d. Security: The blockchain uses advanced cryptography to secure transactions and prevent fraud.
2. Benefits of Using Blockchain Technology for Product Identification
The use of blockchain technology for product identification has several benefits, including:
a. Enhanced Traceability: The blockchain can provide a complete and transparent record of the product's journey from the manufacturer to the end consumer. This information can be used to verify the authenticity of the product and trace its origin.
b. Improved Supply Chain Management: Blockchain technology can be used to enhance supply chain management, including tracking the movement of goods, reducing paperwork, and increasing efficiency.
c. Reduced Counterfeiting: The immutable record provided by the blockchain can help prevent counterfeiting by verifying the authenticity of products.
d. Increased Consumer Confidence: Consumers can be more confident about the authenticity of the products they purchase, which can increase their trust in the brand.
3. Limitations of Using Blockchain Technology for Product Identification
While the use of blockchain technology for product identification has several benefits, it also has some limitations, including:
a. High cost: Implementing blockchain technology can be expensive, especially for small and medium-sized businesses.
b. Limited scalability: The blockchain is limited in its ability to process transactions, which can limit its scalability.
c. Limited adoption: The use of blockchain technology is still in its early stages, and many businesses and consumers are not yet familiar with the technology.
II. LITERATURE SURVEY
The identification of counterfeit products has become a significant issue in recent years. According to the Global Brand Counterfeiting Report 2018, the global value of counterfeiting has reached $1.2 trillion. Counterfeiting can cause significant damage to the brand reputation, financial loss, and even pose a risk to public health and safety. The use of blockchain technology has emerged as a potential solution to combat counterfeiting.[3]Blockchain technology is a distributed ledger technology that provides a secure and transparent way to record transactions. This paper provides a literature survey of the identification of counterfeit products using blockchain technology.
Blockchain technology has been proposed as a potential solution to identify and track counterfeit products. Several studies have proposed various blockchain-based solutions for the identification of counterfeit products.
One study proposed a blockchain-based solution for identifying counterfeit drugs. The solution uses blockchain technology to track the supply chain of pharmaceutical products.[4] The blockchain is used to record the movement of drugs from the manufacturer to the end consumer. The solution also includes a mobile application that allows consumers to scan the drug's barcode and verify its authenticity. The study concludes that the blockchain-based solution can effectively identify counterfeit drugs and prevent their circulation in the market. Another study proposed a blockchain-based solution for identifying counterfeit luxury goods.[5]The solution uses blockchain technology to record the entire supply chain of luxury goods. The blockchain is used to track the movement of goods from the manufacturer to the end consumer. The solution also includes a mobile application that allows consumers to scan the product's barcode and verify its authenticity. The study concludes that the blockchain-based solution can effectively identify counterfeit luxury goods and prevent their circulation in the market.
A study proposed a blockchain-based solution for identifying counterfeit food products. The solution uses blockchain technology to track the entire supply chain of food products.[6] The blockchain is used to record the movement of food products from the farmer to the end consumer. The solution also includes a mobile application that allows consumers to scan the product's barcode and verify its authenticity. The study concludes that the blockchain-based solution can effectively identify counterfeit food products and prevent their circulation in the market.
Another study proposed a blockchain-based solution for identifying counterfeit electronics products.[7] The solution uses blockchain technology to track the entire supply chain of electronics products. The blockchain is used to record the movement of electronics products from the manufacturer to the end consumer. The solution also includes a mobile application that allows consumers to scan the product's barcode and verify its authenticity. The study concludes that the blockchain-based solution can effectively identify counterfeit electronics products and prevent their circulation in the market.
III. RELATED WORK
Blockchain technology has been proposed as a potential solution for identifying counterfeit products due to its ability to create an immutable and transparent record of transactions. Here are some examples of related work in this area:
- "Blockchain for supply chain traceability: A case study of mango export from India" by Sangeeta Sharma and Sanjay Kumar Dhurandher (2019): This paper presents a case study on using blockchain technology for traceability of mango exports from India to Japan. The authors propose a blockchain-based system that uses QR codes to track the movement of mangoes through the supply chain, enabling consumers to verify the authenticity of the product.
- "Blockchain-based anti-counterfeiting in fashion and luxury industry" by Zhengyuan Xu, Shanyu Tang, and Zibin Zheng (2019): This paper proposes a blockchain-based system for the fashion and luxury industry to combat counterfeiting. The system uses a unique identifier for each product that is recorded on the blockchain, allowing consumers to verify the authenticity of the product using a smartphone app.
- "A blockchain-based approach to combating counterfeit drugs" by Michael E. Porter, Jr. and Pinar Ozcan (2018): This paper proposes a blockchain-based system for tracking pharmaceuticals through the supply chain to prevent counterfeit drugs from entering the market. The system uses a unique identifier for each drug that is recorded on the blockchain, enabling consumers to verify the authenticity of the product.
- "Blockchain for anti-counterfeiting in pharmaceutical industry" by Jiaqi Li, Xiaomin Liu, and Weiqi Dai (2020): This paper proposes a blockchain-based system for the pharmaceutical industry to prevent counterfeit drugs from entering the market. The system uses a unique identifier for each drug that is recorded on the blockchain, and it also includes a smart contract that ensures the authenticity of the product.
- "Blockchain for anti-counterfeiting in wine industry" by Rui Zhang, Xuehui Liu, and Jianqiang Zhang (2019): This paper proposes a blockchain-based system for the wine industry to prevent counterfeiting. The system uses a unique identifier for each bottle of wine that is recorded on the blockchain, enabling consumers to verify the authenticity of the product using a smartphone app.
Overall, these studies demonstrate the potential of blockchain technology for identifying counterfeit products across a range of industries. However, there is still much work to be done in developing and implementing effective blockchain-based systems for anti-counterfeiting.
IV. PROPOSED FRAMEWORK
Here is a proposed framework for identifying counterfeit products using blockchain technology:
- Product identification: Each product is assigned a unique identifier that is recorded on the blockchain. This identifier could be a QR code, a barcode, or an RFID tag.
- Supply chain tracking: The movement of the product through the supply chain is recorded on the blockchain. This includes information such as the date of manufacture, the location of each step in the supply chain, and the identity of the parties involved in each step.
- Authentication: Consumers can use a smartphone app or other device to scan the product identifier and verify its authenticity. The app would access the blockchain to retrieve the information recorded during the supply chain tracking phase and use this information to verify the product's authenticity.
- Anti-counterfeiting measures: The system can include additional measures to prevent counterfeiting, such as tamper-evident packaging or specialized tags that are difficult to replicate.
- Enforcement: In cases where counterfeit products are identified, the blockchain can be used to track the source of the counterfeit and help enforce legal action against those involved in the production and distribution of counterfeit products.
This framework would require collaboration between producers, distributors, and retailers to ensure that all relevant information is recorded on the blockchain. It would also require the development of consumer-facing apps or devices that can easily access the blockchain and authenticate products. Additionally, there would need to be legal mechanisms in place to enforce the identification and punishment of counterfeiters.
V. SYSTEM ARCHITECTURE
Here is a possible architecture for a blockchain-based system for identifying counterfeit products:
- Front-end applications: These are the applications used by consumers to authenticate products. The applications could be mobile apps, web apps, or other devices that can scan the unique identifier on the product and access the blockchain to retrieve information about the product's origin, history, and authenticity.
- Smart contract: A smart contract is a self-executing contract with the terms of the agreement between buyer and seller being directly written into lines of code. In this architecture, a smart contract could be used to ensure that all parties in the supply chain comply with the rules and regulations of the system. For example, the smart contract could specify the type of information that needs to be recorded on the blockchain at each step of the supply chain.
- Blockchain network: The blockchain network is where all the information about the product is stored in an immutable and transparent ledger. The blockchain could be a public blockchain or a private blockchain, depending on the requirements of the system. The blockchain could be implemented using any of the available blockchain technologies such as Ethereum, Hyperledger Fabric, Corda, etc.
- IoT sensors: The system could also include IoT sensors that could be used to track the product's movement through the supply chain. The sensors could track information such as temperature, humidity, and location, and record it on the blockchain.
- Data analytics and reporting: The system could include data analytics and reporting tools that could be used to analyze the data recorded on the blockchain. This could include identifying patterns in the movement of products, identifying potential counterfeiting hotspots, and generating reports on the system's performance.
Overall, this architecture is designed to ensure that all relevant information about the product is recorded on the blockchain and is accessible to consumers, producers, and regulators. By using smart contracts and IoT sensors, the system could help ensure that all parties in the supply chain comply with the system's rules and regulations, and provide consumers with a high level of confidence in the authenticity of the products they purchase.
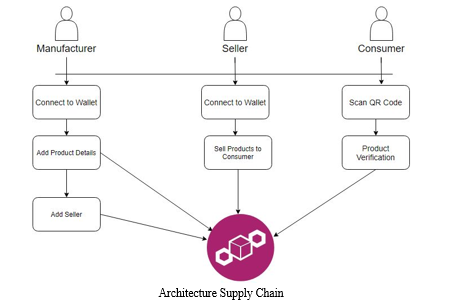
a. Manufacture: A block is added to the Ethereum blockchain using the manufacturer's Ethereum wallet after logging into the manufacturer account to create a QR code for the product and add any further information that is necessary. If both are present, a connection will be made between the wallet addresses of the entity and the user of our local database. If just the block is published to the digital ledger, the manufacturer will enter data from his own account and wallet.
b. Supplier: After entering into their account as a supplier, the product's QR code is scanned by the supplier. The manufacturer's entered product information is available to the seller. It injects extra information about the item—like the shop's location—into the Blockchain. These details are visible to the buyer.
c. Customer: Customers can scan a QR code that details the history of transactions and enables them to examine the integrity of a product to confirm its authenticity. The client will be aware that the goods are not genuine if the final location is different from the purchase location at the time of the customer's purchase following the QR scan in the supply chain history. After learning about counterfeiting, the purchaser comes to the conclusion that the QR code was stolen.
d. QR Code: QR codes can be used as a unique identifier for products in a blockchain-based system for identifying counterfeit products. Here is how it could work:
- Assign a unique QR code to each product: Each product is assigned a unique QR code that is printed on the product or its packaging.
- Record the QR code on the blockchain: The QR code is recorded on the blockchain, along with other relevant information such as the date of manufacture, the location of each step in the supply chain, and the identity of the parties involved in each step.
- Authenticate the product using the QR code: Consumers can use a smartphone app to scan the QR code and authenticate the product. The app would access the blockchain to retrieve the information recorded during the supply chain tracking phase and use this information to verify the product's authenticity.
- Anti-counterfeiting measures: The system can include additional measures to prevent counterfeiting, such as tamper-evident packaging or specialized QR codes that are difficult to replicate.
- Enforcement: In cases where counterfeit products are identified, the blockchain can be used to track the source of the counterfeit and help enforce legal action against those involved in the production and distribution of counterfeit products.
Using QR codes in a blockchain-based system for identifying counterfeit products can provide a quick and easy way for consumers to authenticate products. It also allows for the efficient recording and tracking of product information on the blockchain, which can be used to enforce anti-counterfeiting measures and identify the source of counterfeit products.
VI. SCM AND BLOCKCHAIN TECHNOLOGY
Supply chain management (SCM) and blockchain technology can work together in a system for identifying counterfeit products.[8] Here is how they could be integrated:
- Record the supply chain on the blockchain: The movement of the product through the supply chain is recorded on the blockchain, including information such as the date of manufacture, the location of each step in the supply chain, and the identity of the parties involved in each step.
- Ensure transparency and traceability: By recording the supply chain on the blockchain, the system can provide transparency and traceability, allowing all parties involved in the supply chain to access the same information.
- Use smart contracts to enforce rules and regulations: Smart contracts can be used to ensure that all parties involved in the supply chain comply with the rules and regulations of the system. For example, the smart contract could specify the type of information that needs to be recorded on the blockchain at each step of the supply chain.
- Authenticate products using blockchain technology: Consumers can use a smartphone app to scan a unique identifier on the product and access the blockchain to retrieve information about the product's origin, history, and authenticity.
- Use data analytics to identify potential counterfeiting hotspots: The system can include data analytics tools that can analyze the data recorded on the blockchain to identify patterns in the movement of products and potential counterfeiting hotspots.
By combining SCM and blockchain technology, the system can provide a high level of transparency and traceability throughout the supply chain, making it easier to identify the source of counterfeit products.[9]The use of smart contracts can also help ensure that all parties in the supply chain comply with the rules and regulations of the system, and the use of data analytics can help identify potential counterfeiting hotspots, enabling proactive measures to be taken to prevent counterfeit products from entering the supply chain.
Conclusion
A blockchain-based system for identifying counterfeit products can provide a high level of transparency, traceability, and security throughout the supply chain. By recording information about the product\'s origin, history, and authenticity on an immutable and transparent ledger, consumers can easily authenticate products using a smartphone app, increasing their confidence in the products they purchase. The use of smart contracts and IoT sensors can also help ensure that all parties in the supply chain comply with the system\'s rules and regulations, preventing counterfeit products from entering the supply chain. In conclusion, the integration of blockchain technology in the fight against counterfeit products has the potential to revolutionize supply chain management and consumer protection. By providing a reliable, secure, and decentralized system for tracking and authenticating products, blockchain can help reduce the prevalence of counterfeit products and increase consumer trust. However, implementing such a system requires collaboration among various stakeholders, including producers, retailers, regulators, and consumers, to ensure the system\'s success. Further research and development are needed to address the technical, social, and economic challenges of implementing a blockchain-based system for identifying counterfeit products.
References
[1] N. Satoshi, Bitcoin: A Peer-to-Peer Electronic Cash System, (2008). [2] J. Leng, P. Jiang, K. Xu, Q. Liu, J. L. Zhao, Y. Bian, and R. Shi, ‘‘Maker chain: A blockchain with chemical signature for self-organizing process in social manufacturing,’’ J. Cleaner Prod., vol. 234, pp. 767–778, Oct. 2019. [3] JINHUA MA 1, SHIH-YA LIN 2, XIN CHEN 1, HUNG-MIN SUN 2, YEH-CHENG CHEN 3, (Graduate Student Member, IEEE) AND HUAXIONG WANG 4 A Blockchain-Based Application System for Product Anti-Counterfeiting (2020). [4] Satoshi Nakamoto, Bitcoin: A Peer-to-Peer Electronic Cash System retrieved from bitcoin.org, (2009). [5] N. Alzahrani, Block-supply chain: A brand-new anti-counterfeiting supply chain using NFC and blockchain, (2018). [6] C. Shaik, Computer Science & Engineering: An International Journal (CSEIJ), 4, (2021). [7] Atlanta, Georgia, USA, Tech. Rep. Press 12. Hargreaves, S.: \"Counterfeit goods growing in risk,\" CNN Money, (2012). [8] S. F. Roy and M. Jerremy, \"African Counterfeit Pharmaceutical Epidemic: The Road Ahead,\" ACAPPP, 2009. [9] \"WHO | Growing Threat from Counterfeit Medicines,\" Bulletin of the World Health Organization, vol. 88, no.4, pp, 2010. [10] Hult, G. Tomas M., D. J. Ketchen, and M. Arrfelt. \"Strategic supply chain management: Improving performance through a culture of competitiveness and knowledge development.\" Strategic Management Journal, vol. 28, 2007, pp. 1035–1052. [11] Wang, William Y. C., and H. K. Chan. \"Virtual organization for supply chain integration: Two cases in the textile and fashion retailing industry.\" International Journal of Production Economics, vol. 127, 2010, pp. 333-342. [12] Sturm LD, Williams CB, Camelio JA, White J, Parker R (2014) Cyberphysical vulnerabilities in additive manufacturing systems. (SFF) Symposium pp: 951–963. [13] Turner H, White J, Camelio JA, Williams C, Amos B, et al. (2015) Bad parts: are our manufacturing systems at risk of silent cyberattacks?. IEEE Secur Priv 13: 40–47. [14] Vincent H, Wells L, Tarazaga P, Camelio J (2015) Trojan detection and side-channel analyses for cyber- security in cyber-physical manufacturing systems. Procedia Manuf 1: 77–85. [15] Ang, K.H., Chong, G., Li, Y.: Visualization Technique for Analyzing Non- Dominated Set Comparison. In: 4th Asia-Pacific Conference on Simulated Evolution and Learning (SEAL 2002), Singapore, vol. 1, pp. 36-40 (2002) [16] Lien, S.Y., Shieh, S.L., Huang, Y., Su, B., Hsu, Y.L., Wei, H.Y.: 5G new radio: waveform, frame structure, multiple access, and initial access. IEEE Commun. Mag. 55(6), 64–71 (2017)
Copyright
Copyright © 2023 Sahil Bhosale, Aditya Bhosale, Sreerag Nair, Arjun Mohan, Prof. Anita Patil. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET52715
Publish Date : 2023-05-22
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

