Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Exploring the Evolving Landscape of Cybercrime in India and Strategies for Prevention
Authors: Kirti ., Dr. Jyoti Singh
DOI Link: https://doi.org/10.22214/ijraset.2023.53624
Certificate: View Certificate
Abstract
Cybercrime refers to criminal activities that either target computers or networks such as hacking, phishing, and spamming, or involve the use of computer to commit offensive and illegal activities, such as hate crimes and child pornography. The research aims to explore the evolving landscape of cybercrime in India along with Indian cybercrime statistics, motives behind cybercrimes like fraud, extortion, sexual exploitation, terrorist activities, Inciting Hate against Country, Sale Purchase illegal drugs, etc. In addition, the paper will delve into specific types of cybercrime, unique challenges, and strategies for prevention of same. The paper investigates cybercrimes reported in India from 2016 to 2020 under the IT Act 2000 and Indian Penal Code (IPC), identifying both persistent and emerging types of cybercrimes, Police, and court Disposal of Cyber Crime Cases. The research design for this study will be a review type and will use both qualitative and quantitative data analysis techniques to present a bibliographic overview of the evolving landscape of cybercrime in India. The data analysis process will involve using statistical techniques to summarize the data and present it in a meaningful way. The findings of this research will be useful for policymakers, law enforcement agencies, and other stakeholders in the fight against cybercrime in India. This article will serve as the data set for various studies associated with the digital forensic investigations.
Introduction
I. INTRODUCTION
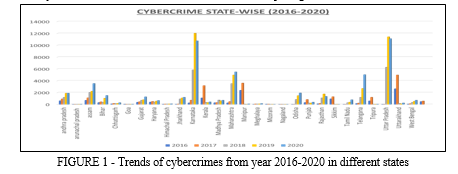
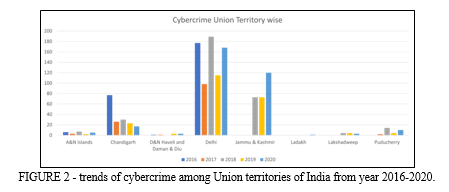
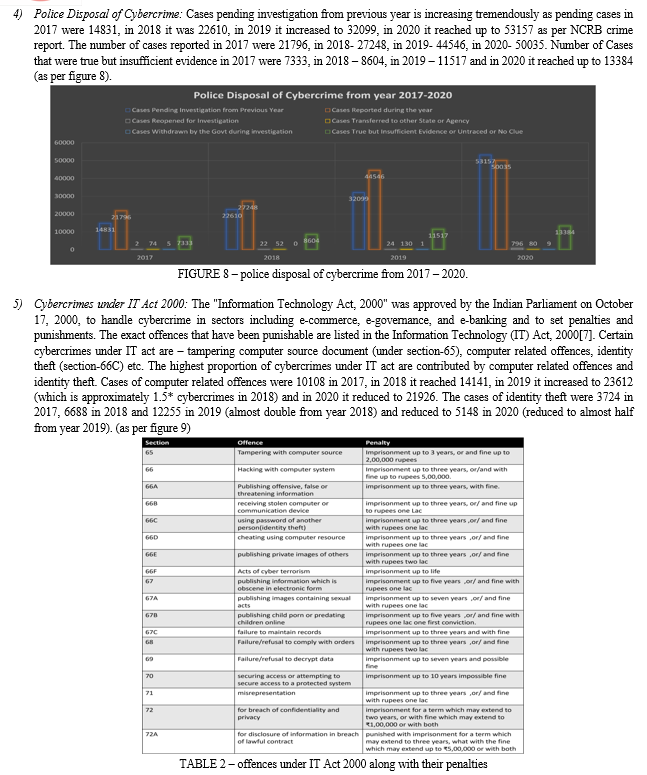
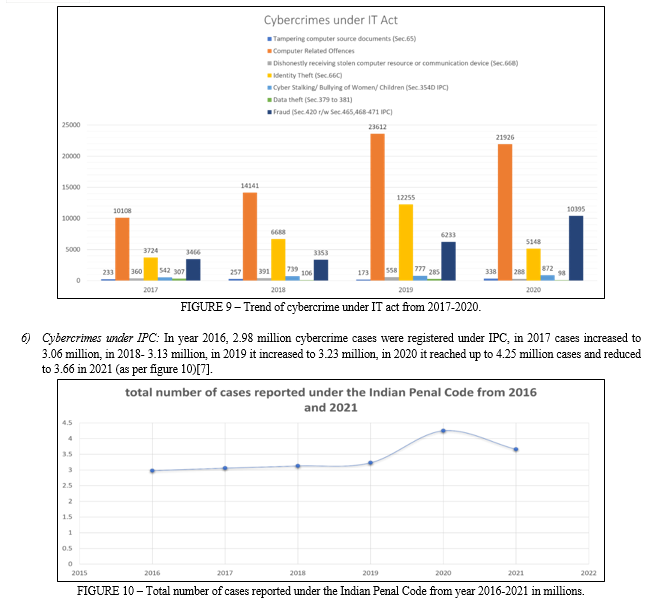
Cybercrimes are modern offences committed through the use of electronic devices. Electronics are now a commonplace aspect of daily life and are regarded as the fourth fundamental element after oxygen, food, and shelter. Unfortunately, because of users' lack of awareness and education, behaviors like extortion, stalking, bullying, harassment, and even acts that result in suicide have become frequent. Due to the lack of the essential tools, technology, and cyber professionals, our ability to tackle cybercrimes is substantially behind. In the meantime, criminals constantly develop and create new types of cybercrimes, surpassing our capacity.[1] The escalating proliferation of abusive content on social media platforms is a troubling issue. Over the past five years (from 2016-2020), the number of reported cybercrime cases has shown a significant upward trajectory: 12,317 cases in 2016, 21,796 cases in 2017, 27,248 cases in 2018, 44,735 cases in 2019, and 50,035 cases in 2020. This trend raises serious concerns and calls for effective measures to address the problem. States like Karnataka, Uttar Pradesh, Maharashtra[2], and Telangana have shown rapid increase in cybercrime in years 2019-2020 as the crime rate has almost doubled due to increased use of online platform during Covid-19 and due to lowering of cyber defenses as major focus of authorities was on health crisis (as per figure-1). Union territories like A&N islands and D&N haveli and Daman and Diu, Ladakh and Lakshadweep have very less almost negligible cybercrime rates whereas Chandigarh, Delhi and Jammu and Kashmir are the top among cybercrime trends in Union Territories. Delhi and Chandigarh cover all the cybercrime under IT act, the IPC act and SLL (as per figure 2)
II. DATA COLLECTION METHOD -
To gather information on cyber-crimes recorded between the years 2016 and 2020 under the IT Act 2000 and the Indian Penal Code, secondary data was collected from the National Crime Records Bureau website[3]. Additionally, secondary data was obtained from the 'Cyber Security' article published by NITI Aayog to examine emerging crimes reported between 2016 and 2020. In order to capture the evolving internet usage in India, secondary data was sourced from various websites including internetlivestats, Statista, and iamai.
III. DATA ANALYSIS METHOD
A trend analysis was conducted to determine the proportion of internet users across India and study the growth of internet usage from 2016 to 2020. Furthermore, a trend analysis was performed on the number of cyber-crimes recorded under the IT Act 2000 and the Indian Penal Code[3]. The cybercrime trend was recorded and analyzed on the basis of motives, cybercrimes trends against women and children, police disposal of the cybercrime. To analyze the newly emerging cyber-crimes and illustrate the distribution of recent cyber-crimes in 2016-2020, 2D bar charts were utilized.
IV. RESULTS AND DISCUSSION
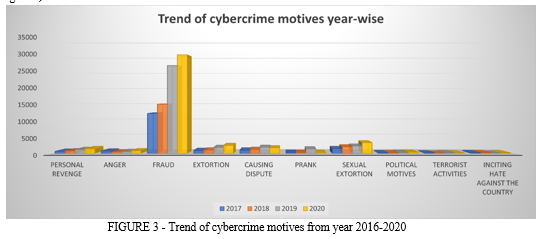
- Cybercrime Motive: The primary motivation for cybercrime is monetary and financial gain without being present at the scene of crime using a virtual identity. Various types of cybercrime motives are personal revenge, anger, fraud, extortion, causing dispute, prank etc., with majorly being contributed by fraud as per the data provided by the states to NCRB. Computer fraud is a malicious attack with an intent to either steal data or to retain someone’s personal information for monetary or financial gain[4]. As per the data provided by the states and union territories to the NCRB, Uttar Pradesh constitutes the highest fraud rate, then Karnataka and then Maharashtra which almost doubled from year 2018 to year 2019 and rate keeps on increasing in 2020 also (as per figure 3).
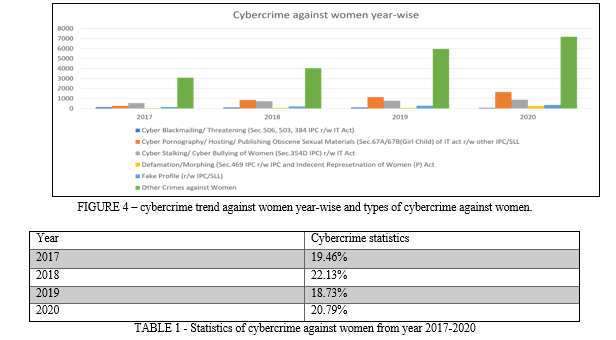
2. Cybercrime Against Women: Crimes against women have persisted throughout history, encompassing various forms such as the Sati system, dowry-related offenses, cruelty, domestic violence, and rape. Despite 70 years of independence and numerous studies and reports, these crimes against women continue to rise. In the modern age, cybercrime targeting women has emerged as a new form of offense, involving acts committed through electronic medium. Different categories of cybercrimes committed against women are cyber blackmailing or threatening or fake profile etc., with majority of which contributed by cyber pornography or publishing obscene materials and cyber stalking and cyber bullying (as per figure 4). According to the most recent NCRB report, there were 4,242 cases of cybercrimes against women reported in 2017, 6,030 cases in 2018, 8,379 cases in 2019, and 10,405 cases in 2020. 7,184 of the incidents that were reported in 2020 were classified as "other crimes," which shows that India lacks specialized legislation to address cybercrimes against women[5]. With 1,655 recorded incidents, cyberpornography/hosting/publishing obscene sexual materials was the most common sort of cybercrime, followed by cyberstalking/bullying with 887 cases. The biggest number of cases against women were reported in Karnataka (2,859), followed by Maharashtra (1,632 instances) and Assam (1,071 cases), in that order. [5]
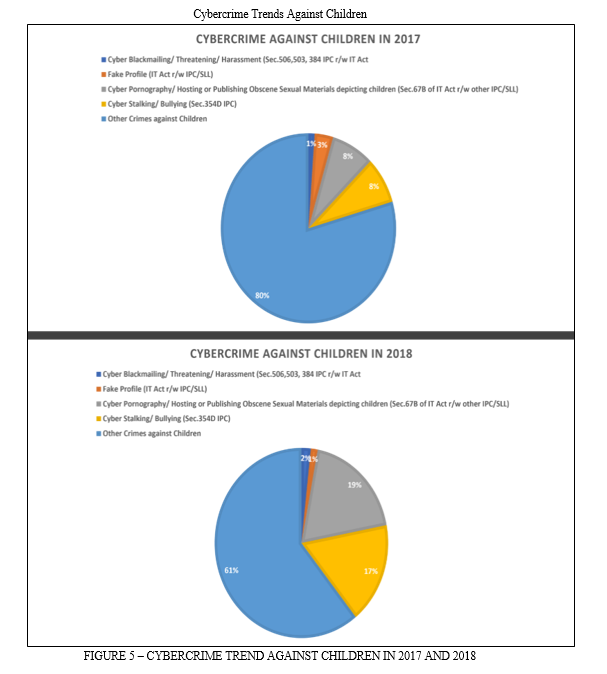
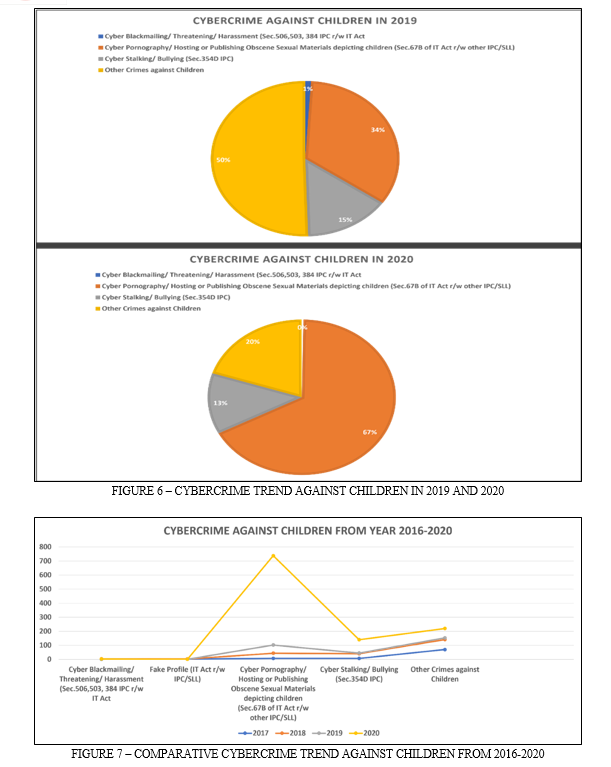
3. Cybercrime against children- Cybercrime against children has become a grave concern in today's digital age. With the rapid advancement of technology and the widespread use of the internet, children are increasingly vulnerable to various forms of online exploitation, abuse, and harassment. Cybercriminals target children with malicious intent, causing significant harm to their emotional, psychological, and physical well-being. It is crucial to understand the reasons behind these crimes, analyze the trends state wise, delve into the motives of offenders, and discuss effective prevention measures. Several factors contribute to the rise of cybercrime against children. The anonymity and accessibility of the internet make it easier for offenders to exploit unsuspecting children.[6] The lack of awareness and digital literacy among both children and parents adds to the vulnerability. Moreover, the rapid growth of social media platforms, online gaming, and messaging apps has created ample opportunities for perpetrators to groom and exploit children. In 2017 and 2018, 80% crimes still classified as other cybercrimes against children as no specified legislation for their classification, 8% of cybercrime constituted by cyber pornography or publishing obscene sexual materials depicting children and cyberstalking and cyberbullying also constitute 8%, cyber blackmailing constitutes 1% and fake profile constitute 3% (as per figure 5). In 2019, 50% crimes classified as other cybercrimes against children, 34% of cybercrime constituted by cyber pornography or publishing obscene sexual materials depicting children which is the second highest and cyberstalking and cyberbullying constituting 15%. The depiction of cybercrime against children in 2020 highlights a significant shift in trends. The majority of these crimes, accounting for 67%, were attributed to cyber pornography or the distribution of explicit sexual material involving children. This represents a notable increase, making cyberpornography the most prevalent form of cybercrime against children. On the other hand, the category of "other" cybercrimes against children, which held the highest percentage in 2017-2019, now occupies the second position with a reduced rate of 20%. Cyberstalking and cyberbullying make up 13% of the reported cases, placing them as the third most common types of cybercrimes against children (as per figure 6).
V. STRATIGIES FOR PREVENTION OF CYBERCRIME
Preventing cybercrime involves following security guidelines and implementing best practices. The following recommendations can help minimize security risks:
- Regularly Update Computer Systems: Keep operating systems and antivirus software up to date. While this won’t provide complete protection, it significantly reduces the chances of hackers gaining unauthorized access, blocks many basic attacks, and enhances overall security.[8]
- Utilize Secure Passwords: Choose passwords with at least eight characters, a mix of letters, numbers, and symbols (for example, # $%!?), and at least one symbol. Instead, using information that may be easily guessed, such as names or city names, use non-dictionary words. Keep your passwords secure and avoid using the same password on several internet accounts. It is advisable to update passwords once every 90 days.
- Install Security Software: Utilize security software such as firewalls and antivirus programs. Firewalls control online communication and determine who or what can access your computer. Antivirus software keeps track of internet actions and protects users from viruses, worms, Trojan horses, and other harmful software. Every time you connect to the Internet, set up your antivirus and antispyware software to update itself automatically.[8]
- Protecting Individual Information: Take security measures to safeguard sensitive data while disclosing personal information online.
Follow these guidelines:
a. Be cautious of phishing messages that pressure you to act quickly or threaten negative consequences. Ignore and do not respond to such messages.
b. Legitimate companies do not request personal information via email, so avoid responding to email requests for personal data.
c. Instead of clicking on links within emails or instant messages, manually type the URL into your web browser when visiting websites.
d. Protect your email address from unsolicited emails and spam.
5. Exercise Caution with Online Offers: Beware of offers that seem too good to be true, as they may involve bundled advertising software that tracks your behavior or displays unwanted ads. Exercise caution when downloading free software or services.
6. Regularly Review Bank and Credit Card Statements: Identity theft and online crimes can be mitigated by promptly detecting any suspicious activity. Regularly monitor bank and credit card statements for any unauthorized transactions. Many financial institutions employ fraud prevention systems that alert you to unusual purchase patterns.
7. Be Social Media Savvy: Adjust the privacy settings of social networking profiles, such as Facebook or Twitter, to private. Regularly review and modify security settings. Exercise caution when sharing personal information online.
8. Mobile Devices Should be Secured: Be aware that viruses and hacking efforts might affect mobile devices. Only download software via reliable sources.
9. Wireless Network Should be Secured: Ensure that your home Wi-Fi network is properly secured. Review and modify default settings to prevent unauthorized access. Avoid using public Wi-Fi networks, as they can pose security risks.[8]
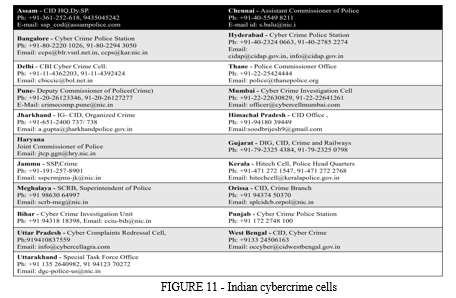
10. Seek Assistance from Cybercrime Cells: To address cybercrime incidents, law enforcement agencies in India have established cybercrime investigation cells nationwide. These specialized units focus on looking into a variety of cybercrimes, such as hacking, virus distribution, pornography, account manipulation, data alteration, software piracy, fraudulent websites, the creation of counterfeit money and visas, the theft of intellectual property, email spam, denial of access, password theft. The table below lists the contact information for numerous active cybercrime cells present in India, including contact details and email addresses:
VI. FUTURE CHALLENGES
- Evolving Technology: Rapid technological advancements create new opportunities and challenges for cybercriminals. Emerging technologies like artificial intelligence, Internet of Things (IoT), and quantum computing introduce vulnerabilities that can be exploited. Developing effective security measures becomes crucial in combating cybercrime.
- Increasing Sophistication of Cyber Attacks: Cybercriminals are becoming more sophisticated in their tactics, making it challenging to detect and prevent cyber-attacks. Advanced persistent threats (APTs), ransomware attacks, and zero-day exploits bypass traditional security measures. Proactive defense strategies and advanced cybersecurity solutions are necessary to counter evolving threats.[9]
- Insider Threats: Individuals within organizations exploiting access privileges pose a significant challenge. Insiders may intentionally leak sensitive information, engage in financial fraud, or sabotage computer systems. Identifying and mitigating insider threats requires robust security protocols, employee training, and effective monitoring systems.
- Cybersecurity Skills Gap: The shortage of skilled cybersecurity professionals globally hinders efforts to combat cybercrime effectively. Organizations struggle to find qualified professionals to fill cybersecurity roles. Addressing the skills gap requires increased investments in cybersecurity education, training programs, and industry collaboration.
- Cross-Border Jurisdictional Challenges: Cybercrime transcends borders, creating challenges in terms of jurisdiction and international cooperation for law enforcement agencies. Coordinating efforts, sharing intelligence, and establishing effective legal frameworks for international cooperation are crucial in tackling cross-border cybercrime.
- Cloud Security: As cloud computing adoption increases, securing cloud-based systems and data becomes critical. Cloud services introduce new security risks, such as data breaches, misconfigurations, and unauthorized access. Robust cloud security measures, including strong access controls, encryption, and regular security audits, are vital to protect sensitive data.
- Social Engineering Attacks: Social engineering attacks, such as phishing and social media manipulation, remain prevalent and effective. Cybercriminals exploit human psychology to manipulate individuals into divulging sensitive information or performing certain actions. Raising awareness, implementing multi-factor authentication, and providing cybersecurity training can help mitigate the risks associated with social engineering attacks.
- Internet of Things (IoT) Security: Securing interconnected IoT devices presents a significant challenge. IoT devices often lack adequate security measures and can serve as entry points for cyber-attacks. Strengthening IoT security standards, implementing robust authentication mechanisms, and regularly updating firmware and software patches are essential to mitigate IoT-related risks.
- Data Privacy and Compliance: Data privacy regulations impose strict requirements on organizations to protect individuals' personal data. Ensuring compliance with regulations like GDPR and CCPA while safeguarding sensitive data poses complexity. Establishing comprehensive data privacy frameworks, implementing privacy-by-design principles, and conducting regular privacy audits are crucial.[9]
- Emerging Threats in Critical Infrastructure: Critical infrastructure systems, such as power grids and transportation networks, are increasingly vulnerable to cyber-attacks. Disrupting critical infrastructure can have severe consequences for public safety and national security. Strengthening cybersecurity, conducting risk assessments, and developing incident response plans specific to critical systems are essential to mitigate these threats.
VII. RECOMMENDATIONS
- Strengthen Legislation and International Cooperation [10]: Governments should continuously update and strengthen cyber laws to keep pace with emerging threats. International cooperation and information sharing among law enforcement agencies are crucial for combating cross-border cybercrime.
- Enhance Cybersecurity Awareness and Education: Promoting cybersecurity awareness among individuals, businesses, and organizations is vital. Educating users about best practices, such as using strong passwords, updating software, and recognizing phishing attempts, can significantly reduce the risk of falling victim to cybercrime.
- Invest in Cybersecurity Infrastructure: Governments and organizations should allocate resources to develop robust cybersecurity infrastructure. This entails putting in place cutting-edge security measures like firewalls, antivirus software, and encryption as well as performing frequent security assessments.
- Foster Public-Private Partnerships: Collaboration between governments, law enforcement agencies, and the private sector is essential for effectively combating cybercrime. Public-private partnerships can facilitate information sharing, joint investigations, and the development of innovative cybersecurity solutions.
- Strengthen Cybercrime Investigation and Forensics Capabilities: Law enforcement agencies need to enhance their cybercrime investigation and digital forensics capabilities. This includes training personnel in cybercrime investigation techniques, establishing specialized cybercrime units, and investing in advanced forensic tools and technologies.
- Promote Ethical Hacking and Bug Bounty Programs: Encouraging ethical hacking and bug bounty programs can help identify vulnerabilities in computer systems and networks. Offering rewards to individuals who responsibly disclose vulnerabilities can incentivize proactive cybersecurity measures.
- Raise Awareness on Cybercrime Impact: Governments, NGOs, and educational institutions should raise awareness about the impact of cybercrime on individuals, businesses, and society. This includes highlighting the potential financial, emotional, and reputational consequences of cybercrime.
Conclusion
1) In conclusion, this research paper delves into the evolving landscape of cybercrime in India and proposes strategies to prevent and combat this growing threat. The findings emphasize the urgent need for proactive measures and increased awareness about cybercrime among individuals, organizations, and government bodies. Understanding the various forms of cybercrime prevalent in India is crucial for effectively identifying and mitigating potential risks. This necessitates targeted awareness campaigns, educational initiatives, and the dissemination of best practices for online safety and security.[1] 2) The research highlights the significance of investing in robust cybersecurity infrastructure, urging both public and private organizations to implement comprehensive security measures to safeguard critical systems and sensitive data. This includes the deployment of encryption technologies, firewalls, intrusion detection systems, and regular security audits. Fostering a cybersecurity culture within organizations promotes a proactive approach to risk management. 3) Addressing the shortage of skilled cybersecurity professionals is a critical concern, and bridging the expertise gap requires partnerships between educational institutions, industry associations, and government bodies. Specialized cybersecurity training programs, certifications, and internships can equip individuals with the necessary skills to detect, prevent, and respond to cyber threats effectively.[3] 4) Collaboration between the public and private sectors is essential for an effective prevention and response strategy. The research advocates for information sharing platforms, public-private partnerships, and joint efforts between law enforcement agencies, industry associations, and cybersecurity experts. Sharing intelligence, resources, and best practices enhances the collective ability to detect and disrupt cybercriminal activities. 5) Furthermore, the research emphasizes the need to strengthen legal frameworks and legislation to keep pace with evolving cyber threats and enable swift prosecution of cybercriminals. Regular review, amendment, and introduction of new laws are vital to address emerging challenges. 6) In conclusion, combatting cybercrime in India requires a multi-faceted approach encompassing awareness, technological advancements, skill development, collaboration, and robust legal measures. By adopting a proactive stance and implementing the strategies outlined in this research, India can enhance its cybersecurity posture, protect its citizens, businesses, and critical infrastructure, and create a safer digital environment for all.
References
[1] N. Jain, “‘CYBER CRIME CHANGING EVERYTHING-AN EMPIRICAL STUDY,’” International Journal of Computer Application Issue 4, vol. 1, 2014 [2] Ieee and Ieee, 2013 International Conference on Intelligent Systems and Signal Processing (ISSP). [3] M. R. Shah, “CYBER CRIMES IN INDIA: TRENDS AND PREVENTION,” International Journal of Research and Analytical Reviews, 2019, [Online]. Available: [4] Amity University, Amity University. Amity Institute of Information Technology, Institute of Electrical and Electronics Engineers. Uttar Pradesh Section, and Institute of Electrical and Electronics Engineers, ICRITO’2020 : IEEE 8th International Conference on Reliability, Infocom Technologies and Optimization (Trends and Future Directions) : conference date: 4-5 June 2020 : conference venue: Amity University, Noida, India. [5] A. Kabi, A. Marisport, S. Gori, and A. Singh Tomar, “The Facets Of Cyber Crimes Against Women In India: Issues And Challenges.” [Online]. Available: [6] T. J. Holt and A. M. Bossler, “The Palgrave Handbook of International Cybercrime and Cyberdeviance. [7] “Cyber Laws in India.” [8] V. Kandpal and R. K. Singh, “Latest Face of Cybercrime and Its Prevention In India,” International Journal of Basic and Applied Sciences Kandpal & Singh, vol. 2, no. 4, pp. 150–156, 2013, [Online]. Available: [9] J. Iqbal, “Cybercrime in India: Trends and Challenges,” 2017. [Online]. Available: http://www.coe.int/cybercrime [10] D. Gupta and N. Agrawal, “Global Journal of Enterprise Information System Empirical Study of Cyber Crimes in India using Data Analytics”, doi: 10.18311/gjeis/2018/19960
Copyright
Copyright © 2023 Kirti ., Dr. Jyoti Singh. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET53624
Publish Date : 2023-06-02
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

