Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
I Am Here: Privacy Aware Support
Authors: Mohammad Kaosain Akbar, Dibya Prokash Sarkar, Emrul Kaiser
DOI Link: https://doi.org/10.22214/ijraset.2022.46776
Certificate: View Certificate
Abstract
There is a growing concern about supporting general people with location awareness applications, mainly when a person is in a vulnerable situation. The current rise of challenging situations where the number of cases of sexual abuse, kidnap, and murders have taken place in Bangladesh, location-aware solutions are considered to handle the ongoing concerns. However, location sensitivity requires to be privacy sensitive to ensure safety to individuals seeking help. There is a design requirement around flexibility to abstract one’s location to different sets of people. An android based mobile system on supporting location abstraction to ensure privacy is presented here featured as “I am Here.” The design process involved inquiries from 84 individuals (51 female). The system has been deployed and evaluated in four different regions of urban and rural setup on 107 individuals (57 female). CCS Concepts H.5.m. Information interfaces and presentation (e.g., HCI): Miscellaneous.
Introduction
I. INTRODUCTION
In recent years, there has been a requirement for support and monitoring systems that can protect one in an unfavorable situation. Recent incent of Khashoggi murder [45] and the clues recorded on his apple watch is an example of how technology can play an important role. In countries suffering from political instability, an increase in the number of crime, social, and cultural problems relating to sexual harassment requires technology support to ensure citizens’ better living. Ongoing cases of sexual harassment and increased awareness level have initiated community support, along with technology-based support systems [34, 37, 42, 43, 41]. The problem of ensuring location-based support is considered in the context of Bangladesh, where the number of murders, kidnapping has increased over time. A father’s last call before he was murdered followed by his daughter’s desperate voice calling “Baba (daddy), baba (daddy) are you crying?” was recorded on a phone which was revealed by the media later [24]. It opened up the necessity to be able to leave trails in case of anticipated danger. There have been several attacks on women, some of which have resulted in murders [22], that show the ongoing requirement for the support system. Technology-based on-location services can play an important role in seeking help in probable and imminent danger. However, revealing technology can place the person in need in a vulnerable situation if that information reaches the wrong person. We have worked on a system that balances security calls preserving the privacy of users in the context of Bangladesh.
There have been solution approaches designed to support victims of harassment designed to engage a community [34, 37, 42, 43, 41] to achieve social justice. The role of technology in these support systems was on creating a platform of trusted community building or developing ways to seek support. Social-cultural barriers [34, 36], limited access to technology [14, 46] required a solution that remains in a closed community in the context of Bangladesh. Our current work considers such requirements for women. A solution that is able to seek help, along with keeping trails of a person in danger, can be helpful to support the person. We have added ways to abstract user’s exact location in a way that is preferable to the user giving the application user full control to abstract the user. Location information can introduce vulnerabilities if it is revealed to undesirable people. The weak law enforcement system that is often influenced by the use of power and or money [34] requires ways to abstract information.
We have initiated our design through user-centric design principles. We have conducted a qualitative study on 84 people whom we contacted through snowball sampling [47]. The design considered multiple alternatives where we worked carefully to support users and preserve user’s privacy, which was a significant concern among participants. There was a countrywide student protest going on right after our development process [48]. The protest was based on requirements for safer road conditions and better law enforcement system when two students were run over the bus. Some protesting students were attacked, and later some were locked up in prison prior to facing trials. The uncertainty, fear, and eagerness to seek help put our work in a proper context. We were able to ask more than 100 participants to try our solution approach. These participants included students, parents, family members, and many others from known connections. Our work is an effort to support general people facing suppression, harassment which may help them to seek social justice using technology as a medium.
In summary, contribution of our work is presented as follows:
- We explored user requirement on safety related application through a survey among 84 users (51 female)
- We have designed and developed an application that supports location services along with abstracting user information securing privacy that followed findings of user study
- A user evaluation of the system on 100 users along with system evaluation has been conducted to validate the system named I am Here
II. RELATED WORK
A. Context of Bangladesh
In 2016, a 19-year-old female college student, while returning to her residence, was assaulted by a group of men and then murdered inside the Comilla Cantonment. It was one of the major talks of the town at that particular period. This investigation is still ongoing, and the victim’s family is still waiting to get justice [22].
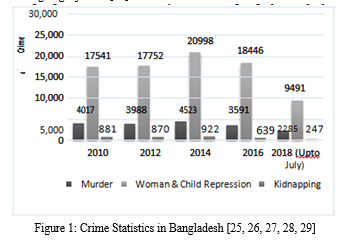
Another controversial killing took place recently in Cox’s Bazar, where the security force was directly involved, notably known as “Ekram killing” [24]. Security forces brought drug trafficking allegations against Mr. Ekram during the anti-narcotic drive. As a result, law enforcers kidnapped him from his residence and then shot him to death. However, an audio-clip was recorded when security forces shot Mr. Ekram, raised questions and criticisms against the government.
All these murders sparked social media and created nationwide protests against the alleged persons in Bangladesh, but it did not change the condition. Nevertheless, everyday rape incidents are taking place in different parts of the country, abduction, and events like murder are coming to the news headlines regularly. We analyzed past eight years of crime statistics from Bangladesh Police database (figure 2), where we found that women and child repression-like occurrences are increasing years after years, and it gives the real picture of how insecure women and children are in our society. From all these incidents, we decided to utilize the cellular device for personal safety, because in recent years’ number of smartphone users has increased. Moreover, it can help to raise public awareness to fight against these crime incidents and reduce the crime rate.
B. Mobile Application, Community Platforms
In recent times, harassment in streets and job spaces are increasing across the globe, and most of the victims are women. To tackle such occurrences, researchers and mobile app developers have made several efforts to fight against these crimes. With the advancement of information technology and cellular devices, people nowadays can quickly gather information from anywhere within a short time. Moreover, the number of smartphone users is rising because people can afford it easily. As a result, most of the researchers are now trying to develop mobile apps that can help not only to reduce street harassment and crime rates but also to raise awareness against them.
There are lots of community-based platforms and mobile apps, which are available in Google play store or iTunes. Whenever discussing community-based platforms, “Hollaback!” is one of them, which is developed by the Metropolitan Action Committee on Violence, a Canadian organization. It is specially developed for women to raise awareness against street harassment.
It is a social platform like Facebook, where users can share their harassment experiences. The main benefit of such social platforms is that it helps people know about different types of harassment across the world. Recently this organization has developed smartphone applications as well. This application allows users to share nearby street harassment incidents along with the location. Moreover, through this application, users can also do documenting and mapping [30].
Another mobile app with which users can share real-time location, along with the harassment experience the user has faced, is “Not your Baby.” METRAC, a community that is working on to fight against gender-based violence [31, 32], launched this application. Another notable community-based platform is “HarassMap”. It is developed in Egypt. The main feature of this web portal is that it helps the user to give an overview of different types of street harassments through a map. Besides that, it has a reporting option where users can report any harassment incidents through the web or cell phone [38].
“Circle of 6” is another mobile app developed for female users, where the user can send an alert message to her friends and trusted contacts whenever she is feeling threatened. This application is very famous among female users. In this application, user can set her preferred contacts, and specialty of this app is if the user taps screen twice, the app will send three text messages to the trusted contacts [39]. “bSafe” is another mobile app that works exactly same like Circle of 6, but here whenever user allows sending an emergency message to the preferred person at that time, it will send otherwise not [40].
There are more outstanding works, which are mainly developed to fights against street harassment. Among them “SafeStreet”, “HearMe”, “IPROB”, “MehfoozAurat” are notable [37, 42, 43, 41]. SafeStreet is a mobile application that is developed by a group of Bangladeshi researchers. In this app, there is a reporting option through what user can report any nearby harassment incidents. Moreover, it has a real-time location sharing option to trusted persons whenever the user feels trouble. Besides that, there is a map where the user chooses the preferred destination, and the app automatically suggests a safe route to reach the destination. Such a facility is beneficial, especially for women [37].
Apart from them, another noteworthy initiative that has been developed by Bangladeshi developers is “Protibadi.” It is a combination of community-based social platform and mobile app, which offers on spot emergency report option [34]. Moreover, it has options like sharing any experience of harassment and raise awareness.
Another application named “Hello CT” is a Bangladesh government-approved app where users can share any incident to Bangladesh Police without sharing their identity. Moreover, there is a real-time location sharing option, which has added more usability for the users [35]. “Bangladesh Emergency Service (BES)” is an application where people will get all the emergency phone numbers and emergency report options that will go to the nearby police stations. It made unique because it is developed in Bengali [36].
Moreover, there is a watch named “OnWatch,” which leads to providing a real-time location to the registered, trusted people if it senses an unwanted situation [33].
Above mentioned, all these mentioned applications’ primary and mutual mechanisms allow users to report or share the nearby harassment incidents through cell phones or web portals as well as to send emergency text messages or call to the preferred contacts whenever the user feels threatened while walking on the streets. According to ActionAid Bangladesh, most of the women remain silent after facing such crimes because of social disgrace [44]. In this paper, we have developed a mobile application named “I AM HERE”, where we have introduced a masking system by which users can share real-time location in some segments according to user’s preference.
Besides that, whenever the user feels threatened, the user can call trusted contacts or police. Moreover, this application can be used in Bengali as well.
III. METHODOLOGY
The inquiry that we needed for our project was focused on understanding the security issues of Bangladesh, the vulnerability of those issues, and acquiring help using mobile phone applications on sensing or being in danger. First, we took interviews of individuals and then gave them a survey containing ten sets of questions. The questionnaire was distributed among 40 participants, of whom 23 were men and 17 were women.
The survey was conducted from 28th June to 3rd July of 2018. In total, 8 hours of fieldwork was conducted, interviewing Faculties and Students from University campus and senior citizens at retirement homes and residences. Interview sessions and completing the survey for individuals took about 15 minutes on average. Each interview was concluded by asking the participants how they want to use the phone efficiently when they are in any danger, giving them a chance to present their views. Survey questions are provided at the end of this section.
A. Participant Recruitment
Participants were enlisted through personal contact using snowball sampling [47], retirement homes, and relatives at Residence. Before the survey and interview sessions, we stated the purpose of interviews and surveys. We provided the floor of rejecting the participation at any moment.
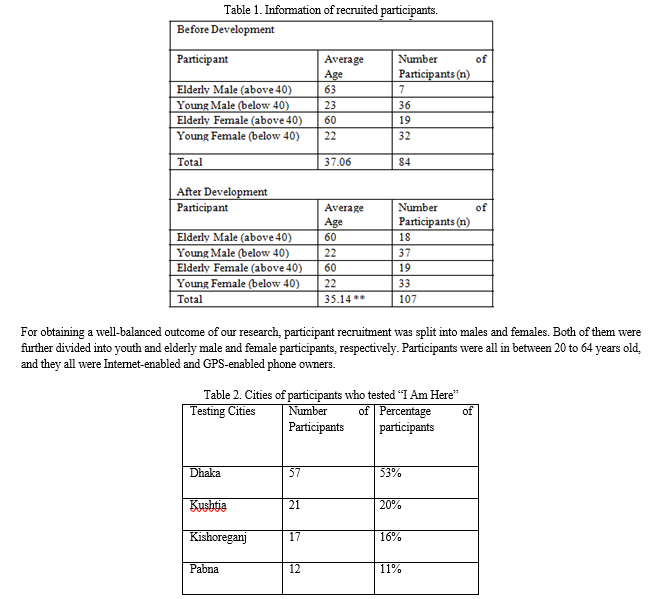
In the post-development test, “I Am Here” was provided to participants in various parts of the Dhaka City, namely Badda, Bashundhara Residential Area Baridhara DOHS, and Mohammadpur. In addition to Dhaka, the test was conducted in various districts such as Kishoreganj, Pabna, and Kushtia. Table 2 shows the cities and number of participants and their percentages who tested the application. About 53% of participants were from Dhaka City, where 57 participants tested and reviewed the application. 20% of participants were from Kushtia, followed by 17% and 12% from Kishoreganj and Pabna district, respectively.
- Survey (n=84): Before the development phase of the project, 84 participants were surveyed, among whom, 43 were male, and 41 were female. The participants were questioned whether they would prefer to use a cell phone while in any case of emergency or sense any danger around them. Participants were then asked whether they wanted their locations to be tracked, and even if they did, how much extent they would like to share it. Participants were also inquired if they would call a trusted contact in case of an emergency.
- Application Evaluation (n=107): In the after-development phase, we demonstrated and elaborated our application to 57 participants. We explained how the users could sign in to the application using both phone numbers and email addresses. We also explained how users could add a trusted contact and set various radius of respective contacts. Secondly, users were also guided on how to check the current location of trustee contact and the functionality of the emergency dial and logout feature. Tests were conducted on how different people use the application and how users might use it in case of any emergency
- Moderation and Incentive: The group members of the project conducted interviews and surveys. Thus, no incentives were required during this phase. All the participants whom we interviewed and surveyed participated voluntarily. At the start as well as at the end of the interviews and surveys, all the participants were thanked for their donated time.
- Research Ethics: For creating a neutral and comfortable environment based on participants’ preferences, we surveyed and interviewed youths at the university campus and elderly citizens at their residences. Participants were well informed about the purpose of our interviews and answers to the survey questionnaires. Participants also had the option of terminating the study at any time. Methods of recording were mostly notes. No pictures were taken during the interviews, and no interviews were recorded. All the participants were well aware that the project team will use their interviews and survey results. During the interviews, decency was maintained by both participants and project members.
IV. FINDINGS
After conducting surveys and interviews of participants of various ages, we observed different opinions. As most of our participants were young male and female, they were very much concerned with their privacy issues. For education and part-time jobs, they often remain outside of their homes and feel insecure. They do often feel the need to ask for help if they are passing by an empty street or quiet neighborhood. Since youth are very attached to their phones, they did show significant interest in sharing their locations, although there were different opinions regarding the range of their locations to be shared. On the other hand, older adults who stayed at home did not feel comfortable sharing their locations, but they did feel the need to contact in case emergencies they might face both indoors and outdoors.
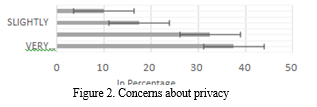
- Concerns about Privacy: Among all the participants’ majority of them were very much aware of the current security concerns about Bangladesh. Almost 37.5% of participants were very concerned about privacy and security issues, as shown in Figure 2. They stated their cautiousness about their surroundings. Additionally, 32.5 % of the participants were moderately concerned regarding privacy and securities. They know the threats but consider themselves to keep out of it. Moreover, about 17% were slightly concerned, and 10% were not concerned about it all. We can see that majority of the participants were very much or moderately concerned about the privacy and security issues.
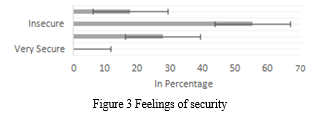
2. Feelings of Security: The participants stated various opinions regarding their security. 55% of the participants feel insecure, and additionally, of 18% feel insecure. They stated that constant news on television and newspapers about various crimes such as mugging, rape, kidnapping, made them feel very insecure when moving in the streets, as shown in Figure 3. Around 27% of the participants feel secure. These people said that they use personal cars and do not stay out of the house during the late hours. Interestingly, only 0% of people feel very secure, thus stating how insecure people feel showing the current situation in the country.
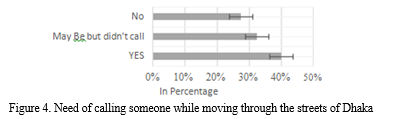
3. Connecting Others: The participants were also asked whether they feel the need to call someone while moving in the Dhaka city. Among them, 40% stated that they felt the need to call someone while roaming around Dhaka's streets. The other 33% stated that they felt the need but did not make any call. Most of them stated that they were very much nervous about making the call on such situations. The remaining 27% stated that they did not feel the need to call anyone while moving through the city streets. Therefore, we can say that a summation of 73% felt unsecured on the streets as in Figure 4.
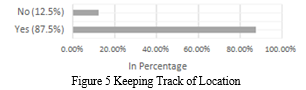
4. Keeping a Track of Location: The participants were asked whether they wanted to share their locations with trusted contacts, as present in Figure 5. 87.5% of them showed interest in sharing their locations. Most of them were young females, followed by young males. The majority of them stated they wanted to share their exact locations while others wanted to share the area of their current locations. Remaining 12.5% were unwilling to share any data regarding their locations because they did not want to share their locations because of privacy issues.
5. Feelings of Emergency Contacts: When participants were asked whether they required emergency contact feature, 70% of them expressed their interest in it. In case of emergency, participants wanted their location to be uploaded and sent to their emergency contacts so that the contacts can get an alert informing that the user is in trouble. The remaining 30% stated that they do not need any emergency contacts. These participants informed them that they do not want to upload their whereabouts or want anyone to see it because they feel that uploading their location would violate their privacy.
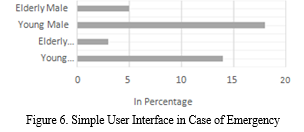
A large number of our participants were youth (18 males and 14 females). Participants stated interest in using an application to send their location to an emergency contact or get in touch with the emergency contact in case of sensing any danger.
Therefore, it was concluded a simple user interface was a priority over a complicated and intimidating interface so that the user can choose the correct option in case of any emergency. Moreover, elderly personnel also showed interest in using this application. Thus, a simple, clean User Interface would also increase the efficiency of the application to the elderly as shown in Figure 6.
V. SYSTEM DESIGN
In Figure 7, we have suggested a system which was acquired from the preferences of the participants. Here we have prioritized on user’s privacy control because nowadays users are much concerned about their privacy. Users can seek help in a way that allows them to preserve privacy without disclosing personal details. Only trusted contacts may know further details.
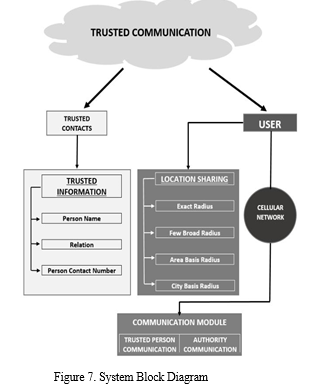
There will be two options, one is for location sharing, and another is for communicating the trusted persons. Here user can share his/her updated location with their trusted contacts, having the flexibility of setting a preferred radius. Besides, the user can also manage the trusted contact list with whom s/he likely to share the location. Additionally, we have kept a calling option to the police control room.
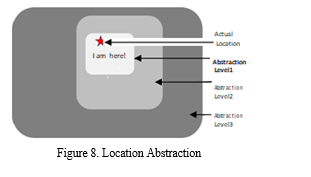
- Location Abstraction: Ability to an abstract location is presented in Figure 8, where the actual location can be abstracted at various levels – defined and preferred by the user seeking for support without compromising the call for help. The abstraction of location is conducted in a randomized manner, as shown in Figure 8.
- Application Description: “I Am Here” was developed on the most used version of android studio 3.0 Canary 1. The application was developed using the API of Android Version 8.0. We did not use the latest android 10.0 version because about according to “Fossbytes”, around 28% of the user around the world still uses android version 8.0 where-else only around 10% of the user uses the later version [49].
After developing the application in the android studio, we ran the application on the android emulator on our personal computer. There were minor bugs that needed attention, and also some UI changes. Then, the android package kit (APK) file was generated and installed to the android device. The application was installed. After installing the necessary permissions, such as access to location, contact and SMS, were granted from the settings option and the application was accessed. Initially, the user is required to register to the application by using either the contact number or the email id.
Figure 9 shows the sign-up/ sign-in window of “I Am Here” where the application automatically suggests the user to sign-up using the account already being used by the phone and also keeps an option of signing with a completely different account.
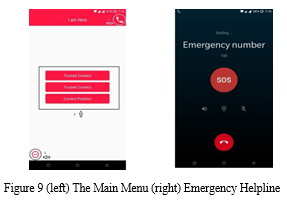
After the user registration, the application takes the user to the homepage. In the homepage, the user will find a few options. There are three marked regions. Region number 1 indicates the option of calling to Emergency Helpline in Bangladesh (999). Region number 2 indicates the main feature of the application, and region number 3 shows the logout option. If the user presses the dial icon from the main menu of the application, the user will see the dial-up section of the phone where the application would automatically place a call at the Emergency Helpline for assistance. Figure 4 shows the dial-up section of the phone calling the emergency helpline. When the user enters the trusted contact section, the user will see the names of the contacts who can see the current location of the user. User can also add other trusted contacts in the list by tapping the plus icon on the top right corner and searching a contact is done using the email id of that contact. “I Am Here” provide the user with the flexibility of deciding how much of the user’s location will be seen by his/her trusted contact. The application provides with four options of user’s location sharing with the trusted contact such as exact radius, few broad radius, area basis radius and city basis radius. Now for each contact user can choose how much of his/her location, the trusted contact and see. Figure 10 shows the location seen by the trusted contact according to the option selected by the user.
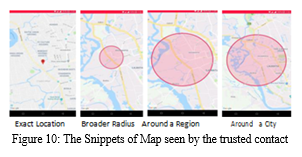
If the user selects the Trustee Contact option, then the user would see the name of the contact who is sharing his/her location with the user. If the user selects the current position option, then the user would be able to see his/her current location.
VI. EVALUATION
Consumption of CPU, Memory, Network and Energy of the test device by “I Am Here” is shown below.
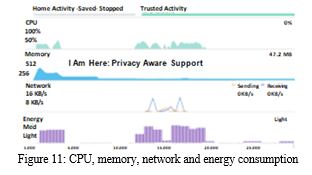
The graph of figure 11 was generated while testing “I Am Here” on Google Nexus 5x. The device runs on a Qualcomm Snapdragon 808 chip which is Hexa-core CPU with 2-gigabyte ram and 2700 mAh battery. The version of android used on the device was Android 8.0 Oreo. The application consumed a low rate of memory and power from the phone. Moreover, under the network section, the receiving bytes per second by the application is higher than that of sending bytes per second. So the user will need fewer data to operate the application than the data needed by the trusted contact. Therefore, location can be shared seamlessly in areas having slow data connectivity.
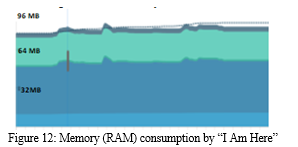
Figure 12 shows how much memory is consumed by the application while operating correctly. A careful observation of the graph informs us that a total of 78.4 MB is used by “I Am Here” where Java processing takes up 11.3 MB, the native application itself occupies 40 MB of the RAM and Stack, code and others need about 1.4 MB, 21.9 MB and 3.8 MB of the memory. The low-end cellular devices of 2018 come packed with a minimum of 1000 MB of memory of which 79 MB is a very negligible portion. Therefore, not only in high-end mobiles but “I Am Here” can run smoothly on low-end mobiles with less RAM.
A. Operating “I AM HERE” on various Devices
In order to check whether “I Am Here” is suitable for all range of devices, the application was tested on three devices. The devices were Samsung Galaxy Note 9, Samsung Galaxy J7 2017 and Samsung J2 2016. Galaxy Note 9 is powered by Qualcomm Snapdragon 845 which an Octa-core chip, being the latest processor on any mobile devices of 2018 and having about 8 GB of ram and runs on latest android version 8.1 Oreo. Galaxy Note 9 is embedded with the latest dual-layered GPS module along with GLONASS, BDS and GALILEO. Galaxy J7 2017 is a mid-range device powered by Cortex-A53 Octa-core chip having 3 GB of ram runs on previous generation android 7.1 Nougat. It has the same GPS of Note 9 but of a single layer. Galaxy J2, on the other hand, is powered by Quad-core Cortex A-7 chip with 1 GB of ram and embedded with a single layer, old generation GPS with the only GLONASS. The phone runs on three-generation old android 5.1.1 Lollipop.
B. User Evaluation: User Evaluation of System
We have presented the methods of user data collection in the Methodology section, showing our application usage study on 107 users. We have conducted a usability study in Dhaka mainly and some outside Dhaka city.
Table 3. Percentage presences on location sharing
|
|
Location Sharing Option |
Interested Participants |
|
|
|
|
|
|
Exact Location |
8% |
|
|
|
|
|
|
Few Broad Location |
67% |
|
|
|
|
|
|
Area Based Location |
22% |
|
|
|
|
|
|
City Based Location |
3% |
|
|
|
|
Most of the users, as can be seen from Table 3, (95%) mentioned positively about the application. However, some were concerned about the accuracy of the given locations (8%). Only 8% of the participants wanted to reveal exact location while 67% preferred a broader radius and the rest wanted it to be obscure (e.g. city-specific information). Current UI seemed complex to some users (17%), and a large number asked to provide similar support in Bengali (43%). We hope to improve our application based on these user inputs.
After testing the application, many participants expressed their benefits and appreciativeness of using it. One of the participants said:
“I am a student, and I am staying in a hostel. When I go home during a semester break, it takes 9 to 10 hours in bus or train journey. Mostly, I travel alone and feel insecure. So, using this app, my family can see my exact location and can sigh breathe of relief.” – (Student, Age 20, Chottogram).
A female student with a part time job told:
“Currently, I am studying at a Private University. Additionally, to support my family, I do a part-time job at a customer call-center of a reputed mobile phone operator of Bangladesh. During the day, I attend lectures, and four days of each week, I work during the night shift at the customer helpline. Because of my duties, sometimes, I fail to receive the parent’s call. Although I use the official transport service to reach home, my parents remain tensed about my safety. With the help of ‘I Am Here’, my parents can quickly check my location even without the need of calling me during work, as well as when I am returning home.” - (Student and a part-time employee, Age 23, Dhaka).
A working mother informed that:
“I stay at work from 9 am to 5 pm every working days. My son will appear for the O-Level exam in the upcoming session. Every day, he attends multiple coaching classes. Each coaching is far from the others. Sometimes he might be at class for which I remain confused whether to call and ask where is he currently attending class for which as a mother, I remain worried. This application helps to drive off that confusion. Now I can keep an eye on where my son is currently attending a class without the need of calling him.” – (Government Officer, Age 38, Dhaka).
Many other teenagers and elderly people have also stated their thoughts about using “I Am Here.”
VII. ACKNOWLEDGMENTS
We want to thank all our participants who participated voluntarily in our survey and testing sessions with full of enthusiasm.
Conclusion
The software has the capability of reducing the abduction issues of Bangladesh that is frequently occurring. Smartphones are becoming cheaper every day, making it more available to the broader population. These significant Smartphone users can have the opportunity to access the service, which might help them tackle many life-threatening situations that they may encounter on the streets of the capital city of Dhaka and the whole of Bangladesh. Our goal is not just reducing abduction but also other tackling crimes such as mugging, rape, and any other kind of harassing issues. If people from all gender and ages learn to use this application properly and share the benefits of it around, then the streets of Bangladesh may become much safer than before.
References
[1] “Population, total”. The World Bank. Retrieved at 20th June 2018. https://data.worldbank.org/indicator/SP.POP.TOTL [2] “The total number of Mobile Phone subscriptions has reached 147.000 million at the end of January, 2018”, Bangladesh Telecommunication Regulatory Commission, Retrieved at 2nd July 2018. http://www.btrc.gov.bd/content/mobile-phone-subscribers-bangladesh-january-2018 [3] “Mobile phone users in Bangladesh top 140 million”, BDNEWS24. Retrieved at 30th June 2018. https://bdnews24.com/business/2017/11/14/mobile-phone-users-in-bangladesh-top-140-million [4] “Crime in Bangladesh”, NUMBEO. Retrieved at 24th June 2018, https://www.numbeo.com/crime/country_result.jsp?country=Bangladesh [5] “Ten people being killed each day in Bangladesh”. The Dhaka Tribune, Retrieved at 21st June 2018. https://www.dhakatribune.com/bangladesh/crime/2016/04/27/ten-people-killed-day-bangladesh [6] Syed Ishtiaque Ahmed, Steven J. Jackson, Nova Ahmed, Hasan Shahid Ferdous, Md. Rashidujjaman Rifat, A.S.M Rizvi, Shamir Ahmed, and Rifat Sabbir Mansur. 2014. Protibadi: A platform for fighting sexual harassment in urban Bangladesh. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems (CHI \'14). ACM, New York, NY, USA, 2695-2704. DOI: https://doi.org/10.1145/2556288.2557376 [7] Toby Xu and Ying Cai. 2007. Location anonymity in continuous location-based services. In Proceedings of the 15th annual ACM international symposium on Advances in geographic information systems (GIS \'07). ACM, New York, NY, USA, Article 39, 8 pages. DOI: https://doi.org/10.1145/1341012.1341062 [8] A.J. Bernheim Brush, John Krumm, and James Scott. 2010. Exploring end user preferences for location obfuscation, location-based services, and the value of location. In Proceedings of the 12th ACM international conference on Ubiquitous computing (UbiComp \'10). ACM, New York, NY, USA, 95-104. DOI: https://doi.org/10.1145/1864349.1864381 [9] Duckham, M. and Kulik, L. Location privacy and location-aware computing, In Dynamic & Mobile GIS:Investigating Change in Space and Time, CRC Press, 2006, 34-51. [10] Steiert, Douglas, et al. \"Poster: A Location-Privacy Approach for Continuous Queries.\" Proceedings of the 22nd ACM on Symposium on Access Control Models and Technologies. ACM, 2017. [11] de Montjoye, Yves-Alexandre; César A. Hidalgo; Michel Verleysen; Vincent D. Blondel (March 25, 2013). \"Unique in the Crowd: The privacy bounds of human mobility\". Scientific Reports. doi:10.1038/srep01376. Retrieved 12 April 2013. [12] Palmer, Jason (March 25, 2013). \"Mobile location data \'present anonymity risk\'\". BBC News. Retrieved 12 April 2013. [13] Tara Matthews, Kerwell Liao, Anna Turner, Marianne Berkovich, Robert Reeder, and Sunny Consolvo. 2016. She’ll just grab any device that’s closer: A Study of Everyday Device & Account Sharing in Households. In Proceedings ofthe 2016 CHI Conference on Human Factors in ComputingSystems, 5921– 5932. [14] Sambasivan, N., Checkley, G., Batool, A., Ahmed, N., Nemer, D., Gaytán-Lugo, L., Matthews, T., Consolvo, S., and Churchill, E. 2018. “Privacy is not for me, it\'s for those rich women”: Performative Privacy Practices on Mobile Phones by Women in South Asia [15] GSMA Country Overview: Bangladesh Report, Available online at https://www.gsma.com/mobilefordevelopment/wp-content/uploads/2016/02/Country_Overview_Bangladesh_.pdf (accessed on 25th November, 2018) [16] “Harassmap “Available online at http://harassmap.org/en/, (accessed on 25th November, 2018) [17] “Onwatch,” Available online at http://www.onwatchoncampus.com/ (accessed on 25th November, 2018) [18] ” Bangladesh witnesses 592 rapes in six months,” 2018, Available online at https://www.dhakatribune.com/bangladesh/crime/2018/07/17/bangladesh-witnesses-592-rapes-in-six-months (accessed on 5th September 2018 [19] “5yr old girl ‘raped’ in Faridpur,” 2018, Available online at https://www.thedailystar.net/country/5yr-old-girl-raped-faridpur-1565281 (accessed on 5th September 2018) [20] “Horrific tale of kidnap,” 2018, Available online at https://www.thedailystar.net/backpage/horrific-tale-kidnap-1548397 (accessed on 5th September 2018) [21] “2 years of Tonu murder: Protesters demand justice,” 2018, Available online at https://www.thedailystar.net/country/2-years-tonu-murder-protesters-demand-justice-1550929 (accessed on 5th September 2018) [22] “Ekram killing: Audio clip raises questions about anti-drug crackdown,” 2018, Available online at https://www.dhakatribune.com/bangladesh/nation/2018/06/02/ekram-killing-audio-clip-raises-questions-about-anti-drug-crackdown (accessed on 5th September 2018) [23] “Ward councillor Ekramul killed in Cox’s Bazar ‘gunfight’,” 2018, Available online at http://www.newagebd.net/article/42201/ward-councillor-ekramul-killed-in-coxs-bazar-gunfight (accessed on 5th September 2018) [24] “Crime Statistics 2010,” 2010, Available online at https://www.police.gov.bd/en/crime_statistic/year/2010 (accessed on 10th September 2018) [25] “Crime Statistics 2011,” 2011, Available online at https://www.police.gov.bd/en/crime_statistic/year/2011 (accessed on 10th September 2018) [26] “Crime Statistics 2012,” 2012, Available online at https://www.police.gov.bd/en/crime_statistic/year/2012 (accessed on 10th September 2018) [27] “Crime Statistics 2014,” 2014, Available online at https://www.police.gov.bd/en/crime_statistic/year/2014 (accessed on 10th September 2018) [28] “Crime Statistics 2016,” 2016, Available online at https://www.police.gov.bd/en/crime_statistic/year/2016 (accessed on 10th September 2018) [29] “Crime Statistics 2018,” 2018, Available online at https://www.police.gov.bd/en/crime_statistic/year/2018 (accessed on 10th September 2018) [30] Hollaback! Available online at http://www.ihollaback.org/ (accessed on 25th November, 2018) [31] Not your baby app, Available online at http://www.gender-focus.com/2013/05/18/new-apps-tackle-dating-violence-street-harassment/ (accessed on 25th November, 2018) [32] METRAC, Available online at https://www.metrac.org/?doing_wp_cron=1538322458.2737810611724853515 625 (accessed on 25th November, 2018) [33] Onwatch, Available online at http://www.onwatchoncampus.com/ (accessed on 25th November, 2018) [34] S. I. Ahmed, S. J. Jackson, N. Ahmed, H. S. Ferdous, M. R. Rifat, A. S. M. Rizvi, S. Ahmed, and R. S. Mansur. Protibadi: a platform for fighting sexual harassment in urban bangladesh. In CHI, pages 2695{2704, 2014. [35] Hello CT, Available online at https://dmp.gov.bd/police-apps-hello-ct/ (accessed on 25th November, 2018) [36] M. M. Hossain, M. Sharmin and S. Ahmed. Bangladesh emergency services: a mobile application to provide 911-like service in Bangladesh. [37] M. E. Ali, S. B. Rishta, L. Ansari, T. Hashem, and A. I. Khan. SafeStreet: empowering women against street harassment using a privacy-aware location-based application. [38] Harassmap Available online at http://harassmap.org/en/ (accessed on 25th November, 2018) [39] Circleof6, Available online at http://www.circleof6app.com/, (accessed on 25th November, 2018) [40] bSafe Available online at https://getbsafe.com/, (accessed on 25th November, 2018) [41] M. Y. Sarosh, M. A. Yousaf, M. M. Javed and S. Shahid. MehfoozAurat: transforming smart phones into women safety devices against harassment. [42] S. A. Akash, M. A. Zihad, T. Adhikary, M. A. Razzaque and A. Sharmin. HearMe: a smart mobile application for mitigating women harassmen [43] M. Kumar and R. Kumar. IPROB – emergency application for women [44] ”Citiesnot safe for women,” 2017, Available online at https://www.thedailystar.net/backpage/cities-not-safe-women-1498840, (accessed on 25th November, 2018) [45] “Khashoggi murder: Calls to remove Saudi crown prince \'a red line\',” 2018, Available online at https://www.bbc.com/news/world-middle-east-46295142, (accessed on 25th November, 2018) [46] Sambasivan, Nithya, et al. \"\" Privacy is not for me, it\'s for those rich women\": Performative Privacy Practices on Mobile Phones by Women in South Asia.\" Fourteenth Symposium on Usable Privacy and Security ({SOUPS} 2018). 2018. [47] Biernacki, Patrick, and Dan Waldorf. \"Snowball sampling: Problems and techniques of chain referral sampling.\" Sociological methods & research 10.2 (1981): 141-163. [48] ”Bangladeshi Students Bring Dhaka to a Standstill With Protests Over Road Safety,” 2018, Available online at http://time.com/5357019/bangladesh-student-protests-road-safety/ (accessed on 25th November, 2018 [49] “Most Popular Android Versions In May 2019 (Always Updated List),” 2019, Available online at https://fossbytes.com/most-popular-android-versions-always-updated/ (accessed on 13th June 2020)
Copyright
Copyright © 2022 Mohammad Kaosain Akbar, Dibya Prokash Sarkar, Emrul Kaiser. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET46776
Publish Date : 2022-09-15
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

