Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Impacts in Social Networks
Authors: Sumitra ., Amaresh
DOI Link: https://doi.org/10.22214/ijraset.2022.42307
Certificate: View Certificate
Abstract
In this paper, we present a methodology both informal community construction and strength of impact between people advance continually, it expects to follow the powerful hubs under a unique setting. To resolve this issue, we investigate the Influential Node Tracking (INT) issue as an expansion to the conventional Influence Maximization issue (IM) under powerful interpersonal organizations. While Influence Maximization issue targets distinguishing a bunch of k hubs to boost the joint impact under one static organization, INT issue centers around following a bunch of persuasive hubs that continues to expand the impact as the organization advances. Using the perfection of the advancement of the organization structure, we propose a productive calculation, Upper Bound Interchange Greedy (UBI) and a variation, UBI+. Rather than developing the seed set from the beginning, begin from the compelling seed set we find beforehand and execute hub substitution to further develop the impact inclusion. Moreover, by utilizing a quick update technique by working out the minor addition of hubs, our calculation can scale to dynamic interpersonal organizations with a huge number of hubs. Exact examinations on three genuine huge scope dynamic informal communities show that our UBI and its variations, UBI+ accomplishes better execution with regards to both impact inclusion and running time.
Introduction
I. INTRODUCTION
Web-based entertainment impact is an advertising term that portrays a singular's capacity to influence others' reasoning in a social web-based local area. The more impact an individual has, the more allure that individual needs to organizations or others who need to advance a thought or sell an item.
Organizations can saddle online entertainment impact to assist with creating brand mindfulness, sell stock and increment client commitment. This should be possible by executing an advertising procedure that spotlights on expanding the organization's own online entertainment impact or by recruiting laid out, dependable powerhouses in the space.
A. What are Social Media Influencers?
A virtual entertainment force to be reckoned with is a client that has laid out believability in a specific industry or content sort that approaches a wide crowd. A powerhouse ought to have a sufficiently huge following and the ability to have the option to ignite a discussion and motivate an activity or change in conduct. Organizations can employ web-based entertainment powerhouses to assist with extending their social reach, become more interesting and support items or administrations.
B. Types Of Social Media Influencers Include
- Celebrity Influencers: These are the most notable powerhouses as they have obtained their following from their superstar status. Since specific VIPs draw in unambiguous socioeconomics and interest groups, organizations that wish to arrive at those customers can enlist the VIP force to be reckoned with to advance or underwrite their item to their fans.
- Consumer Influencers: These are regular individuals that have acquired a following because of their character and appeal. They are normally dynamic on their online entertainment through text posting, contributing to a blog or photograph sharing. Since their crowd thinks about them "genuine" or "engaging" they will more often than not view their recommendation in a serious way, for example, when they vouch for an assistance.
- Micro Influencers: Otherwise called master powerhouses, these are regular individuals that have acquired a following and effective authority because of their insight in a particular region. At the point when they suggest or commend an item, their crowd is probably going to trust their viewpoint.
- Content Creators: These incorporate proficient bloggers, vloggers and photographic artists. Their job incorporates growing new satisfied that perusers are keen on staying aware of consistently. Part of an organization's advertising technique could be to send items to a substance maker in the expectations they will survey and talk emphatically about it to their supporters. Another choice is to compose supported posts for their foundation.
Prior to picking a powerhouse, organizations ought to think about a couple of characteristics. The first is assuming the powerhouse's very own message adjusts well will the organization and is pertinent to a similar interest group. The second is the means by which drawing in the powerhouse is with their following, or how dependable their following thinks about them. Finally is to consider the force to be reckoned with's compass or supporter consider this can assist with anticipating profit from speculation (ROI).
C. Impact Of Social Media
- Social media only continues to grow as a form of communication and entertainment, meaning social platforms get more powerful as their memberships rise. Due to this, social media impacts society in the following ways:
- Generating visibility around social, ethical, environmental and political views or issues.
- Spreading educational material quickly and efficiently.
- Providing companies with new marketing opportunities.
- Creating new channels that companies can use to find, recruit and hire new employees.
- Increasing the number of social contacts of groups and individuals.
- Producing new jobs associated with social media networks and consulting.
- Allowing a platform for group discussion and opinion sharing.
II. Related Work
The work in 1] presents an outline of studies in regards to Adaptive Seeding (AS) philosophies to settle the Influence Maximization (IM) issue. IM is the method involved with finding and actuating a bunch of seed persuasive hubs clients to start the dissemination interaction so the biggest number of hubs is reached or impacted. Frequently, that arrangement of clients is limited to the people who are locked in with the subject of interest, and because of primary conditions of the organization, positioning low as far as their impact potential is conceivable. An elective methodology is to consider a versatile technique which targets cultivating adjoining hubs of high impact. As both IM and AS procedures remember the initiation of hubs which for turn proliferate the got data and enact others, the work portrayed in [1] covers just the "Data Flow and Influence: Propagation-arranged" class as depicted in our study.
The creators in [2] have checked on approaches that empower Information Retrieval (IR) errands in OSNs, which exploit content and primary social data. The exploration works the creators have checked on have been characterized into three classifications as indicated by the utilization of social data. In particular, the "social web search" classification incorporates strategies where social substance is utilized to further develop exemplary IR cycles like re-positioning of recovered records, question reformulation, extension or decrease, and client profiling. The subsequent classification, called "social hunt", remembers philosophies for data revelation in view of clients' produced content, associations, and connections. At last, "social suggestion" targets foreseeing clients' inclinations and depends on satisfied based and cooperative separating approaches.
Thus, the review in [2] covers the parts of "Social Matching: User-situated", "Organization/Graph Properties", and "Applications: Recommendation", as portrayed by this work. At long last, the creators of [3] give an outline on different client arrangement procedures in OSNs. All the more explicitly, they depict the most well-known systems in view of machine (for example Bayesian, Decision Tree, Logistics, SVM and KNN) and non-machine (idea of entropy and in light of client comparability) learning strategies. The point of these strategies is to order clients into specific classes 9 as indicated by their express or verifiable elements, like conduct credits, profile data, interests, viral substance and intelligence. Accordingly it covers just the "Social Matching: User-situated" classification as we have introduced in this study.
The creators in [4] propose an augmentation of PageRank for estimating impact. They applied their lengthy PageRank approach on a diagram of retweets and client connections and consider social variety of clients and transmission probabilities of the messages in view of the speculation that clients acquire impact from their supporters. The point is to investigate whether individual qualities and social activities as well as impact spread designs are factors equipped for affecting different clients.
III. Existing System
The cycles and elements by which data and ways of behaving spread through informal organizations have long intrigued researchers inside numerous areas. Seeing such cycles can possibly reveal insight into the human social construction, and to affect the methodologies used to advance ways of behaving or items. While the interest in the subject is well established, late expanded accessibility of interpersonal organization and data dispersion information (through locales like Facebook, Twitter, and LinkedIn) has raised the possibility of applying interpersonal organization examination at an enormous scope to beneficial outcome.
One specific application that has been getting revenue in endeavors is to involve informal exchange impacts as an apparatus for viral advertising. Persuaded by the promoting objective, numerical formalizations of impact boost have been proposed and broadly concentrated by numerous scientists. Impact expansion is the issue of choosing a little arrangement of seed hubs in an informal organization, with the end goal that their general effect on different hubs in the organization, characterized by specific models of dispersion, is boosted.
IV. Proposed System
For genuine powerful informal community, it is probably not going to have unexpected and intense changes in chart structure in a brief timeframe. Thus, the comparability in design of diagrams from two continuous previews could prompt comparative seed sets that augment the impact under each chart. In view of the above thought, we propose UBI calculation for the INT issue, in which we observe the seed set that boosts the impact under Gt+1 in light of the seed set St we have previously found for diagram Gt. Rather than building the seed set for diagram Gt+1 from the beginning, begin with St and ceaselessly update by supplanting the hubs in St to further develop the impact inclusion. Our calculation first purposes an underlying set and a few rounds of exchange heuristic to augment the impact, as referenced in the paper. So the exchange heuristic clearly chips away at a preview diagram. When reached out to the powerful chart, our calculation just has to exchange for a couple of additional rounds after each time window and can accomplish a quicker update. More definite depictions about how our technique deals with the preview charts and dynamic organizations will be introduced in the following two subsections.
V. Implementation
A. Modules Description
The Modules are:
- Impact Maximization Module: Marketing effort is generally not a one-time bargain, rather ventures complete a supporting effort to advance their items by cultivating persuasive hubs persistently. Frequently, an advertising effort might keep going for months or years, where the organization intermittently distributes financial plans to the chose compelling clients to use the force of the informal exchange impact. Under this present circumstance, it is normal and critical to understand that social or data networks are consistently elements, and their geography advances continually over the long haul. For instance, joins show up and vanish when clients follow/unfollow others in Twitter or companion/unfriend others in Facebook. Besides, the strength of impact likewise continues to change, as you are more affected by your companions who you contact often, while the impact from a companion typically subsides as time slips by in the event that you don't contact with one another. Subsequently, a bunch of hubs persuasive at one at once to unfortunate impact inclusion after the development of informal community, which proposes that involving one static set as seeds across time could prompt unacceptable execution.
- Persuasive Node Tracking Module: The customary Influence Maximization issue targets tracking down powerful hubs for only one static informal community. Be that as it may, true informal communities are only occasionally static. Both the design and furthermore the impact strength related with the edges change continually. Subsequently, the seed set that boosts the impact inclusion ought to be continually refreshed by the advancement of the organization structure and the impact strength. In this work, we model the powerful interpersonal organization as a progression of depiction charts, G1,. . . , GT . We expect that the hubs continue as before while the edges in every depiction chart change across various time stretches. Every preview chart is demonstrated as a coordinated organization, Gt = (V;Et), which incorporates edges showing up during the periods viable. Also, a bunch of proliferation probabilities Pt u;v is related with every depiction diagram Gt. We want to follow a progression of seed sets, meant as St; t = 1; : : : ; T, that amplifies the impact work t() at every one of the depiction Gt.
- Upper limits Examination Module: Upper bound named as dynamic hubs' way rejected upper bound (AB), is hypothetically more tight than the upper bound proposed , which we call it the guileless upper bound (NB). To approve our hypothesis, we run observational trials to contrast our bound AB and the credulous upper bound. We first concentrate a progression of preview charts from Mobile datasets by setting both time window and time contrast to 60 minutes. We run comparable number of emphasess in figuring both AB and NB on a similar hub set with size k = 30 where proliferation probabilities are set by DWA model. The seed set is chosen by Greedy calculation that expands the impact under every depiction. As is displayed in Figure 9, our bound is reliably more tight than the credulous bound proposed in as recommended by our hypothesis. It ought to be seen that the horrible showing of NB under DWA model is because of the way that occasionally NB neglects to join in Mobile organization.
- Upper Bound of Node Replacement Gain Module: In this segment, we delineate the just baffling part in our UBI calculation, in particular the calculation of the upper bound of the substitution gain u;vs (S). Zhou et al. first take advantage of the upper bound on leverage capacity to speed up the avaricious calculation in persuasive seeds determination . we propose a more tight upper bound on the substitution gain by barring the impact along ways, which incorporate approaching edges to the seed set. We have told beforehand the best way to process a more tight bound on the trade gain for one static organization with a decent seed set S. Nonetheless, as organization changes continually, we really want to refresh the upper bound by the progressions in spread likelihood. In addition, as we incorporate new hub into the seed set S, we likewise need to refresh the upper bound as the engendering likelihood lattice PG(S+T) additionally changes.
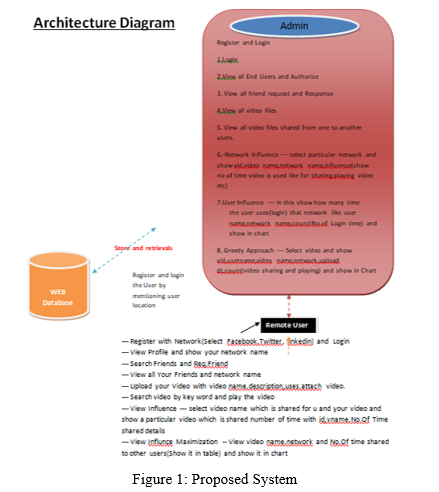
VI. Architecture Diagram
A covetous calculation, as the name proposes, consistently pursues the decision that is by all accounts the best at that point. This implies that it settles on a locally-ideal decision with the expectation that this decision will prompt an internationally ideal arrangement
Accept that you have a goal work that should be upgraded (either expanded or limited) at a given point. A Greedy calculation goes with covetous decisions at each progression to guarantee that the goal work is upgraded. The Greedy calculation has just a single shot to figure the ideal arrangement so it never returns and turns around the choice.
Greedy algorithms have some advantages and disadvantages:
- It is quite easy to come up with a greedy algorithm (or even multiple greedy algorithms) for a problem.
- Analyzing the run time for greedy algorithms will generally be much easier than for other techniques (like Divide and conquer). For the Divide and conquer technique, it is not clear whether the technique is fast or slow. This is because at each level of recursion the size of gets smaller and the number of sub-problems increases.
- The difficult part is that for greedy algorithms you have to work much harder to understand correctness issues. Even with the correct algorithm, it is hard to prove why it is correct. Proving that a greedy algorithm is correct is more of an art than a science. It involves a lot of creativity.
VII. Future Enhancement
It very well might be souring for the online entertainment skeptics to process that purposes and benefits of web-based entertainment offset the inconvenience. Since online entertainment is associated, correspondence is exceptionally successful. Individuals can show portfolio to checkout a task on the organization. The blaze news can keep one to be update on society. Social adjusting can be spurred. With fast reach to people anyplace on the planet, virtual entertainment assumes an incredible part for the outcome of every person. As an immediate future work, we might want to sum up our UBI calculation to follow powerful hubs under the other generally embraced dissemination model, Linear Threshold model under unique organizations. Also, it will be fascinating in the event that we can consolidate our work with . That is to follow a progression of compelling hubs where the dispersion interaction is additionally done under a unique organization rather than the static depiction diagram.
Conclusion
We investigate a clever issue, specifically Influential Node Tracking issue, as an augmentation of Influence Maximization issue to dynamic organizations, which targets following a bunch of compelling hubs progressively to such an extent that the impact spread is amplified all of a sudden. We propose a proficient calculation UBI to tackle the INT issue based thought of the Interchange Greedy method.We use the upper bound on hub substitution gain to speed up the cycle. Also, a proficient technique for refreshing the upper bound is proposed to deal with the development of the organization structure. Broad investigations on three genuine interpersonal organizations show that our technique beats cutting edge baselines concerning both impact inclusion and running time. Then, at that point, we propose UBI+ calculation that works on the calculation of the upper bound and accomplishes better impact spread.
References
[1] Y. Singer, “Influence maximization through adaptive seeding”, ACM SIGecom Exchanges, Volume 15, Issue 1, 2016, pp. 32-59, http://dx.doi.org/10.1145/2994501.2994503 [2] M. R. Bouadjenek, H. Hacid, M. Bouzeghoub, “Social networks and information retrieval, how are they converging? A survey, a taxonomy and an analysis of social information retrieval approaches and platforms”, Information Systems, Volume 56, 2016, pp. 1-18, http://dx.doi.org/10.1016/j.is.2015.07.008 [3] G. Bai, L. Liu, B. Sun, J. Fang, “A survey of user classification in social networks”, in: 6th IEEE International Conference on Software Engineering 60 and Service Science (ICSESS), Beijing, 2015, pp. 1038-1041, http://dx.doi.org/10.1109/ICSESS.2015.7339230W [4] . Chen, Y. Wang, and S. Yang, “Efficient influence maximization in social network,” in KDD, 2009, pp. 199–208. [5] P.-Y. Huang, H.-Y Liu, C.-T. Lin, P.-J. Cheng, “A diversity-dependent measure for discovering influencers in social networks”. in: R. E. Banchs, F. Silvestri, T.-Y. Liu, M. Zhang, S. Gao, & J. Lang (Eds.), Information retrieval technology - 9th Asia information retrieval societies conference, AIRS 2013, Singapore, December 9-11, 2013, in: Lecture Notes in Computer Science, Volume 8281, Springer, pp. 368-379 [6] P. Domingos and M. Richardson, “Mining the network value of customers,” in KDD, 2001, pp. 57–66. [7] D. Kempe, J. Kleinberg, and E. Tardos, “Maximizing the spread of inffluence through a social network,” in KDD, 2003, pp. 137–146. [8] M. Kimura and K. Saito, “Tractable models for information diffusion in social networks,” in PKDD, 2006, pp. 259–271. [9] W.Yu, G.Cong, G.Song, and K.Xie, “Community-based greedy algorithm for mining top-k influential nodes in mobile social networks,” in KDD, 2010, pp. 1039–1048. [10] W.Chen, C.Wang, and Y.Wang, “Scalable influence maximization for prevalent viral marketing in large-scale social networks,” in KDD, 2010, pp. 1029–1038. [11] W. Chen,W. Lu, and N. Zhang, “Time-critical influence maximization in social networks with time-delayed diffusion process,” in AAAI, 2012. [12] W. Chen, Y. Yuan, and L. Zhang, “Scalable influence maximization in social networks under the linear threshold model,” in Data Mining (ICDM), 2010 IEEE 10th International Conference on. IEEE, 2010, pp. 88–97. [13] N. Du, L. Song, M. Gomez-Rodriguez, and H. Zha, “Scalable influence estimation in continuous-time diffusion networks,” in Advances in neural information processing systems, 2013, pp. 3147– 3155. [14] J. Leskovec, J. Kleinberg, and C. Faloutsos, “Graphs over time: densification laws, shrinking diameters and possible explanations,” in KDD, 2005, pp. 177–187. [15] J. Leskovec, J. M. Kleinberg, and C. Faloutsos, “Graph evolution: Densification and shrinking diameters,” TKDD, vol. 1, 2007. [16] J. Leskovec, L. Backstrom, R. Kumar, and A. Tomkins, “Microscopic evolution of social networks,” in KDD, 2008, pp. 462–470. [17] C. Zhou, P. Zhang, J. Guo, X. Zhu, and L. Guo, “Ublf: An upper bound based approach to discover influential nodes in social networks,” in ICDM, 2013. [18] M. Richardson and P. Domingos, “Mining knowledge-sharing sites for viral marketing,” in KDD, 2002, pp. 61–70. [19] J. Leskovec, A. Krause, C. Guestrin, C. Faloutsos, J. VanBriesen, and N. S. Glance, “Cost-effective outbreak detection in networks.” in KDD, 2007, pp. 420–429. [20] Q. Jiang, G. Song, G. Cong, Y. Wang, W. Si, and K. Xie, “Simulated annealing based influence maximization in social network,” in AAAI, 2011. [21] K. Jung, W. Heo, and W. Chen, “Irie: Scalable and robust influence maximization in social networks,” in ICDM, 2012, pp. 918–923. [22] M. G. Rodriguez and B. Sch¨olkopf, “Influence maximization in continuous time diffusion networks,” arXiv preprint arXiv:1205.1682, 2012. [23] Y. Tang, X. Xiao, and Y. Shi, “Influence maximization: Nearoptimal time complexity meets practical efficiency,” in Proceedings of the 2014 ACM SIGMOD international conference on Management of data. ACM, 2014, pp. 75–86. [24] Y. Tang, Y. Shi, and X. Xiao, “Influence maximization in nearlinear time: a martingale approach,” in Proceedings of the 2015 ACM SIGMOD International Conference on Management of Data. ACM, 2015, pp. 1539–1554.
Copyright
Copyright © 2022 Sumitra ., Amaresh . This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET42307
Publish Date : 2022-05-06
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

