Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Pursuance Scrutiny of Packet Detection Procedure Applied to Network Monitoring
Authors: Dr. Ayesha Taranum, Deepana N R, Deekshitha P, Kavyashree K S
DOI Link: https://doi.org/10.22214/ijraset.2022.44610
Certificate: View Certificate
Abstract
Network security might be a convoluted subject, generally just made a plunge thoroughly prepared and persevered through specialists. In any case, as endlessly further individuals come wired\'\', an adding number of distinctions got to figure out the basics of safety during an arranged world. Network security refers to the projects and procedures in place to prevent unapproved access, misuse, modification, or forswearing of an infinitely network-accessible money vault. The approval of access to the information within an organization is governed by the organization’s leader. Some set of experiences of systems administration is incorporated, additionally as an introduction to TCP/IP and internetworking. We keep on assuming about danger activity, network entanglements, firewalls, and more unique reasons for secure systems administration predisposition. Network security begins with confirming, by and large with a username and a word. Since these needs just a single detail confirming the stoner the name — that is, the word — is usually labelled as one-factor confirmation. With two-factor verification, where the Stoneham’s also used (e.g., a security memorial or dongle,\' an ATM card, or a cell phone); and with three-factorr verification, item the stoners also used (e.g., a security memorial or dongle an ATM card, or a cell phone) (e.g., a point or retinal exam).
Introduction
I. INTRODUCTION
Network security can be a perplexing topic that is best handled by professionals who are well-prepared and experienced. However, as a growing number of people become "wired," a growing number of people are need to learn the fundamentals of safety in a structured world. The procedures and practices used to halt and screen unapproved access, abuse, adjustment, or forswearing of an infinite network available assets are referred to as network security. The organization director controls network security, which includes the approval of information access. This message spread process is ordinarily referenced in light of the fact that the "store-convey and forward" system, and accordingly the directing is set in an "entrepreneurial" style.
II. LITERATURE SURVEY
- This work provides Trait grounded encryption (ABE) on middleware for access control, based on current approaches for access control on middleware. ABE combines access control and perplexity for the good of all information. Network middleware is a new layer between network predisposition and pall operations that reduces pall estimation and data management. In this research, we suggest the CPABE conspiracy on the middleware sub position in the NETWORK framework armature for stoner access control The proposed layout should provide security and sufficiency while reducing middleware complexity. To support the proposed plot, we used the AVISPA device.
- This paper is being executed utilizing a PIR sensor and is spoken with relevant/natural mindfulness, which will allow it to take a superior choice regarding when to tell the proprietor and henceforth lessening the phony problem rate. The outcome proposed during this paper plans to check back this advance notice rate. The projected result has an impact on people's desire to carry their phones with them everywhere they go. Consciousness with a sense of place of the Because of the ESP8266's several modes of operation, a framework is possible. The system also looks for the owner's phone's MAC address to determine his or her presence. It also decides whether or not to recommend a good measure of any mixture to the proprietor. During a SQL database, the instance of interruption will also be logged.
- This paper carries out a hypothetic-logical system, the allowances and speculations are introduced for the conventional evidence of the newly proposed technique. The outcomes accomplished inside the examination show that the methodology of the confirmation component is streamlined, and the model was approved inside the In a Fog Computing context, the AVISPA convention assessment instrument was used in a constrained memory-controlled climate
- This paper is carried out utilizing the OS-TCP application layer to channel traffic and make it secure. Instructions for remotely monitoring and obtaining framework traffic over the web by providing a genuine lightweight security plot on the transmission control convention (TCP) network. What's more, fabricated programming between the remote checking framework and NETWORK gadget to improve and uphold the TCP application layer to channel traffic and make it secure. Operating system TCP is light weighted and least handshaking security conspire with altered incorporated key administration. Operating system TCP plans to put the least weight over obliged NETWORK gadgets and deal sensible security to data. The further extent of work incorporates planning and modifying the plan for monstrous NETWORK sending.
- This work presents a consensus model for meetings in an Internet of Things (IoT) environment, which is used in the context of fog computing. At least one layer from the network device can be attacked. accompanying: 1) Hardware layer, 2) Network layer, and 3) Cloud layer. An adversary gains access to the organization's equipment and recovers the keys or security barriers that have been stored inside the device unique ID number is assigned to each organization’s device. The calculation is safe from side-channel attacks that try to break into the organization's devices' security. After each successful meeting between the server and the business gadget, the password arrangement is modified.
- This work employs an approach for (1) obtaining End-To- End devices that protect the NETWORK administration door and low-power sensor hubs using lightweight asymmetric cryptography, and (2) obtaining Broker devices/Gateways and hence cloud administrations using Lattice-based cryptography. The devices used by the organization are diverse, ranging from distant sensors to less resource-intensive devices. This protects the system from DDoS attacks, eavesdropping, and quantum computation attacks. The suggested convention makes use of the sensors' unique Device IDs to generate key pairs for determining shared device-to-device confirmation Services. Finally, inside the channel, the Mutual confirmation instrument is used.
- This study focuses on a lightweight mutual authentication mechanism between network devices that is important for access control and security policymaking, and it describes the results of the proposed method's functional tests. Many businesses have recently introduced smart networks and wearable devices.
- The IETF Core working group is considering lightweight DTLS for the network environment to adopt security protocols used in conventional IP networks. The experiment will use Wi-Fi, BLE, and ZigBee communication to combine access control policies between devices (e.g., Gas Leak Detectors and Gas Breakers) when providing smart home services. Furthermore, we will carefully examine the suggested mutual authentication method's security flaws and, if necessary, supplement the features to increase the method's safety.
- This study uses a security scheme that is based on the most widely used public-key cryptography (RSA) and runs on top of conventional low-power communication stacks. They discuss their findings in this paper. In light of existing Internet principles, particularly the Datagram Transport Layer Security (DTLS) convention, the principal fully executed two-way validation security conspire for the Internet of Things (NETWORK). Existing executions, designing methods, and security frameworks can be reused if they are based on a laid-out standard, allowing for easy security implementation. They've completed framework engineering for the planned plot based on a low-power equipment stage that's appropriate for the business.
- This study employs a security scheme that is based on the most widely used public-key cryptography (RSA) and runs on top of common low-power communication stacks. Existing executions, designing methodologies, and security foundations can all be reused if they are based on a laid-out standard, allowing for easy security adoption. They created a structure for the proposed plot based on the organization's low-power equipment stage. With the origination of forestalment, we've identified dark opening attacks inside businesses using two different methods: (1) interruption disclosure framework (IDS) and (2) encryption design (computerized hand). In addition, standard AODV, BH AODV, and DBH AODV conventions are investigated for brilliant quality of administration (QoS) bounds, such as parcel conveyance rate (PDR), confinement, and more, with varying the number of knocks, bundle sizes, and recreation times.
- This paper presents a study on wormhole attacks and their countermeasures in Mobile Unplanned Networks (MANET) with their unborn compass. The paper is arranged as follows: It gives an overview of wormhole attacks in ad hoc networks. presents a review on some being wormhole discovery and forestalment schemes. Section IV shows the longer-term compass of wormhole discovery and forestalment schemes bandied before. In an impromptu organization, autonomous knock’s structure a multi-jump radio organization for speaking with one another and keeping up with availability in a decentralized way. Each bunch works as both a number and a switch. In other words, unplanned network is rested on dynamic topology, because the bumps are mobile and keep changing connectivity among bumps with time.
12. In this study, we proposed a modified AODV convention capable of imitating geography with a district social a bad bunch that drops all bundles passing through it. This adjusted AODV convention is given a build-up dark opening AODV The primary motivation behind an area assault is to and by the answer to any RREQs without empowering the word parcel to a cunning objective; Dark opening assault that builds the succession number utilizing concession tie inside the organization, loftiest arrangement number is 4294967295 which is 32-cycle unsigned whole number worth of AODV convention.
13. In this paper, we examine the most common security entanglements and attacks, as well as the solutions offered within the test to address these security flaws. MANETs are made up of mobile knocks that communicate with one another via remote connections. Comparable organizations are habitually utilized in the milestone activity, calamity activity, and in far-off regions where the foundation and activity of a fixed network are beyond the realm of possibilities. They’re portrayed by questionable correspondence media where the organization's geographies change forcefully. Additionally, each bunch is restricted by data transfer capacity, battery, and estimation power.
14. This study will provide a quick overview of the various types of area assaults carried out during the AODV steering convention. A Distant Mobile Ad-hoc Network (MANET) is a tone- configurable and structureless network made up several of flexible knocks connected by a remote media. It's a bunch of tone-supporting versatile knocks which will send through radio grows. Anytime, a bundle is to be energized by a bunch, it will initially check with its directing table to pick whether a course to the objective is currently conceivable. If a course isn't open or the ahead of the time entered course is inactivated, likewise the bunch begins a course revelation course. The steering dispatches won't portray the entire way it will illuminate just specific sources and objectives.
III. COMPARISION
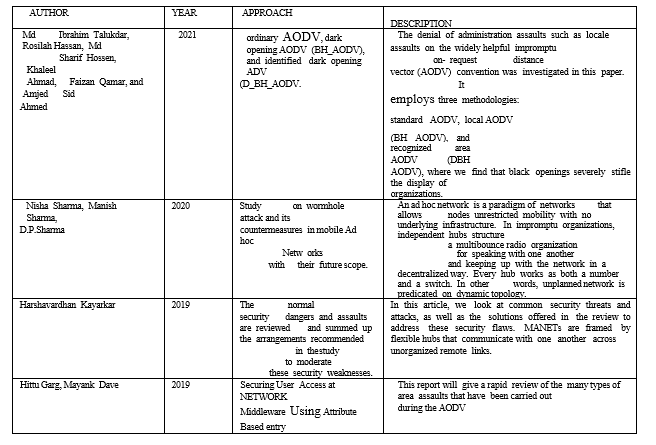
In this we Use the AODV Routing protocol which helps in identifying the path of communication, in this, it has the source device, destination device, and neighbour’s device form which packets can send. In AODV, nodes discover routes in request- response cycles.
A node requests a route to a destination by broadcasting an RREQ message to all its neighbours. When a node receives an RREQ message but does not have a route to the requested destination, it, in turn, broadcasts the RREQ message. Also, it remembers a reverse route to the requesting node which can be used to forward subsequent responses to this RREQ. This process repeats until the RREQ reaches a node that has a valid route to the destination. This node (which can be the destination itself) responds with an RREP message. This RREP is unicast along the reverse routes of the intermediate nodes until it reaches the original requesting node.
Thus, at the end of this request-response cycle, a bidirectional route is established between the requesting node and the destination. When a node loses connectivity to its next hop, the node invalidates its route by sending a RERR to all nodes that potentially received its RREP.
Conclusion
In this project, we used Aodv as routing protocol, we use the packet sniffing method for live packets data sent from device to device with the help of IP Address and Port Number of Nodes. Then identify the attackers in the network during packet transmission is major proposed work in this project.
References
[1] Hittu Garg, Mayank, Department of Computer Engineering National Institute of Technology Kurukshetra, Haryana, India, “Securing User Access at NETWORK Middleware Using Attribute Based Access Control”, 10th ICCCNT 2019 July 6-8, 2019, IIT - Kanpur, Kanpur, India. [2] Ravi Kishore Kodali, Sasweth C. Rajanarayanan, AnveshKoganti and Lakshmi Boppana Department of Electronics and Communication Engineering National Institute of Technology, Warangal, Telangana, India,“Network based security system”, [3] Leandro Loffi, Carla Merkle Westphall, Lukas DernerGr¨udtner, Carlos Becker Westphall Postgraduate Program in Computer Science Federal University of Santa Catarina P.O. Box 476, 88040-970, Florian´opolis, SC, Brazil,“Mutual Authentication for NETWORK in the Context of Fog Computing”, 2019 11th international conference on communication system & network (COMSNETS). [4] Rohan A Nath S N Systems PVT. Ltd, Pune India, “Objective Secured TCP Socket for remote monitoring NETWORK devices”, 10th ICCCNT 2019 July 6-8, 2019, IIT- Kanpur, India. [5] Trusit Shah Department of Computer Science University of Texas at Dallas Richardson, S. Venkatesan Department of Computer Science University of Texas at Dallas Richardson, “Authentication of Network Device and Network Server Using Secure Vaults”, 2324-9013/18/31.00©2018 IEEE DOI 10.1109/TrustCom / BigDataSE.2018.00 117. [6] S. Sridhar Research Scholar, Dept. of IT, Alpha College of Engineering, Chennai, India, Dr. S. Smys Dept of ECE, RVS Technical Campus, Coimbatore, India, “Intelligent Security Framework for Network Devices Cryptography Based End -To- End Security Architecture”, 978-1-5090-4715-4/17/$31.00 ©2017IEEE. [7] Jin-Hee Han Information Security Research Division ETRIDaejeon, Republic of Korea, JeongNyeo Kim Information Security Research Division ETRIDaejeon, Republic of Korea, “A Lightweight Authentication Mechanism between Network Devices”, 978-1-5090-4032- 2/17/$31.00 ©2017 IEEE. [8] Shadi Janba baei Department of Computer Engineering Shahed University, Tehran, Iran, Hossein Gharaee Iran Telecom. Research Center Tehran, Iran, Naser Mohammad zadeh Department of Computer EngineeringShahed University, Tehran, “Lightweight, Anonymous and Mutual Authenticationin NETWORK Infrastructure”, 978-1-5090-3435-2/16/$31.00 ©2016 IEEE. [9] Thomas Kothmayr, Corinna Schmitt, Wen Hu, Michael Brunig and Georg Carle, “A DTLS Based EndToEnd Security Architecture for the Internet of Things with Two-Way Authentication”, 2016, IEEE Conference. [10] Md Ibrahim Talukdar , Rosilah Hassan , Md Sharif Hossen , Khaleel Ahmad , Faizan Qamar , and Amjed Sid Ahmed Department of Information and Communication Technology (ICT), Comilla University, Cumilla, Bangladesh 2 Centre for Cyber Security, Faculty of Information Science and Technology, Universiti Kebangsaan Malaysia (UKM), 43600 UKM Bangi, Selangor, Malaysia 3 Department of Computer Science and Information Technology, Maulana Azad National Urdu University, Hyderabad, India 4 Computing Department, Engineering Faculty, Global College of Engineering and Technology, Oman, “Performance Improvements of AODV by Black Hole Attack Detection Using IDS and Digital Signature”, Received 24 November 2020; Revised 3 January 2021; Accepted 13 February 2021; Published 2 March 2021.
Copyright
Copyright © 2022 Dr. Ayesha Taranum, Deepana N R, Deekshitha P, Kavyashree K S. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET44610
Publish Date : 2022-06-20
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

