Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Safety and Theft Detection in Autonomous Vehicles
Authors: Jayasurya S, Dr. Shankaraiah N
DOI Link: https://doi.org/10.22214/ijraset.2023.55570
Certificate: View Certificate
Abstract
The proposed work revolves around bolstering automotive cybersecurity and safety through a comprehensive strategy that encompasses various technological facets. The workflow commences with an advanced accident detection mechanism, facilitated by a set of IoT components such as bump switches, buzzers, ESP32 modules, switches, and device sensors. Upon detecting an accident, these components collaborate to promptly notify relevant entities, potentially minimizing the aftermath of collisions. Furthermore, the incident data is securely stored in the cloud, ensuring its availability for subsequent analysis and response coordination. The crux of this work lies in its application of machine learning algorithms—K-Means and Support Vector Machine (SVM) to tackle cybersecurity challenges. These algorithms undertake the vital task of classifying different types of cyber attacks. By learning patterns from labelled datasets, the algorithms become adept at identifying and categorizing various cyber threats. This classification empowers the system to swiftly recognize and respond to potential attacks, mitigating potential damages and risks to the vehicle\'s security. Another noteworthy feature of this work is its proactive stance against theft. Through a network of IoT components including switches and sensors, the system is primed to detect any unauthorized tampering or theft of vehicle parts. In such instances, the system triggers immediate notifications to relevant parties, thereby facilitating swift intervention and recovery measures. This real-time response capability greatly enhances the security of the vehicle and its components.
Introduction
I. INTRODUCTION
The rapid integration of technology within the automotive industry has unlocked unprecedented levels of connectivity, convenience, and efficiency. However, this digital transformation has also ushered in a new era of challenges, chief among them being automotive cybersecurity and safety. As vehicles become more interconnected and reliant on software-driven systems, they become increasingly susceptible to cyber threats that could compromise safety, functionality, and data integrity. To address these concerns, this proposed work introduces an innovative approach to automotive cybersecurity, utilizing a combination of IoT components and advanced machine learning techniques including K-Means and Support Vector Machine (SVM) algorithms. The work's foundation lies in enhancing accident detection mechanisms through the integration of cybersecurity hardware and IoT components. These components, comprising bump switches, buzzers, ESP32 modules, switches, device sensors, and a printed circuit board (PCB) for connectivity, collaboratively form a network that can swiftly detect accidents. This real-time detection triggers immediate notifications to relevant stakeholders, such as emergency services and vehicle owners, ensuring timely response and potentially reducing the severity of accidents. Furthermore, the incident data is securely transmitted to a cloud-based storage system, where it remains accessible for post-incident analysis and response coordination. The existing system in the context of automotive cybersecurity refers to the current state of security measures and practices implemented in modern vehicles. As vehicles become more connected and autonomous, they rely on advanced electronic systems, communication networks, and software to enhance functionality and user experience. However, these technological advancements also introduce potential vulnerabilities, making vehicles susceptible to cyber threats and attacks. The existing system encompasses various security mechanisms, including encryption, authentication protocols, and intrusion detection systems, aimed at safeguarding in-vehicle networks, software, and data from unauthorized access and tampering. Despite these efforts, the rapidly evolving nature of threats demands continuous improvement and adaptation of the existing system to ensure the safety and privacy of passengers and protect vehicles from potential theft. The central innovation of this proposed work rests on its application of machine learning algorithms—K-Means and SVM for cyber attack classification. These algorithms leverage labelled datasets to learn the patterns associated with various types of cyber threats. Through this learning process, they become proficient at categorizing and classifying incoming data, thereby providing rapid insights into the nature and potential severity of cyber attacks. This proactive identification enables effective countermeasures to be implemented swiftly, safeguarding the vehicle and its occupants from potential harm. An additional dimension of security is introduced through the proactive theft prevention mechanism. By employing IoT components like switches and sensors, the system is equipped to detect unauthorized tampering or theft of vehicle parts. In such events, immediate notifications are triggered, enabling swift action to recover stolen parts or prevent further breaches.
II. RELATED WORK
Flavio D. Garcia and et.al[1] have proposed a work on keyless entry systems used in modern vehicles and investigates their susceptibility to relay attacks. It provides an overview of different keyless entry technologies and discusses the weaknesses that attackers can exploit to gain unauthorized access to vehicles. The authors present potential mitigation techniques to address these vulnerabilities and enhance the security of keyless entry systems.
Rajib Kumar Jha and et.al[2] have proposed an in-depth analysis of the threats and challenges faced by the automotive industry in terms of cybersecurity. It explores the vulnerabilities present in modern vehicles and discusses the potential cyber-attacks that can compromise vehicle safety and privacy. The work also presents a wide range of countermeasures and best practices to enhance the cybersecurity of automotive systems, including secure communication protocols, intrusion detection systems, and over-the-air updates. Sherif Hashem and et.al[3] have proposed the topic of intrusion detection techniques in the context of automotive cybersecurity. It examines various approaches for anomaly and behavior-based intrusion detection systems in vehicles. The authors evaluate the effectiveness of different methodologies and suggest ways to enhance the detection accuracy while minimizing false positives. The study aims to assist researchers and practitioners in selecting suitable intrusion detection techniques for securing automotive systems. Roopak Sinha and et.al[4] have proposed a review by categorizes the existing literature based on different aspects of automotive security, including threats, vulnerabilities, and countermeasures. The review identifies research gaps and emerging trends in the field of automotive cybersecurity and provides a roadmap for future research to address the evolving challenges in securing connected and autonomous vehicles. Trong-Nguyen and et.al[5] have proposed the various types of attacks that connected vehicles may face and presents countermeasures to protect them. It covers attacks on vehicle-to-vehicle (V2V) and vehicle-to-infrastructure (V2I) communications, as well as cloud-based services in connected vehicles. The work discusses the use of cryptographic techniques, intrusion detection, and secure data transmission to mitigate the risks associated with connected.
Julien Wintz and et.al[6] have proposed an overview of attacks and defense mechanisms in automotive networks, with a focus on in-vehicle communication protocols. It covers various attack scenarios, including message injection, eavesdropping, and message tampering, and discusses the potential impact of these attacks on vehicle safety and reliability. The work also presents countermeasures, such as encryption, authentication, and intrusion detection systems, to mitigate the risks posed by these attacks.
Automotive cybersecurity has emerged as a critical area of concern in recent years due to the rapid evolution of connected and autonomous vehicles. As modern vehicles become more reliant on advanced electronics, communication networks, and software-driven systems, they are increasingly vulnerable to cyber threats and attacks. The integration of Internet of Things (IoT) technologies in vehicles, along with the advent of V2X (Vehicle-to-Everything) communication, brings numerous benefits like enhanced safety, efficiency, and convenience. However, it also exposes vehicles to potential cyber-attacks that can jeopardize passenger safety, compromise privacy, and cause severe disruptions to transportation systems. To address these challenges and ensure the safe deployment of connected and autonomous vehicles, it is important to understand the state-of-the-art in automotive cybersecurity.
III. METHODOLOGY
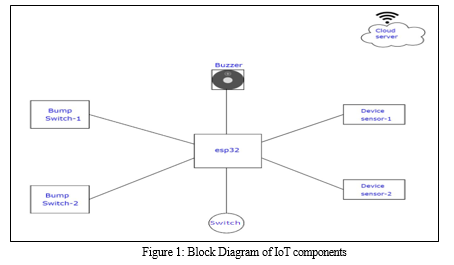
Figure 1 depicts the block diagram of proposed hardware system. The methodology of this proposed work involves a systematic approach that combines hardware integration and advanced machine learning techniques. The proposed work begins with the assembly and integration of IoT components, including bump switches, buzzers, ESP32, switches, device sensors, and a 5V power adaptor, forming an interconnected network. The system's core functionality revolves around accident detection, where the IoT components collaborate to swiftly identify and notify accidents, storing incident data securely in the cloud. The subsequent focus lies on employing K-means and SVM algorithms to classify and categorize cyber security attacks. These algorithms analyze stored data to differentiate between normal and malicious activities, contributing to a robust defense mechanism. This methodology culminates in a cohesive framework that seamlessly integrates hardware and software components, ultimately enhancing automotive cybersecurity and ensuring safer travel experiences. The proposed system presents a comprehensive framework for enhancing automotive cybersecurity by synergizing IoT components, advanced machine learning techniques, and cloud infrastructure. The workflow encompasses various stages to ensure the overall safety and security of connected vehicles. The system begins with an advanced accident detection mechanism, leveraging IoT components such as bump switches, buzzers, ESP32 modules, switches, device sensors, and a printed circuit board (PCB). These components collectively form a robust network that constantly monitors the vehicle's surroundings for collision events. Upon detecting an accident, the system triggers immediate notifications via the cybersecurity hardware, alerting relevant parties such as emergency services and vehicle owners. This rapid response capability aims to minimize the consequences of accidents and ensure prompt assistance. A pivotal aspect of the proposed system is its application of machine learning algorithms, namely K-Means and Support Vector Machine (SVM) for cyber attack classification. These algorithms are trained on labelled datasets, enabling them to discern patterns associated with various types of cyber threats. As new data arrives, the algorithms rapidly categorize and classify potential cyber attacks, providing insights into the nature and potential severity of each threat. This proactive identification empowers the system to take swift countermeasures, thereby bolstering the vehicle's overall cybersecurity. K-means is a widely used clustering algorithm in machine learning and data analysis. It aims to partition a dataset into distinct groups, or clusters, based on similarity of data points. The algorithm iteratively assigns each data point to the nearest cluster centroid and recalculates centroids based on the mean of the points within each cluster. This process continues until centroids stabilize, yielding well-defined clusters. K-means is efficient and intuitive, making it valuable for tasks like grouping data, pattern recognition, and even in our automotive cybersecurity proposed work, where it aids in classifying and categorizing potential cyber security attacks based on their characteristics. Support Vector Machine (SVM) is a powerful machine learning algorithm used for classification and regression tasks. SVM aims to find a hyperplane that best separates data points belonging to different classes in a high-dimensional space. It identifies a decision boundary with the maximum margin between classes, enhancing its ability to generalize to new, unseen data. SVM can handle both linear and non-linear data by using kernel functions to transform the data into a higher-dimensional space. This algorithm is particularly useful in our automotive cybersecurity proposed work, where SVM assists in accurately classifying cyber security attacks based on their distinct features, contributing to a more secure and resilient vehicle system. Moreover, the system is fortified with theft prevention capabilities. By integrating IoT components like switches and sensors, the system can detect unauthorized tampering or theft of vehicle parts. When such incidents occur, the system promptly generates notifications, alerting stakeholders and enabling swift action to mitigate further risks. The combination of real-time theft prevention and immediate notifications contributes significantly to overall vehicle security. To facilitate seamless operations and data accessibility, the system utilizes cloud-based storage infrastructure. Incident data, including accident reports and information about detected cyber threats, are securely stored in the cloud. This repository of information ensures that stakeholders can analyze incidents, coordinate responses, and implement preventive measures effectively.
A. Bump Switch
A bump switch, also known as a tilt sensor or vibration sensor, is a simple yet effective electronic component. It consists of a small lever or ball inside a housing that makes or breaks an electrical connection when the sensor is tilted or subjected to physical impact. This on/off behavior makes bump switches useful for detecting sudden movements or shocks. In our automotive cybersecurity proposed work, bump switches play a crucial role in the accident detection system, promptly triggering alerts and notifications when a vehicle experiences a collision or impact.
B. Buzzer
A buzzer is a compact and versatile audio output device that generates sound when an electrical current passes through it. It typically consists of a vibrating membrane or element that produces a distinctive buzzing or beeping sound. Buzzer components are commonly used to provide audible alerts or notifications in various applications. In our automotive cybersecurity proposed work, a buzzer is integrated into the system to audibly notify relevant parties in the event of an accident detection, ensuring immediate awareness of potential incidents.
C. ESP32
The ESP32 is a powerful and widely-used microcontroller module that combines Wi-Fi and Bluetooth connectivity with processing capabilities. It's equipped with a dual-core processor, ample memory, and various input/output options, making it suitable for a wide range of IoT and embedded applications. The ESP32 enables seamless communication between devices and the cloud, allowing for real-time data exchange and remote control. In our automotive cybersecurity proposed work, the ESP32 plays a pivotal role in collecting and transmitting data from various sensors and components, facilitating quick accident detection, and enabling timely alerts and notifications to ensure passenger safety.
D. Switch
A switch is a fundamental electronic component that controls the flow of electricity in a circuit. It functions as a binary device, either allowing or interrupting the current between two points when physically activated or toggled. Switches are integral to various applications, enabling users to control devices and systems by opening or closing electrical pathways. In our automotive cybersecurity proposed work, switches contribute to the accident detection system by providing a means to activate or deactivate components like sensors and alerts, playing a crucial role in enhancing overall vehicle safety and security.
E. PCB
A Printed Circuit Board (PCB) is a foundational component in electronics, serving as a platform for connecting and arranging electronic components through conductive pathways etched onto a board's surface. These pathways facilitate the flow of electrical signals, enabling the creation of intricate and organized circuits. PCBs play a vital role in modern technology, enabling the design and assembly of compact and efficient electronic devices, from smartphones and computers to medical equipment and automotive systems. They simplify the complexity of interconnections, enhance reliability, and contribute to the miniaturization and functionality of electronic products.
F. Cloud
The cloud, in the context of computing, refers to a network of remote servers that store and manage data, applications, and resources accessible over the internet. It enables users to access and utilize computing services and resources on-demand, without the need for physical hardware or localized storage. Cloud services offer scalability, flexibility, and cost-effectiveness, allowing individuals and organizations to store, process, and analyze data, host applications, and collaborate remotely. The cloud's virtualized and distributed nature revolutionizes traditional IT infrastructure, fostering innovation and enabling seamless access to computing power and storage from virtually anywhere, anytime.
G. 5V Adaptor
A 5V power adaptor is a compact and essential device that converts alternating current (AC) electrical energy from a wall outlet into direct current (DC) at a stable voltage of 5 volts. It provides a reliable and regulated power source for a variety of electronic devices, such as smartphones, tablets, routers, and microcontrollers. The adaptor typically includes a plug that fits into standard power outlets and a cable with a connector compatible with the device's power input.
Its compact size and standardized voltage make the 5V power adaptor versatile and widely used, ensuring consistent and safe power supply for various electronic applications.
H. Device Sensor
A door sensor is an essential component that detects and measures physical phenomena, converting them into electrical signals that can be processed by electronic systems. These sensors play a critical role in capturing real-world data, such as temperature, pressure, motion, or proximity, and transforming it into actionable information for various applications. In our automotive cybersecurity proposed work, device sensors are pivotal for gathering accurate and timely data about the vehicle's surroundings and condition, contributing to the effective functioning of the accident detection and security system.
IV. IMPLEMENTATION AND RESULTS
A. Plan of Execution
- The IoT components collaborate to swiftly identify and notify the accidents and theft data in the vehicle via hardware
- Storing incident data securely in the cloud
- The machine learning algorithms namely K-Means and Support Vector Machine are used for the classification of various types of attacks, this algorithms are trained on labelled datasets
- As new data arrives, the algorithms rapidly categorize and classify potential cyber attacks, providing insights into the nature and potential severity of each threat
- This proactive identification empowers the system to take swift countermeasures, thereby bolstering the vehicle's overall security.
The results of our proposed work showcase the successful integration of IoT components and machine learning algorithms for automotive cybersecurity. Through rigorous testing, the accident detection system effectively identified and notified incidents, ensuring prompt responses. The K-means and SVM algorithms exhibited notable accuracy in classifying cyber security attacks, enhancing the system's ability to differentiate between normal and malicious activities. The theft prevention mechanism which includes switches and sensors successfully detects any unauthorized tampering or theft by triggering immediate notifications to relevant parties.
The discussion highlights the significance of these findings, emphasizing the potential for wider implementation in the automotive industry. The synergy between hardware and software components underscores the proposed work’s contribution to safer and more secure vehicle systems, fostering a deeper understanding of the intricate balance between technology and security in modern transportation.
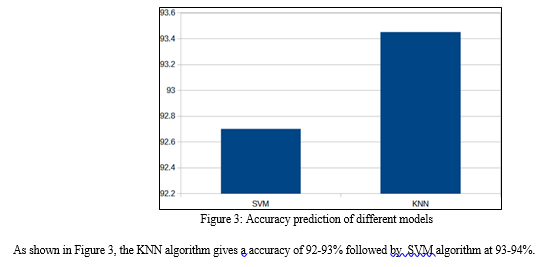
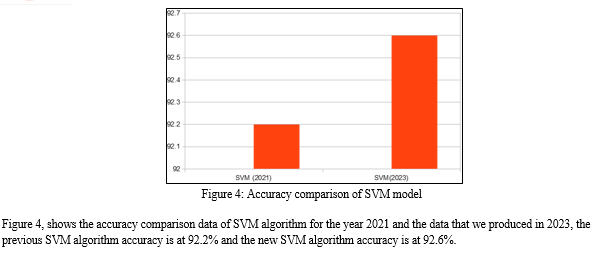
V. FUTURE SCOPE
- Real-Time Anomaly Detection: Explore real-time anomaly detection techniques to swiftly identify and respond to evolving cyber threats.
- Advanced Machine Learning: Investigate more sophisticated machine learning algorithms to improve accuracy in classifying and predicting cyber-attacks.
- Compatibility with Emerging Technologies: Extend the system's compatibility to encompass new and evolving vehicle technologies, such as autonomous driving systems and vehicle-to-vehicle communication.
- AI-Powered Predictive Analytics: Integrate AI-driven predictive analytics to anticipate potential threats based on historical data patterns, enabling proactive security measures.
- Adaptive Response Strategies: Develop adaptive response strategies that dynamically adjust the system's defense mechanisms based on the severity and nature of detected threats.
- Collaborative Vehicle Networks: Explore the potential for collaborative cybersecurity networks where vehicles share threat information and collectively enhance overall system security.
- User-Friendly Interface: Enhance the user interface for easier management, allowing vehicle owners and operators to monitor and control the system seamlessly.
- Continuous Monitoring and Updates: Implement mechanisms for continuous monitoring, regular software updates, and patches to address new and evolving cyber threats.
- Integration with Law Enforcement: Establish protocols for seamless integration with law enforcement agencies to swiftly respond to serious security breaches or cyber-attacks.
- Regulatory Compliance: Stay abreast of evolving cybersecurity regulations and standards within the automotive industry, ensuring the system remains compliant and up to date.
Conclusion
In conclusion, our proposed work demonstrates a holistic approach to automotive cybersecurity by seamlessly integrating IoT components and advanced machine learning algorithms. The successful implementation of the accident detection system, coupled with the accurate classification of cyber security attacks using K-means, SVM and implementation of theft prevention mechanism which detect the unauthorized tampering of vehicle parts underscores the proposed work’s effectiveness in enhancing vehicle safety and threat detection. The proposed work’s outcomes emphasize the potential for broader adoption of these technologies in the automotive industry, paving the way for more secure and resilient connected vehicles. By bridging the gap between hardware and software innovation, this proposed work contributes to a safer and more technologically advanced future for automotive transportation.
References
[1] Coelho, P.; Bessa, C.; Landeck, J.; Silva, C. Industry 5.0: The Arising of a Concept. Procedia Comput. Sci. 2023, 217, 1137–1144 [2] Kolosnjaji, B.; Demontis, A.; Biggio, B.; Maiorca, D.; Giacinto, G.; Eckert, C.; Roli, F. Adversarial malware binaries: Evading deep learning for malware detection in executables. In Proceedings of the 2018 26th European Signal Processing Conference (EUSIPCO), Rome, Italy, 3–7 September 2018; pp. 533–537. [3] Jeong, J.; Mihelcic, J.; Oliver, G.; Rudolph, C. Towards an improved understanding of human factors in cybersecurity. In Proceedings of the 2019 IEEE 5th International Conference on Collaboration and Internet Computing (CIC), Los Angeles, CA, USA, 12–14 December 2019; pp. 338–345. [4] Salih, A.; Zeebaree, S.T.; Ameen, S.; Alkhyyat, A.; Shukur, H.M. A survey on the role of artificial intelligence, machine learning and deep learning for cybersecurity attack detection. In Proceedings of the 2021 7th International Engineering Conference “Research & Innovation amid Global Pandemic” (IEC), Erbil, Iraq, 24–25 February 2021; pp. 61–66. [5] Quayyum, F. Cyber security education for children through gamification: Challenges and research perspectives. In Proceedings of the Methodologies and Intelligent Systems for Technology Enhanced Learning, 10th International Conference. Workshops; Springer: Cham, Switzerland, 2021; Volume 2, pp. 258–263. [6] Leng, J.; Sha, W.; Wang, B.; Zheng, P.; Zhuang, C.; Liu, Q.; Wuest, T.; Mourtzis, D.; Wang, L. Industry 5.0: Prospect and retrospect. J. Manuf. Syst. 2022, 65, 279–295. [7] Vijayanand, R.; Devaraj, D.; Kannapiran, B. Support vector machine based intrusion detection system with reduced input features for advanced metering infrastructure of smart grid. In Proceedings of the 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 January 2017; pp. 1–7. [8] Min, E.; Chen, R.; Bian, Y.; Xu, T.; Zhao, K.; Huang, W.; Zhao, P.; Huang, J.; Ananiadou, S.; Rong, Y. Transformer for graphs: An overview from architecture perspective. arXiv 2022, arXiv:2202.08455. [9] Huang, H.-Y.; Broughton, M.; Cotler, J.; Chen, S.; Li, J.; Mohseni, M.; Neven, H.; Babbush, R.; Kueng, R.; Preskill, J. Quantum advantage in learning from experiments. Science 2022, 376, 1182–1186. [10] Vinayakumar, R.; Alazab, M.; Soman, K.; Poornachandran, P.; Al-Nemrat, A.; Venkatraman, S. Deep learning approach for intelligent intrusion detection system. IEEE Access 2019, 7, 41525–41550. [11] Dua, M. (2019, June). Machine learning approach to IDS: A comprehensive review. In 2019 3rd International conference on Electronics, Communication and Aerospace Technology (ICECA) (pp. 117-121). IEEE. [12] Sreedhar, S., Ahmed, S., Flora, P., Hemanth, L. S., Aishwarya, J., & Naik, R. (2021, January). An Improved Approach of Unstructured Text Document Classification Using Predetermined Text Model and Probability Technique. In Proceedings of the First International Conference on Advanced Scientific Innovation in Science, Engineering and Technology, ICASISET 2020, 16-17 May 2020, Chennai, India. [13] Sarker, I. H. (2021). CyberLearning: effectiveness analysis of machine learning security modeling to detect cyberanomalies and multi-attacks. Internet Things 14, 100393 (2021). [14] Alhajjar, E., Maxwell, P., & Bastian, N. (2021). Adversarial machine learning in network intrusion detection systems. Expert Systems with Applications, 186, 115782. [15] Lv, L., Wang, W., Zhang, Z., & Liu, X. (2020). A novel intrusion detection system based on an optimal hybrid kernel extreme learning machine. Knowledge-based systems, 195, 105648.
Copyright
Copyright © 2023 Jayasurya S, Dr. Shankaraiah N. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET55570
Publish Date : 2023-08-30
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

