Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
The Impact of Data Breach on Reputed Companies
Authors: Rakesh Kumar Ray, Rahul Kumar Sinha, Tinganiwar Akhilesh Kumar
DOI Link: https://doi.org/10.22214/ijraset.2022.45819
Certificate: View Certificate
Abstract
We\'ll come to digital India we the Indians are at the top position in internet usage at the same time India is ranked third among list of countries globally where most of the threats were detected &second globally when it comes to spam and phishing (misleading emails, weblink etc. A data breach is the planned or inadvertent disclosure of confidential information to unauthorized parties. The impact of cyber-attack on a Company is much higherthan the impact on an individual.Data leakage poses serious threats to companies, including significant reputational damage and financial losses. Day by day as the volume of data is growing exponentially and data breaches are happening more frequently than ever before, identifying and preventing data loss has become one of the most pressing security concerns for organizations. This review article helps to learn about company’s data leak threats, recent data breach incidents and its impact on reputed companies.
Introduction
I. INTRODUCTION
We are in 21st Century where we can find everything Online. We the human beings are adopting the technology in all possible ways to make our lives Comfortable. Even the companies conduct their businesses electronically and trying harder to make us comfortable by making themselves online, but some where there will be always a question mark regarding the security of data, we share with those companies it might be personal orprofessional data.Information security incidents are increasing continuously. Information leakage is a serious threat to firm operations, such as institution and government agencies.
The loss of sensitive data can lead to significant reputational damage and financial losses, and even can destroyed long-term stability of a company.
In the digital modern era, data has achieved one of the most crucial components of an organization. A data breach is the intentionally or unintended exposure of confidential information to unauthorized hands.
It poses serious threats to enterprises, including significant reputational and financial losses.What if the companies are vulnerability to data breach? A rise of cybercrime in industries has overburdened the organizations with high costs and impacted their revenue to a large scale [1].
Data breach report 2019 of IBM exposed that within 16 geographies, 507 organizations and 17 industries have suffered an average cost of 3.92 million (USD) with an average data breach size of records 25,575. Yahoo reportedin2016, that minimum 500 million accounts had been stolen in a manifest ‘state sponsored’ data breach in 2014 [2].
Whenever a data breach incident happens, various financial problems can beat the organization and infected organization’s security.
Researches have proved that 29% of businesses end up losing revenue after facing the incident of data breach out of that 38% enterprises experience a loss of almost 20% of more and are unable to sustain the condition.
Organizational Data
- Finance Companies: Income statements, balance sheets, loan details, bank Account details
- Online Shopping Sites: personal information like Name, Address, mobile number, bank card details,
- Insurance Companies: medical records, bank records
- Job Offering Sites: educational Records
II. CLASSIFICATION OF DATA LEAK THREATS
Data leak threats can be classify on the basis (1) of their causes that could be either intentionally or inadvertently (2) on which parties caused the leakage that could be either insider or outsider threats. Mostly intentional leaks caused due to either external hands or malicious insiders. External information breaches are normally performed by hacker break-ins, virus, malware, and social engineering (e.g., phishing) as shown in Figure 1.
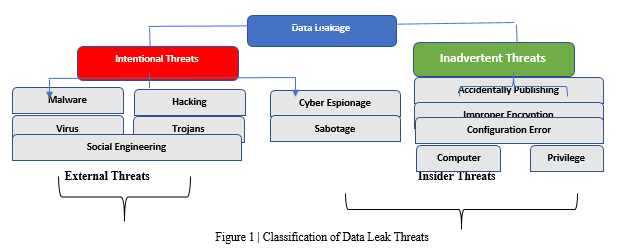
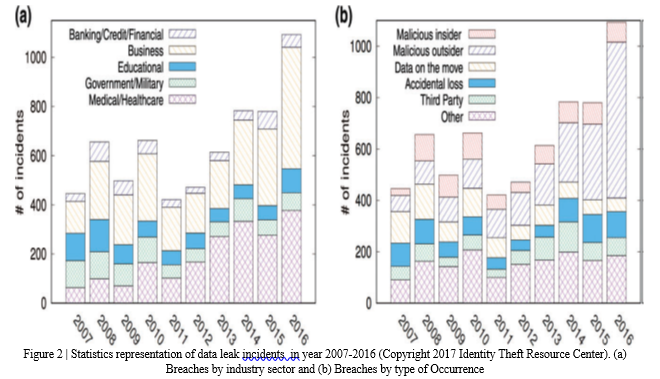
There are also some other attributes like industry sector or the types of occurrences to characterized data leaks. The Report of Identity Theft Resource Center (figure 2), showed that number of major data breach cases keep increasing from 2011 to 2016. Data breach incidents in 2016 is around 40% more than the incidents in 2015. Similarly, incidents of data breach are increasing as 10%, 30%, 32% in the year 2012,2013,2014 respectively. Business and medical/healthcare sectorleaks take the majority portion of the data leaks. Data breach by type of occurrence is shown in Figure 2(b), that is on the basis of malicious insider, malicious outsider, data on the move, accidental loss, third party and others, where the ‘Other’ category involve email/internet exposure or any employee error. In 2016, figure represents, the number of data breaches due to malicious outsider is around 55% of the overall leak incidents [4].
III. DATA BREACH AND IMPACT
A successful Cyber Attack can cause major damage to the companies.
A. Reputation Damage
Apart from immediate costs, a cyberattack can also have less obvious long-term consequences related to reputation damagethat took years to build. If the website is down for longer periods of time the company may appear unreliable and possibly lose credibility. The crucially loss of trust the company must focus less on growing & more on repairing its reputation.
The effect of reputational damage can even impact on your suppliers, or affect relationships you may have with partners, investors and other third parties investor in your business [6].
B. Financial Losses
The monetary cost of a Breach is much higher than just replacing any lost are stolen devices investing in existing security and strengthening the buildings physical security. The most obvious consequence of many attacks, is the main target, for example, unauthorized or fraudulent transfers, or ransom payments after a ransomware infection.
Expenses on investigation, post-breach forensics and vulnerability analysis and interpretation may require to engage in costly external auditors and consultants. For some organizations, if their servers are down for some time means they lost business if there is an online store goes offline, customers can’t place orders or buy products.
C. Legal Liability
The company may be responsible for connecting all the affected customers about breach and have to be prepared for litigation even employees may live the company
Data protection and privacy laws require to manage the security of all Data which holds with company. If this data is accidentally or deliberately compromised, and the company is failed to deploy appropriate security measures, then the company must face fine and regulatory sanctions.
Apart fromfines and regulatory obligations, enterprises can face civil lawsuits from the business partners and customers who has been affected from data breach. If any organization’s information systems are breached and customer personal data is stolen, it may be forced to prove that the incident was not due to negligence and company did everything reasonably possible to maintain its best-practice security measures and procedures.
Table I | Tremendous organizations Data Leak Incidents in past Years (Data Source Is from the Dataset of World’s Biggest Data Breaches3)
|
Organization |
Industry |
Records |
Type |
Source |
Estimated Cost |
Breach Date |
|
Adobe System |
Business |
152 Million |
Financial access |
Malicious outsider |
$714 Million |
September 2013 |
|
Target |
Business |
110 Million |
Financial access |
Malicious outsider |
$252 Million |
November 2013 |
|
Korea Credit bureau |
Financial |
104 Million |
Identify theft |
Malicious insider |
$100 Million |
January 2014 |
|
Benesse |
Education |
49 Million |
Identify theft |
Malicious insider |
$138 Million |
July 2014 |
|
JMPorgan chase |
Financial |
83 Million |
Identify theft |
Malicious outsider |
$13 Million |
August 2014 |
|
Home depot |
Business |
109 Million |
Financial access |
Malicious outsider |
$28 Million |
September 2014 |
|
Yahoo |
Business |
500 Million |
Account access |
State Sponsored |
$350 Million |
December 2014 |
|
Anthem insurance |
Healthcare |
78 Million |
Identify theft |
Malicious outsider |
$100 Million |
January 2015 |
IV. CASE STUDY
A. BigBasket Data Breach
BigBasket, India’s top online grocerhas suffered a massivedata breach, allegedly sold of personal information of more than 20 million customers on dark web. Cyber has claimed that personal information of as many as 20 million users such as full names, email IDs, password hashes (potentially hashed OTPs), pin, contact numbers (mobile and phone),date of birth, full addresses, location, and IP addresses of where users have logged in from and have been put up for sale for $40,000on the dark web[7].
B. Upstox Data Breach
Upstox, second largest stock broker of the country in the terms of strength of customers have been breached by hackers and theft KYC and other data of about 25 lakhs of customers. Ravi Kumar, Upstox’s co-founder and CEO, through its website exposed security systems has been upgraded after receiving of emails, claimed unauthorized access into company’s database. “These claims proposed thatthird-party data-warehouse systemsmay have been compromised some contact information and KYC data [8].
C. MobiKwik Data Breach
The data of around 110 million users of MobiKwik, mobile wallet and payments app is reported to be on sale on a hacker forum on the dark web. The dataset is nearly 8.2TB in size and includes details of Aadhaar cards, KYC documents, mobile phone numbers linked to MobiKwik wallet, credit card details, etc [9].

D. Domino's Data Breach
India’s one of the top pizza service Domino’s was affected with massive data breach that exposed order details of 18 crore Pizza orders made via the service includes 130TB of employee data files and customer details. The data leak includes the details of some transactions which reveals the order delivery address, the date, the name, phone number & email ID of the customer latitude and longitude coordinates of the address, total number of transactions and the total amount spent on orders transactions in Rupees.

Conclusion
With cybercriminals increasing day to day as they are shifting their interest from stealing money to stealing data, no company can honestly say that their system is 100% safe from vulnerabilities in its systems. Anyone can be targeted by unauthorized exploits and other bulk attack attempts, so the best way to protect your company is to avoid being an easy target. Maintaining cybersecurity is necessary for smooth business operations, and good response and recovery planning can help to minimize the risk.
References
[1] WIREs Data Mining Knowl Discov 2017, e1211. doi: 10.1002/widm.1211 [2] Yahoo says 500 million accounts stolen. 2017. Available at: http://money.cnn.com/2016/09/22/technology/yahoo-data-breach/. [3] World’s biggest data breaches. 2017. Available at: http://www.informationisbeautiful.net/visualizations/ worlds-biggest-data-breaches-hacks/. (Accessed March 1, 2017). [4] Identity Theft Resource Center. 2017. Available at: http://www.idtheftcenter.org/. (Accessed March 1, 2017). [5] https://www.cisco.com/c/m/en_sg/partners/cisco-networking-academy/index.html [6] https://www.nibusinessinfo.co.uk/content/impact-cyber-attack-your-business [7] https://www.google.com/amp/s/indianexpress.com/article/explained/explained-how-big-is-the-bigbasket-data-breach-7026688/lite/ [8] https://m.timesofindia.com/business/india-business/upstox-face-data-breach-co-says-ramped-up-security/amp_articleshow/82021166.cms [9] https://www.google.com/amp/s/indianexpress.com/article/technology/tech-news-technology/mobikwik-database-leaked-on-dark-web-company-denies-any- data-breach-7251448/lite/ [10] Ko, M and Dorantes, C. (2006), “The impact of information security breaches on financial performance of the breached firms: an empirical investigation”, Journal of Information Technology Management, Vol. XVII, pp, 13-22. [11] Ahmad, H. and Alnsour, Y. (2019), “The effect of data breaches on company performance”, International journal of Accounting & Information Management, Vol. 28No. 2, pp. 275-301. [12] 2016 cost of data breach study: global analysis. 2017. Available at: https://www-03.ibm.com/security/databreach. [13] Data breach investigations report. 2017. Available at: https://en.wikipedia.org/wiki/United_States_diplomatic_cables_leak. [14] Hunton, J., Lippincott, B. and Reck, J. L.(2003), \"Enterprise resource planning systems: comparing firm performance of adopters and nonadopters,\" International Journal of Accounting Information Systems, Vol. 4, Number 3, pp. 165-184. [15] Ahmad, A., Maynard, S.B. and Shanks, G. (2015), “A case analysis of information systems and security incident responses”, International Journal of Information Management, Vol. 35 No. 6, pp. 717-723. [16] Beaver, W.H. (1966), “Financial ratios as predictors of failure”, Journal of Accounting Research, Vol. 4, pp. 71-111.
Copyright
Copyright © 2022 Rakesh Kumar Ray, Rahul Kumar Sinha, Tinganiwar Akhilesh Kumar. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET45819
Publish Date : 2022-07-20
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

