Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
To Survey Graphical Password Verification Method
Authors: Khusboo Shrivastava, Harish Sahu
DOI Link: https://doi.org/10.22214/ijraset.2022.47855
Certificate: View Certificate
Abstract
In this present time, authentication is the way of giving persons access to system object based on user\'s uniqueness. If the codes match, the process will be succeed and user will get the consent to access the system. Text based password scheme follows the guidelines such as at least 8 characters long, should combine upper-case and lower-case and digit. user have problem to remember their complicated password over time due to the limitation of human brain, user tend to forget about their password. User tend to use the same password for all type of account. So if one account is hacked, the possibility for other account to be hack is a high. Graphical password can be used as alternative to solve the issue related to the text-based authentication based on the fact that humans can tend to remember pictures batter then text. Now a day’s many computer system, Network and internet based environment are trying to use of graphical authentication technique in this paper we make a survey of the basic authentication and its technique and also presents a comprehensive study of graphical password authentication method and graphical password system.
Introduction
I. INTRODUCTION
A password authentication system allows user choice while influencing users toward stronger password identify that there are three major Areas where human computer interaction is important authentication, security operation and the developing secure system. Alphanumeric password where first presented in the 1960 as a result to security issues for first multiuser operating system. An alphanumeric password is only a sequence of letters and digits. Graphical password consist of choosing images or drawing symbol rather than entering textual character It was first described by Greg Blonder in 1996. Physiological studies have shown that people can remember pictures better than text human brain is capable of processing and storing large volume of graphical information with easiness…while it is very tough to recall a string of fifty characters, humans are capable easy to recall faces of people places we visited and things.
A. Graphical Password Authentication Methods
Token based authentication method
- Biometric based authentication method
- Knowledge based authentication method
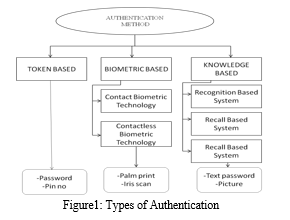
- Token Based Authentication
Token based techniques, like key cards, bank cards and smart cards are mostly used. Token based authentication systems also use knowledge based techniques to upgrade security, for example: ATM cards are generally used together with a PIN number.
2. Biometric Based Authentication
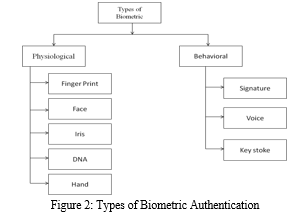
Biometric based authentication techniques, such as a fingerprints, iris scan, or facial recognition, are not yet broadly accepted. the main drawback of this scheme is that such systems can be costly, and the identification system can be slow and often unreliable. However, this type of technique provide the uppermost level of security.
3. Knowledge Based Authentication
knowledge based authentication method are the further most broadly used authentication techniques and include both text-based and picture-based password the picture based techniques can be further divided into two system:-recognition based authentication system and recall based the graphical authentication system knowledge based authentication method shared secret key which is used in banks, financial institutions, internet service provider and email services provider like Gmail, Yahoo mail etc.
a. Recognition based technique: Dhamija and Perring advised a graphical authentication technique established on the Hash visualization scheme in their method the user is asked to select a certain number of pictures from a set of random images generated by a program later the user will be required to identify the preselected images in order to be authenticated. A weakness of this system is that the server needs to store the seeds of the portfolio images of each user in plain tab text.
b. Recall based techniques: In the recall based techniques user need to recall or remember the particular images or drawing which he or she has already generated in the phase of registration. There are lot of techniques provided for recall based scheme. Here we have selected a scheme proposed by Jemyn called Draw-A- Secret (DAS) for our analysis. in this scheme user need to design a picture or signature on a 2D grid. The coordinate occupied by the picture drawn by user are stored in the order of drawing. In the authentication process user need to redraw the same picture. If the picture touches the same grid, then the user is authenticated.
II. LITERATURE REVIEW
These including a few article and journal that related directly and indirectly to the secure graphical password system and also describe about the related research that is review for graphical password authentication which are being proposed. All this survey was described, summarized, evaluated and clarified.
|
S.No |
Proposal/Author |
Year |
Objective |
Trust |
Accuracy |
Techniques |
|
1 |
G.E. Blonder |
1996 |
Single image based schemes |
ü |
ü |
Graphical password schemes |
|
2 |
Greg. E. Blonder |
1996 |
Database consist of predefined images which will be displayed to the user has to top region of interest as to set the password |
ü
|
ü
|
Cued recall based technique
|
|
3 |
Brostoff |
2000 |
User have to chose four faces as a password from 3×3 matrix[Passface Scheme] |
ü |
ü |
Recognition based technique
|
|
4 |
Dhamiya and Perrig |
2000 |
Users have to choose a random image from a set of images |
ü |
ü |
Recognition based technique
|
|
5 |
Jensen |
2003 |
User has to select image of size 40×40 from a 5×5 matrix[Picture Password Scheme] |
ü |
ü |
Recognition based technique
|
|
6 |
Tharpe and vanoorschot |
2004 |
Allow user to create free-hand drawing as a password |
ü |
ü |
Pre recall based technique[Graphical Password Scheme] |
|
7 |
Varenhorst |
2004 |
Allow user to create free-hand drawing as a password |
ü
|
ü
|
Pre recall based technique[Passdoodle] |
|
8 |
G.E. Blonder
|
2005 |
By Eliminating the pre define boundaries and allowing arbitrary images |
ü
|
ü
|
Passpoint Method
|
|
9 |
Sobardo and Birget |
2006 |
User chooses these pass-object and click inside of a convex formed by the pass objects |
ü
|
ü
|
Recognition based technique[Shoulder Surfing Problem]
|
|
10 |
BDAS
|
2007 |
User’s choice depends on various characteristics of image |
ü
|
ü
|
Cued recall based technique
|
|
11 |
Chiasson[Cued Click Points] |
2007 |
Location of the click point of the current image the next image is displayed |
ü
|
ü
|
Cued recall based technique |
|
12 |
Chissaon |
2007 |
Includes persuasive features to cued click point |
ü |
ü |
Cued recall based technique
|
|
13 |
Thao and LI |
2007 |
It provide features of both textual as well as Graphical Password |
ü |
ü
|
Hybrid based technique
|
|
14 |
Jermyn |
2009 |
User have to draw a password on a 2D grid using stylus or mouse |
ü |
ü |
Pre recall based technique[“Draw-A-Secret”][DAS] |
|
15 |
Samaneh Farmand[Syakri Algorithm] |
2009 |
User is authenticated by drawing their signature with the help of a mouse of stylus |
ü
|
ü
|
Pre recall based technique |
|
16 |
Jiminy
|
2011 |
User are provided an image as a reminder to choose Graphical Password that are easy to remember |
ü |
ü |
Hybrid based technique |
|
17 |
H. Gao [Uses CAPTCHA => Completed automated public training Turning test to tell computer and humans apart] |
2011 |
Provides features of both Graphical Password scheme as well as CAPTCHA technology |
ü
|
ü
|
Hybrid based technique
|
|
18 |
H. Gao |
2011 |
Passhands is a combination of Recognition based and Palm based Biometric technique |
ü
|
ü
|
Hybrid based technique
|
|
19 |
Shraddha M.Gurav, Leena S.Gawade |
2014 |
Graphical Password Authentication |
ü
|
ü
|
Cloud Securing Scheme |
|
20 |
Weiss |
2015 |
Geometric Shapes are generated on basis of the combination of eight strokes |
ü
|
ü
|
Pre recall based technique[Pass shapes]
|
|
21 |
Abhilash M Joshi, Balachandra Muniyal |
2018 |
On selection of strict sequence of the image,a two digit number is shown |
ü
|
ü
|
Authentication using text and Graphical Password |
|
22 |
Istanbul,Turkey |
2020 |
Graphical password with strong password space and usability stude |
ü
|
ü
|
CAPTCHA-Based Technique |
|
23 |
Jouraj khadadadi, Yashar Javadianasl Faranak Rabiei, M.Alizadeh |
2021 |
A novel graphical password authentication Scheme with improved usability |
ü
|
ü
|
Recognition-based graphical password |
Conclusion
In this survey,I have focused an comprehensive study of current Graphical Password Techniques, Different techniques from recognition based, Cued recall based and Hybrid schemes of Graphical Password Techniques are observed and reviewed.Though the main consultation for graphical based password is that people are better at remembering picture password than text based passwords, our fundamental analysis proposes that it is very complicated to break graphical password using various method. Therefore, it can be concluded that, we need our authentication system to be more reliable robust and Secure as there is always a place for improvement. my primary analysis justify that it is harder to break graphical password using the traditional attack approaches such as brute force search, dictionary attack or spyware. much more research and user studies are needed for graphical password technique to reach higher levels of capability and cooperation.
References
[1] Dec 2009, H. Gao proposed paper on “graphical password scheme using color login”. [2] In May 2011, M. Sreelatha proposed Hybrid Textual Authentication Scheme. [3] Er. Aman Kumar, Er. Naveen Bilandi, Department of Computer Science and Engineering, DAV University, Jalandhar, Punjab, India “Graphical Password Based Authentication Based System for Mobile Systems”. [4] Miss.Swati Tidke, Miss Nagama Khan, Miss.Swati Balpande Computer Engineering, RTM nagpur university, M.I.E.T Bhandara, “Password Authentication Using Text and Colors”. [5] Veena Rathanavel, Swati Mali, Student M. Tech, Department of Computer Engineering, K J Somaiya, College of Engineering Mumbai, “Graphical Password as an OTP”. [6] Veena Rathanavel, Swati Mali, Student M. Tech, Department of Computer Engineering, K J Somaiya, College of Engineering Mumbai, “Graphical Password as an OTP”. [7] In 2017 Aayush Dilipkumar Jain, Ramkrishna Khetan Krishnakant Dubey, Prof. Harshali Rambade K. Elissa, Department of Information Technology Vidyalankar Institute of Technology, Mumbai, “Color Shuffling Password Based Authentication”. [8] Harsh Kumar Sarohi, Farhat Ullah Khan, “Graphical Password Authentication Schemes: Current Status and Current Issues,” IJCSI International Journal of Computer Science Issues, Vol. 10, Issue 2, No 1, March 2013. [9] “Graphical Passwords: A Survey” by Xiaoyuan Suo, Ying Zhu, G. Scott. Owen. [10] R. Dhamija and A. Perrig. “Déjà vu: A User Study Using Images for Authentication”, In Proceedings of the USENIX Security Symposium, 2000. [11] I. Jermyn, A. Mayer, F. Monrose. M. K. Reiter and A. D. Rubin, “The Design and Analysis of GraphicalPasswords”, In Proceedings of the 8th USENIX Security Symposium, 1999. [12] G. Blonder, “Graphical Password”, In Lucent Technologies, Inc., M urray Hill, NJ, United States Patent 5559961, 1996. [13] Passlogix http://www.passlogix.com, Accessed on February 2007. [11] S. Wiedenbeck, J. Waters, J. C. Birget, A. Brodskiy, and N. Memon, “Authentication Using Graphical Passwords: Basic Results”, In Human-Computer Interaction International (HCII 2005), Las Vegas, NV, 2005. [14] W. Jansen, S. Gavrila, V. Korolev, R. Ayers, and R. Swanstrom, \"Picture Password: A Visual Login Technique for Mobile Devices,\" National Institute of Standards and Technology Interagency Report NISTIR 7030, 2003. [15] Real User Corporation, Passfaces TM http://www.realuser.com, Accessed on January 2007.
Copyright
Copyright © 2022 Khusboo Shrivastava, Harish Sahu . This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET47855
Publish Date : 2022-12-03
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

