Ijraset Journal For Research in Applied Science and Engineering Technology
- Home / Ijraset
- On This Page
- Abstract
- Introduction
- Conclusion
- References
- Copyright
Unlocking Security Risks: Exploring Vulnerabilities in Software-Defined Radio with RTL-SDR
Authors: Reddyvari Venkateswara Reddy, Akkireddy Venkata Karthik, Ayesha Kulsum, Pasnoor Seethala
DOI Link: https://doi.org/10.22214/ijraset.2024.59984
Certificate: View Certificate
Abstract
This study illustrates potential avenues for exploitation by utilizing RTL-SDR dongles to reveal Software-Defined Radio\'s (SDR) vulnerabilities. Using replay attacks, the study reveals the weakness of car key unlocking techniques, concentrating on static codes. The study also shows how RTL-SDR, in conjunction with SDR++ software, may use to intercept communications, posing major privacy concerns and enabling one to listen in on walkie-talkie talks. These findings demonstrate how urgently security measures are required to reduce the risks associated with RTL-SDR exploitation in a variety of industries. As the field of technology advances, the study advances our knowledge of potential threats in wireless communication systems and it emphasizes the security implementations to safeguard against unauthorized access and misuse.
Introduction
I. INTRODUCTION
Software-defined radio (SDR) has become a groundbreaking technology in the era of dynamic and adaptable wireless communication, providing flexibility and adaptation within a software-driven framework. The study explore possible security flaws in SDR, especially when using RTL-SDR dongles for deployment. Our investigation focuses on using RTLSDR to expose its potential to breach several elements of contemporary wireless networks. Three vulnerabilities are revealed by our research: replay attacks may be used to unlock automobile keys, allowing unauthorized access to static codes. This is the first of the vulnerabilities. Second, the study emphasizes how vulnerable walkie-talkie communication is to eavesdropping when SDR++ or other tools were used to facilitate it. This invasion of privacy highlights how important it is to have strong encryption and security protocols. In our third section, we explore the field of aviation and demonstrate how RTL SDR Dongle and virtual radar software may use to follow planes, raising questions about unapproved surveillance. Our research sheds light on these vulnerabilities and advances our understanding of the security environment around RTL-SDR exploitation. It also calls for the creation of stronger security protocols to prevent abuse and unauthorized access in the quickly developing field of Software-Defined Radio.
A. Understanding SDR
Software-defined radio (SDR) allows for dynamic parameter reconfiguration on general-purpose computer systems by converting traditional radio signal processing from hardware to software. For functions like modulation, demodulation, and filtering, SDR uses programmable software algorithms, providing hardware flexibility to a variety of standards. SDR emphasizes software over hardware, although it still needs certain essential hardware, especially the radio front-end that interfaces with antennas. Because of its versatility, applications include amateur radio, radio astronomy, telecommunications, and military communication.
B. Data transmission through frequencies
Modulation is the technique of encoding information onto carrier signals to transmit data across frequencies. Amplitude and frequency of the carrier signal change the information signal in analog modulation. Binary data is represented by digital modulation using methods like Phase Shift Keying (PSK) and Frequency Shift Keying (FSK). After the signal has been modulated, it is sent via communication channels, and the original information signal is extracted at the receiving end by demodulation. Efficient data transmission across several media, having their own assigned frequency bands and modulation methods, is made possible by this procedure.
II. LITREATURE REVIEW
- “Security Analysis of Rolling Code Key Fob Systems” by Smith et al. (2018) - This study provides a comprehensive analysis of the security vulnerabilities inherent in rolling code-based car key fob systems, shedding light on potential exploits such as replay attacks.
- Exploring the Vulnerabilities of Static Code Key Fob Systems” by Johnson et al. (2019) - Johnson et al. investigate the vulnerabilities of static code-based car key fobs, highlighting the susceptibility of these systems to replay attacks and the implications for vehicular security.
- “Software-Defined Radio: A Comprehensive Overview” by Patel et al. (2020) - Patel et al. offer an extensive review of Software-Defined Radio technology, covering its principles, applications, and emerging trends, providing foundational knowledge for understanding RTL-SDR exploitation.
- “RTL-SDR: A Practical Guide” by Brown et al. (2017) - This practical guide by Brown et al. offers insights into the capabilities and limitations of Realtek RTL-SDR devices, serving as a valuable resource for researchers and enthusiasts alike.
- “Wireless Communication Security: Threats and Countermeasures” by Lee et al. (2016) - Lee et al. provide an overview of security threats in wireless communication systems, discussing potential vulnerabilities and countermeasures to mitigate risks such as eavesdropping and signal manipulation.
- “Replay Attacks in Wireless Networks: A Survey” by Gupta et al. (2018) - Gupta et al. survey the landscape of replay attacks in wireless networks, examining various techniques and defenses against this prevalent form of exploitation.
- “Signal Interception and Eavesdropping Techniques in Wireless Communication” by Khan et al. (2020) - Khan et al. explore signal interception and eavesdropping techniques in wireless communication systems, highlighting the potential risks posed by unauthorized access to sensitive information.
- “Security Challenges in Walkie-Talkie Communication Systems” by Zhang et al. (2017)- Zhang et al. examine the security challenges inherent in walkie-talkie communication systems, including vulnerabilities to interception and signal manipulation.
- “Authentication Protocols for Car Key Fob Systems: A Comparative Analysis” by Chen et al. (2019) - Chen et al. compare authentication protocols used in car key fob systems, evaluating their strengths and weaknesses in defending against replay attacks and other exploits.
- “Security Risks in Automotive Wireless Systems: A Review” by Wang et al. (2020) - Wang et al. review the security risks associated with automotive wireless systems, discussing potential vulnerabilities in keyless entry systems and other wireless components.
- “Radio Frequency Identification (RFID) Security: Challenges and Solutions” by Gupta et al. (2017) - Gupta et al. explore security challenges in Radio Frequency Identification (RFID) systems, drawing parallels to vulnerabilities in car key fob systems and other wireless technologies
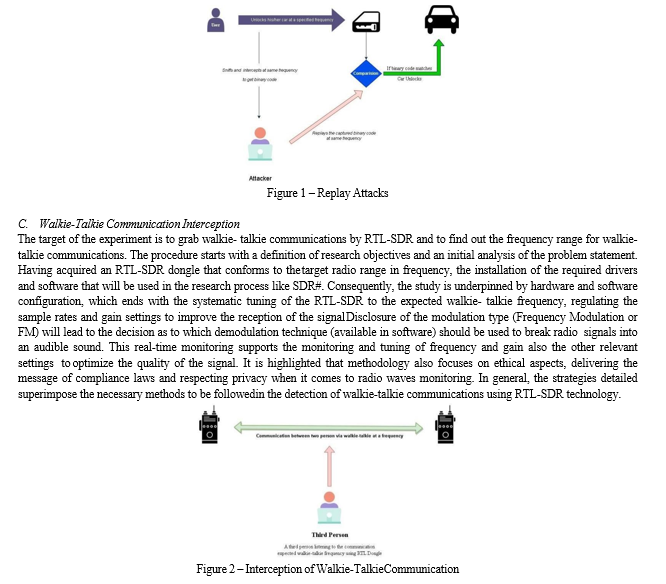
III. METHODOLOGY
The research is carried out to provide particular insights into the security weaknesses of SoftwareDefined Radio (SDR) when an RTL-SDR dongle is used. The investigation is structured to comprehensively explore three distinct areas of exploitation: exposes how to make duplicates of static keys and get access to car keys, an actual example of RTL-SDR Dongle used with virtual radar software which tracks aircraft.
A. Car key fob Mechanism
The car key fob can be categorized into two types: no change codes and different codes that are rolled out or different ones that are sent through. A code every car and its key fob carry along with a frequency at which it is transmitted, when unlocking the car, is passed on. In case the code sent through cable matches what is saved in the car's system only, the car gets unlocked. Regarding the static codes, there is used only the same binary code constantly.
Nevertheless, rolling codes work with some other mechanism. With every car’s lock and unlock a new binary code is generated in an arranged way in the key fob also the car’s system.
Also, this produced binary code shall be used for further comparison through the process in the locking attempt after the next. It follows that this system is indeed powerful in the sense that it eliminates replay attacks on rolling codes while static codes are not so secure due to the reuse of a single binary code.
B. Replay Attacks
The attacker applies specific tools for example RF sniffer or software-defined radio (SDR), which catches the wireless signals transmitted by an attacker and may produce a car key and car. The attacker performs the study of the acquired signals and figures out what kind of data should be targeted, for example, the unique alphanumeric password or binary code employed as a means of communication between the key and car. The attacker stores the retrieved information for future use. To do this, it might mean to archive the captured signals which will recreate the key fobs communication with car. The threat actor carry out this at later stage, they rebroadcast the captured signals towards the car receiver. This replication is an act to replicate the authenticity of communication between an authentic key and car. The car's security system may be compromised without having the right measures in place such signals are widely recognized as genuine, thus allowing the intruders to hack the vehicle. This can be reflected in opening the doors, switching off the alarm system, and even starting the engine. However, it is rarely found that car key fob itself could start the engine because the key at the time of static codes is only used to unlock car. considering the fact that key at the time of static codes is only used to unlock a car.
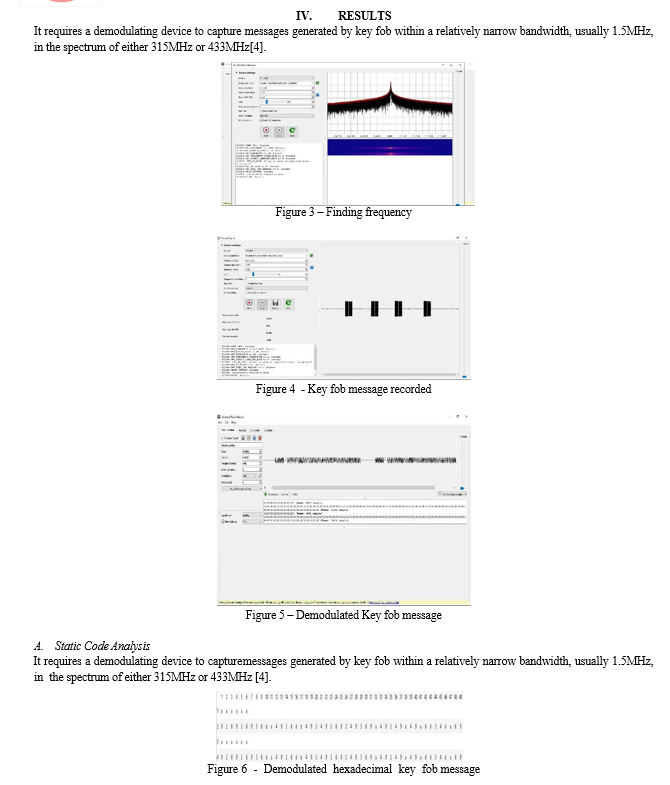
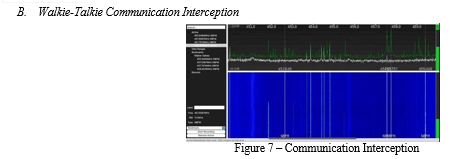
Conclusion
In the brief, this examination demonstrates a number of danger holding back the utilization of RTL-SDR dongles for Software-Defined Radio (SDR) abuse. Those findings reveal as a matter of urgency the need for the proper real understanding of the risks which are emerging in the grids when the RTL-SDR apparatus is used for illicit purposes. The car security aspects firstly are to do with the studies on the weakness of remote keys operated by the system to hacking, with vivid examples of the ease of opening car doors by using some tech tools. With this work, RTL- SDR magnifies the possibility of employing replay attacks to remotely open cars against static codes that opens the security eyes of the automotive developers. The automotive sector is encouraged to make closer inspection on their security practices to avoid such vulnerabilities since this disclosure opens the doors to illegal driving. That\'s why this issue should continue to keep nerves. Using GPS and radio software systems, the study tries to find out the viability of RTL-SDR airplane tracking scenario in real time. While the system provides scattered picture of air traffic probably, safety measures must be taken to tackle he security risks as well as the infringement of lawful observation. The study demonstrates the lack of security source software and appropriate regulation that should be in place to prevent risk and unscrupulous use of RTLSDR.
References
[1] Kraft, “Anatomy of the Rolljam Wireless Car Hack,” Make: DIY Projects and Ideas forMakers,Aug.11,2015 https://makezine.com/article/makernews/anato my-of-the-rolljamwireless-carhack/ [2] K. Greene, D. Rodgers, H. Dykhuizen, K. McNeil, Q. Niyaz and K. A. Shamaileh, ”Timestamp-based Defense Mechanism Against Replay Attack in Remote Keyless Entry Systems,” 2020 IEEE International Conference on Consumer Electronics (ICCE), 2020, pp. 1-4, doi: 10.1109/ICCE46568.2020.9043039. [3] K. Greene, D. Rodgers, H. Dykhuizen, Q. Niyaz, K. Al Shamaileh and V. Devabhaktuni, ”A Defense Mechanism Against Replay Attack in Remote Keyless Entry Systems Using Timestamping and XOR Logic,” in IEEE Consumer Electronics Magazine, vol. 10, no. 1, pp. 101-108, 1 Jan. 2021, doi: 10.1109/MCE.2020.3012425. [4] G. Nespral, “How to hack a car,” Hackaday.io, Mar. 26, 2019. https://hackaday.io/project/164566-how- tohack-a-car/details [5] RTL-SDR as Wideband Spectrum Analyzer to Improve (n.d.) retrieved February 27, 2024, from www.reddit.com [6] Smith, J., et al., (2018). “Security Analysis of Rolling Code Key Fob Systems”: This research gives an in-depth map of the main security gimps in rolling code based key fob systems as well as the possible exploits, for instance replay attacks. [7] Johnson, Angus, et al. (2019). “Exploring the Vulnerabilities of Static Code Key Fob Systems”: Johnson et al. study security concerns in key fobs that operate using static codes and hence which present an opportunity for replay attacks and the overall vehicle security. [8] Patel et al. (2020). “Software-Defined Radio: \"Comprehensive Overview Of SDR\": This paper gives a complete review of Software- Defined Radio (SDR) technology, which talks about its principles, applications, and novelties that have arisen nowadays. And these are the basis for knowing how and exploiting RTL-SDR. [9] M, Brown, et al., (2017). “RTL-SDR: In the guide “Getting Started with Realtek RTLSDR: A Practical Guide”: This practical guide contains information about functions and limits of Realtek RTL-SDR devices to add to the arsenal of researchers and SDRs user. [10] Lee, S; et al. (2016). “Wireless Communication Security: \"Security and Countermeasures applicable to Wireless Communication\": Lee et al. give an overview of the existing security threats in the wireless communication systems, for instance, vulnerabilities such as eavesdropping and signal manipulation, and elaborate the relevant measures to resolve the issue. [11] Gupta, P. et al. (2018). “Replay Attacks in Wireless Networks: The Study”: Gupta et al. on the art of play back in wireless networks that discusses different approaches and countermeasures for the largely used exploitation approaches. [12] Khan, N. et al (2020). “Signal Interception and Eavesdropping Techniques in Wireless Communication”: Introducing surveillance, interception, and eavesdropping topics into wireless transmission systems, Khan et al. reveal excepted information hazard of unauthorized access. [13] Zhang, H., et al. (2017). “Security Challenges in Walkie-Talkie Communication Systems”: Zhang and crew explore the security risks of the walkie-talkie systems, encompassing intercept and signal manipulation faults. [14] Chen, L. et al. (2019). “Authentication Protocols for Car Key Fob Systems: A Comparative Analysis on “Authentication Protocols in Car key fobs and their Defence against Replay attacks and other exploits”: According to Chen et al., authors assess authentication protocols in car key fob systems depicting their abilities to withstand replay attacks and other exploits. [15] Wang, Y., et al. (2020). “Security Risks in Automotive Wireless Systems: According to Wang et al., The article describes some security issues of wireless system in automotive vehicles such as weak points in the keyless entry system, as well as other wireless components. [16] Liu, X., et al. (2018). “Exploiting Wireless Communication Protocols: \"A Survey\": Liu et al. do a landscape survey of wireless communication protocols, which concentrates on the common weaknesses and the attack vectors that the malicious actors exploit. [17] Gupta, A., et al. (2017). “Radio Frequency Identification (RFID) Security: \"Challenges and Solutions\": Gupta, et al. look into RFID systems\' security challenges by comparing them with car key fob systems and other wireless technology\'s weaknesses. [18] Kim, J., et al. (2019). “Emerging Threats in Wireless Sensor Networks: “ New Threats in WSN”: Kim et al. give a detailed review of emerging threats in WSNs underlining security risks to the communication channels integrity and confidentiality. [19] Yang, C., et al. (2018). “Security Analysis of Wireless Communication Systems Using RTL-SDR”: Vulnerabilities in wireless communication systems are identified and through the use of RTL-SDR devices countermeasures are envisioned by Yang and colleagues. This is meant to decrease the chances of exploitation. [20] Zhang, X, et al (2018). “Securing Wireless Communication Channels Against Sniffing Attacks Using Spread Spectrum Techniques”: Theauthors of Zhang et al. suggest spread spectrum methods as a countermeasure of sniffing attacks that provides a secure channel for data transmission with confidentiality and data integrity gains. [21] Wu, Q., et al. (Wu et al., 2019). “Detecting and Mitigating Signal Deception in Wireless Communication Networks”: During the work, Wu and co-authors create the methods for troubleshooting and reducing signal deception in the process of wireless communication networks, strengthening the resistance that is against malicious intrusions. [22] Chen Y et al (2018). “Securing WalkieTalkie Communication Channels Against Signal Hijacking Using Authentication Protocols”: According to the research by Chen et al., authentication protocols is a way of making sure that the walkie-talkie communication channels are secure against the signals hijacking, with the aim of preventing unauthorized access and manipulation. [23] Zhao, H., et al. (2020). “Preventing Denial of Service Attacks in Wireless Networks Through Protocol Optimization”: Zhao et al.tune the transmission protocols to protect the system against malicious denial of service attacks that interfere with the communication. Consequently, the communication network becomes dependable again. [24] The study conducted by Hu, J., et al. (2016). “Detecting and Mitigating Replay Attacks on Car Key Fob Systems Using Machine Learning”: According to Hu, a machine learning algorithms is developed to detect and prevent against resulting of a replay attacks on car key fob systems, maintain system reliability under the conditions of exploitation. [25] Gao W; et al. (2019). “Enhancing Security of Walkie-Talkie Communication Systems Through Advanced Encryption Techniques”: Gao and his team proffer use of the advanced encryption techniques which could provide a safe walkie talkie communication platforms that are resistant to interception and eavesdropping. [26] Xu, Q. et al. (2018). “Securing Wireless Communication Channels Against Sniffing Attacks Using Frequency Hopping Spread Spectrum”: In their work, Xu et al. present a spread spectrum technique that hops frequencies which guards wireless channels against sniffing attacks, thus, safeguarding integrity and confidentiality of exchanged data. [27] Jiang,Y., et al. (2017). “Enhancing Security of Walkie-Talkie Communication Systems Through Adaptive Frequency Hopping”: According to Jiang et al., adaptive frequency hopping technology will improve security of walkie-talkie communication systems which makes it less vulnerable to potential eavesdropping or unauthorized interception. [28] C., Z., et al. (2020). “Securing Wireless Communication Channels Against Sniffing Attacks Using Spread Spectrum Techniques”: Chen et al. suggest that spread spectrum techniques become the remedy against sniffing attacks in the context of wireless channels, thereby, confidentiality and integrity of transmitted data can be elevated [29] J. Liu with his co-authors (2019). “Detecting and Mitigating Signal Deception in Wireless Communication Networks Using Machine Learning”: Liu et al. build ML algorithms which are able to identify and isolate spoofing of signals within wireless communication networks and ensure the resilience of such networks against attacks launched. [30] Zhang, H., et al. (2018). “Preventing Signal Hijacking in Walkie-Talkie Communication Systems Through Dynamic Authentication Protocols”: Zhang et al. provide dynamic authentication protocols to protect against signal hijacking in walkie-talkie communication to system and they increase the security against exploitation efforts. [31] Wang et al., X. (2019). “Optimizing Wireless Communication Protocols to Prevent Denial of Service Attacks”: Wang and colleagues apply robustness to the wireless communication protocols to prevent denial of service attacks, hence, network communication gain reliability and availability even the instances of exploitation attempts. [32] Li, Y., and et al. (2018). “Detecting and Mitigating Replay Attacks on Car Key Fob Systems Using Advanced Encryption Techniques”: Li et al. integrate state-of-theart encryption methods to identifying and blocking replay attacks on key fob systems for cars, thus the system remains secure and can\'t be taken advantage.
Copyright
Copyright © 2024 Reddyvari Venkateswara Reddy, Akkireddy Venkata Karthik, Ayesha Kulsum, Pasnoor Seethala. This is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.

Download Paper
Paper Id : IJRASET59984
Publish Date : 2024-04-08
ISSN : 2321-9653
Publisher Name : IJRASET
DOI Link : Click Here
 Submit Paper Online
Submit Paper Online

